Adversaries don’t work 9-5 and neither do we. At eSentire, our 24/7 SOCs are staffed with Elite Threat Hunters and Cyber Analysts who hunt, investigate, contain and respond to threats within minutes.
We have discovered some of the most dangerous threats and nation state attacks in our space – including the Kaseya MSP breach and the more_eggs malware.
Our Security Operations Centers are supported with Threat Intelligence, Tactical Threat Response and Advanced Threat Analytics driven by our Threat Response Unit – the TRU team.
In TRU Positives, eSentire’s Threat Response Unit (TRU) provides a summary of a recent threat investigation. We outline how we responded to the confirmed threat and what recommendations we have going forward.
Here’s the latest from our TRU Team…
What did we find?
In May 2025, eSentire's Threat Response Unit (TRU) detected an attack targeting a certified public accounting firm in the United States. The attack utilized a new crypter called “Ghost Crypt” alongside multiple layers of obfuscation to deliver and execute PureRAT malware. PureRAT is a Remote Access Trojan (RAT) malware first observed in Hackforums on January 2023 and has seen a significant surge in infections in 2025.
Initial access was gained through social engineering, where the threat actor impersonated a new client and sent a PDF containing a link to a Zoho WorkDrive folder containing malicious zip files. The attacker also created a sense of urgency by calling the victim and requesting that they extract and execute the file immediately.
The malicious file contained a DLL encrypted with the “Ghost Crypt” crypter, which performed process hypnosis injection of PureRAT into the legitimate Windows binary csc.exe. Figure 1 illustrates the attack flow.
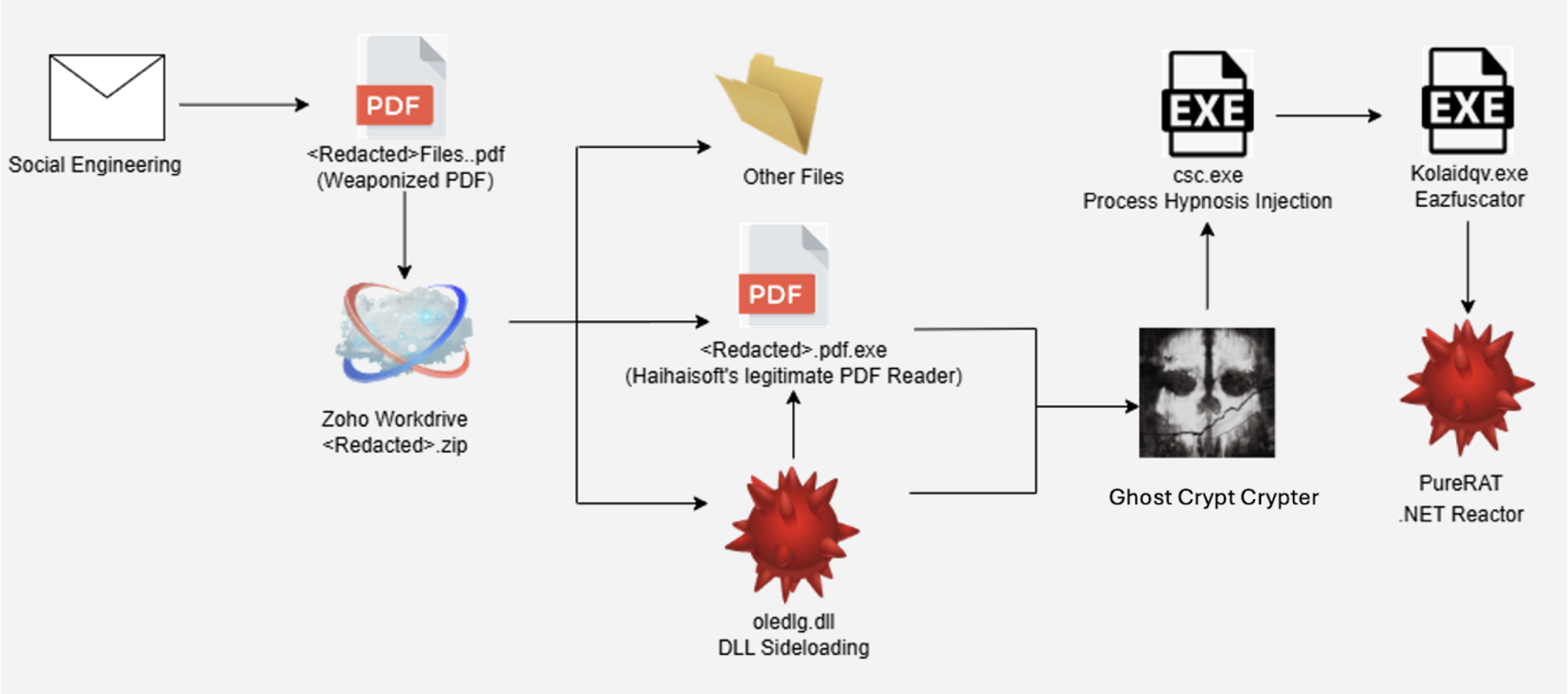
Ghost Crypt Service
As seen in Figure 2, Ghost Crypt was first advertised on hackforums on April 15, 2025, by the user “ghostcrypt” (a new account created in April 2025). The service offers advanced crypting and sideloading capabilities, with support to pack both EXE and DLL files.
