Today’s threat actors are faster, stealthier, and increasingly well-resourced, so your IT/Security team can’t afford to be purely reactive. While tools like firewalls, antivirus software, and intrusion detection systems are essential, they only protect against known threats.
To defend against today’s advanced adversaries and emerging threats, organizations must also embrace proactive strategies – namely, threat intelligence and threat hunting.
These two concepts are often used interchangeably, but they serve distinct purposes. Even more importantly, to drive real impact, they must be operationalized; that is, embedded into your day-to-day security operations with measurable outcomes.
In this blog, we explore what it truly means to operationalize both threat intelligence and threat hunting, how they work together in a feedback loop, and how to distinguish between critical activities like IOC-based threat hunts and behavior-based threat hunts.
Whether you’re building in-house capabilities or evaluating a Managed Detection and Response (MDR) provider, understanding the role that threat intelligence and threat hunting play is essential for building modern, resilient detection and response programs.
Cyber Threat Hunting: A Proactive Approach to Cyber Defense
Threat hunting is the practice of actively searching for signs of compromise or malicious behavior that may have slipped past traditional security controls. Rather than waiting for alerts, hunters work from hypotheses to answer questions like “Is there evidence of lateral movement across critical systems?” or “Are there signs of credential abuse within our cloud infrastructure?”
Effective threat hunting focuses on both indicators of compromise (IOCs), such as known malicious IPs, file hashes, or domains, and attacker behaviors like privilege escalation, command-and-control beaconing, or data exfiltration over uncommon protocols. These behaviors often align with techniques documented in the MITRE ATT&CK framework, providing a structured way to hunt across tactics and techniques used by real-world adversaries.
The primary goals of threat hunting are threefold:
- Identify unknown threats before they escalate into full-scale incidents.
- Enhance detection capabilities for novel threats by feeding insights into new detection content (e.g., SIEM rules, EDR analytics).
- Reduce Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) by enabling faster investigation and containment.
While threat hunting is inherently proactive, it complements reactive security controls by uncovering threats that bypass them. A mature threat hunting program becomes a force multiplier – feeding detection engineering efforts, informing threat intelligence prioritization, and building confidence that your defenses can adapt to evolving threats.
What Does It Mean to Operationalize Cyber Threat Intelligence?
Threat intelligence (TI) is more than just collecting headlines about the latest ransomware gang or downloading a feed of malicious IP addresses. To create real value, threat intelligence must be operationalized. That is, it must be transformed from raw data into actionable insights that inform security decisions, drive detections, and enable response.
There are four common levels of threat intelligence:
- Strategic: High-level trends in the threat landscape, often used by executives for risk planning.
- Tactical: Techniques and tools used by threat actors, often aligned to frameworks like the MITRE ATT&CK framework.
- Operational: Campaign-specific intelligence, such as threat actor infrastructure, malware delivery methods, or TTP patterns.
- Technical: Specific IOCs like file hashes, URLs, IP addresses, and domains.
To operationalize TI, security teams must:
- Ingest and normalize threat intelligence feeds from multiple sources such as commercial, industry-specific, open source, ISACs, and internal telemetry.
- Enrich security alerts and logs with contextual threat information, helping analysts understand whether an alert is noise or a true signal.
- Prioritize and act on intelligence based on relevance to your industry, geolocation, or internal risk posture.
- Integrate intelligence into detection platforms, such as NDR, SIEM, EDR, or SOAR systems, to trigger real-time alerts.
- Enable threat hunts, guiding hunters toward high-value behaviors or IOCs surfaced through intelligence.
Operationalizing TI closes the loop between awareness and action. Instead of being reactive to news of new threats, security teams gain the ability to predict, prevent, and detect those threats with much greater precision and speed.
What Does It Mean to Operationalize Threat Hunting?
If threat intelligence provides the what and where, threat hunting provides the how; how an attacker might be moving through your environment undetected, and how you can find them before damage is done. Operationalizing threat hunting means embedding it into your core security operations, rather than treating it as a one-off or manual effort.
An operationalized threat hunting process includes:
- Hypothesis-driven investigation: Using threat intelligence, recent detection gaps, or changes in the environment to formulate hunt hypotheses.
- Behavioral and anomaly-based analysis: Searching for patterns of activity that deviate from the norm, especially those that suggest adversarial behavior rather than relying solely on known IOCs.
- Threat sweep capabilities: Quickly scoping known IOCs across the environment as a form of lightweight, fast validation.
- Detection engineering handoff: When a hunt surfaces new findings, those are converted into codified detection rules and playbooks.