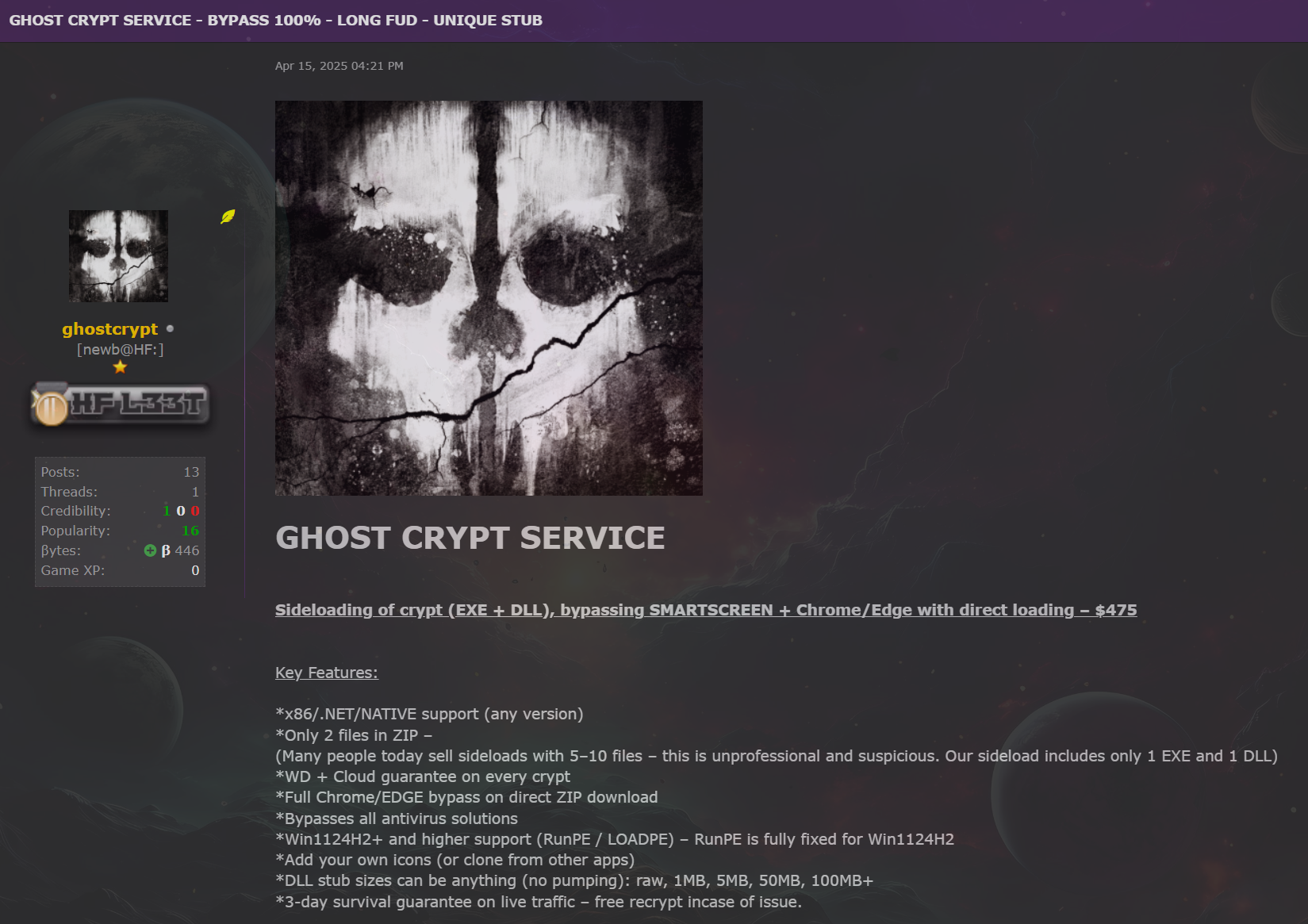
According to the advertisement, Ghost Crypt provides:
- Key features include support for x86, .NET, and native binaries, delivery via a ZIP archive with only two files (one EXE and one DLL), DLL Sideloading and guaranteed bypasses for Windows Defender and cloud-based detections.
- Additional features: Full Chrome/Edge bypass for direct ZIP downloads, claimed bypass of all antivirus solutions, compatibility with Windows 11 24H2 and higher (with updated RunPE/LOADPE support), customizable icons, flexible DLL stub sizes, and a 3-day survival guarantee with free recrypts if issues arise.