- Tuning and iteration: Regularly reviewing and updating hunt procedures and detection logic to reflect evolving TTPs and reduce false positives.
By operationalizing hunting, security teams not only detect more sophisticated threats, they also continuously improve the quality and coverage of their detection stack. This cycle is especially critical for MDR providers, who must scale threat hunts across multiple environments while maintaining detection fidelity.
Understanding the Threat Intel and Threat Hunting Loop
Threat intelligence and threat hunting aren’t isolated disciplines. They operate as part of a continuous feedback loop that enhances threat visibility and response over time. Here’s how the cycle typically works:
- Threat intelligence uncovers a new indicator of compromise (IOC) or novel TTP.
- Threat hunters operationalize this data, investigating whether that IOC or behavior exists in the environment.
- Detection engineers convert validated findings into new SIEM rules, EDR detections, or automated SOAR workflows.
- Hunters move on to the next unknown threat, applying lessons learned to new hypotheses.
At eSentire, our Threat Response Unit (TRU) uses an Infinite Loop Threat Framework to gather intelligence, operationalize it to conduct hypothesis-driven threat hunts, and build detections for our team of 24/7 SOC Cyber Analysts:

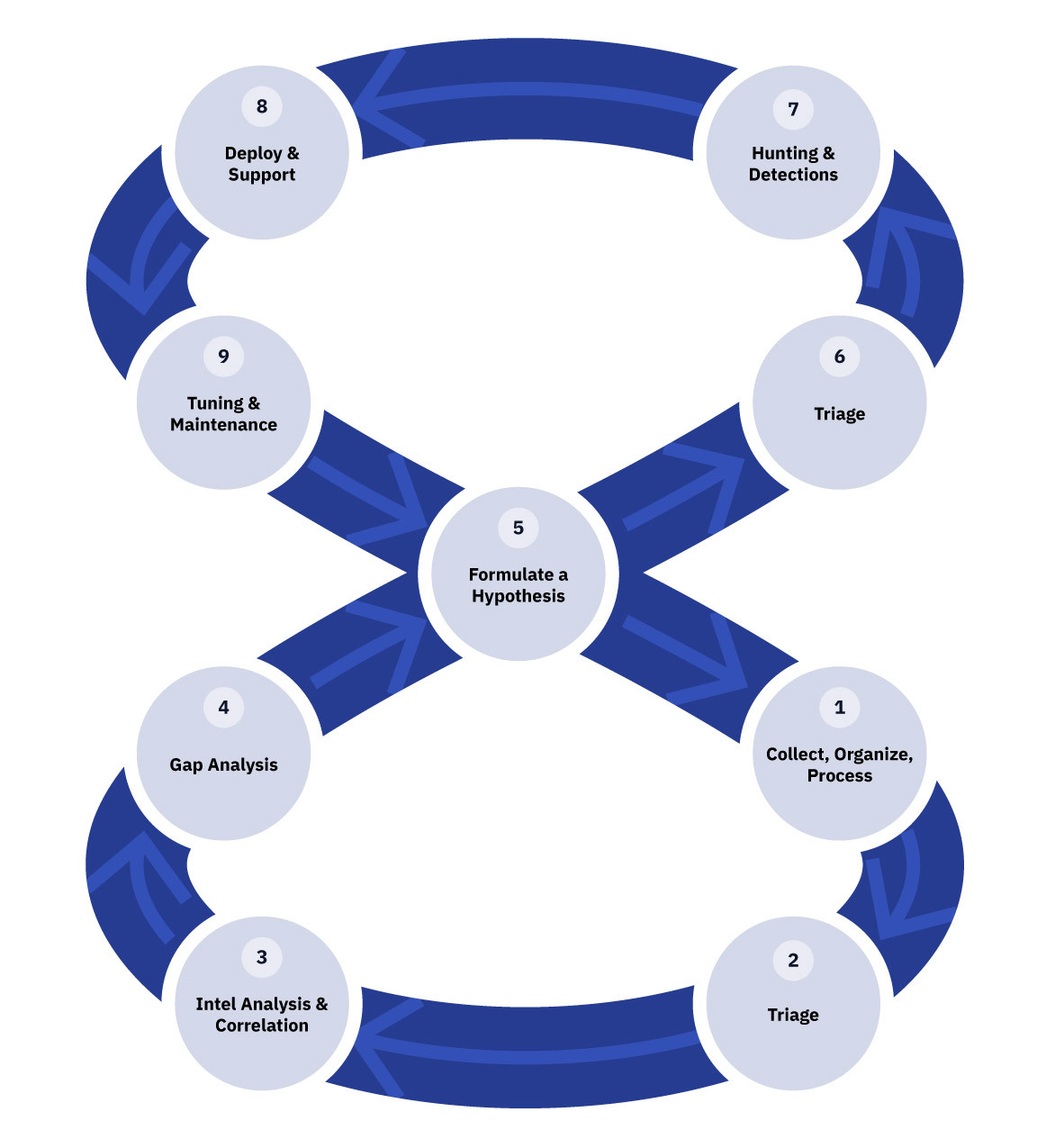
This loop ensures that the environment is constantly being tested, improved, and defended using the most up-to-date threat insights. It turns threat detection into an evolving capability far more agile than traditional, static approaches.
GUIDE
How eSentire Threat Response Unit (TRU) Conducts Proactive Threat Hunting with the Infinite Loop Threat Framework
READ NOWIOC-based Threat Hunts vs. Behavior-based Threat Hunts: A Crucial Distinction
A common misconception is that all hunting is created equal. In reality, there are two distinct approaches:
- IOC-based threat hunts are valuable for validating whether a newly surfaced IOC associated with an emerging threat is present in your environment. Think of them as “spot checks.”
- Behavior-based threat hunts are broader, behavior-focused efforts that seek to uncover stealthy or novel attacks.
|
Feature |
Threat Sweep |
Threat Hunt |
|
Purpose |
Check for known indicators |
Explore for unknown behaviors |
|
Input |
Known IOCs (hashes, IPs) |
Hypotheses based on behaviors or patterns |
|
Scope |
Narrow, fast, confirmatory |
Broad, open-ended, exploratory |
|
Tools |
Query-based scans |
Behavioral analytics, custom scripts |
|
Outcome |
IOC presence/absence |
Potential new detection opportunities |
Both approaches have value, but it’s the combination that enables true threat visibility and resilience.
Detection Engineering: Bridging the Gap Between Intel and Action
None of this works without detection engineering, which is the process of translating threat insights into real-world detection logic. Detection engineers take the outputs of hunts and the inputs from threat intel and turn them into rules, signatures, analytics, response workflows, and new run books for the SOC.
Whether done in-house or through an MDR provider, this role is the connective tissue between proactive research and actionable response. It’s where threat hypotheses become high confidence alerts that SOC analysts can actually use.
For organizations without dedicated detection engineering teams, this is one of the most valuable functions an MDR partner can offer. In 2024 alone, eSentire’s TRU team performed 162,300+ indicator-based threat sweeps and 1,190+ hypothesis-based threat hunts across 2,000+ customers, operationalizing 500+ novel threat detections and runbooks.
Operational Maturity: How Do You Stack Up?
So where does your organization stand?
Here's a quick maturity model to benchmark your progress:
|
Maturity Level |
Threat Intelligence |
Threat Hunting |
|
Reactive |
Consumes threat feeds but no integration |
No structured hunting or tooling |
|
Developing |
Prioritizes and enriches alerts with TI |
Periodic hunts with limited documentation |
|
Operationalized |
Automated TI ingestion, prioritized by context |
Hypothesis-driven hunts, detection feedback loops |
Climbing the maturity curve isn’t just about buying more tools; it’s about aligning your people, processes, and technology to act quickly and decisively when new threats emerge.
In today’s high-stakes threat environment, operationalizing threat intelligence and threat hunting isn’t a nice-to-have – it’s a critical need. When done right, these functions create a dynamic, self-improving detection capability that evolves with the threat landscape.
By investing in the right workflows, tools, and talent – whether in-house or through an MDR provider – you empower your team to move from reactive defense to proactive cyber resilience.
To learn how eSentire’s Threat Response Unit (TRU) can help your organization strengthen your threat detection maturity and operationalize threat intelligence to get ahead of today’s most advanced adversaries, contact an eSentire Security Specialist today.
To learn how your organization can build cyber resilience and prevent business disruption with eSentire’s Next Level MDR, connect with an eSentire Security Specialist now.
GET STARTEDABOUT THE AUTHOR

Mitangi Parekh Content Marketing Director
As the Content Marketing Director, Mitangi Parekh leads content and social media strategy at eSentire, overseeing the development of security-focused content across multiple marketing channels. She has nearly a decade of experience in marketing, with 8 years specializing in cybersecurity marketing. Throughout her time at eSentire, Mitangi has created multiple thought leadership content programs that drive customer acquisition, expand share of voice to drive market presence, and demonstrate eSentire's security expertise. Mitangi holds dual degrees in Biology (BScH) and English (BAH) from Queen's University in Kingston, Ontario.