- Direct EXE Crypt service is available for $225, offering a 99% polymorphic engine, similar bypass guarantees, and broad support for Windows 11 24H2 and newer. The vendor notes that while most EDRs and AVs can be bypassed, effectiveness depends on the quality of the malware used.
- Supported malware families include LummaC2, BlueLoader, Rhadmanthys, XWorm, DcRat, PureLoader, StealC, and others.
- Kleenscan integration: The service promotes Kleenscan, a tool that allows cybercriminals to test their packed malware against multiple antivirus engines through a user-friendly interface.
![Figure 3 - Kleenscan scan results with 0 hits (hxxps[:]//kleenscan[.]com/scan_result/2d8af5c8db0b34dab78d7e631f25efdec6fafc5d3e33c42b47e97c7abe39b599)](https://esentire-dot-com-assets.s3.amazonaws.com/assetsV3/Blog/Blog-Images/Ghost-Crypt-Powers-image3.png)
Initial Access
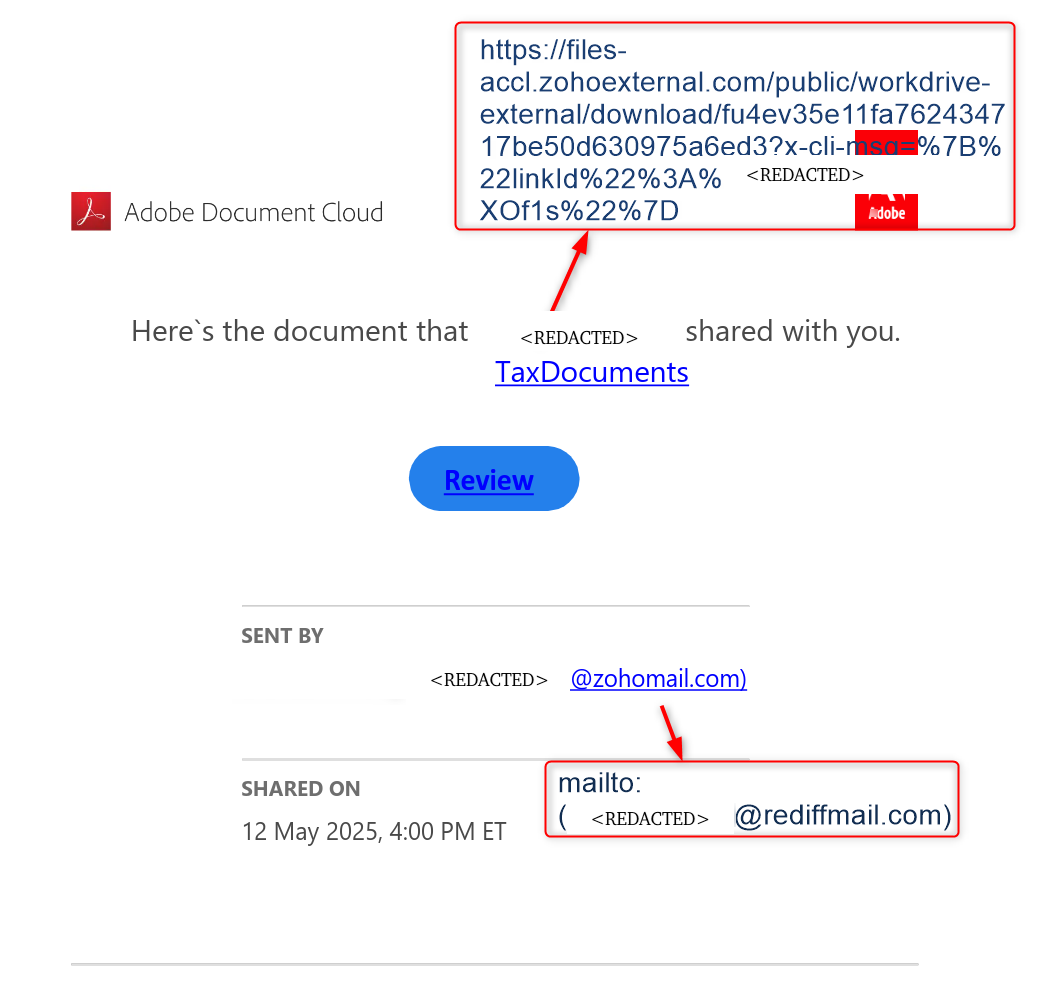
Initial access was achieved when the threat actor, posing as a new client, sent a malicious PDF to the victim (Figure 4). The PDF contains a link to a Zoho WorkDrive URL (zohoexternal[.]com). This URL is part of Zoho’s cloud-based file sharing and collaboration platform, allowing users to securely share and download files over the internet.
When the victim clicked the link, the zip archive was downloaded containing various files such as License copy, tax documents, along with an executable file with a double extension: <filename>.pdf.exe and the malicious DLL.
Visiting that Link Downloads “<Redacted>_File (3).zip” which contains multiple files including Driving License and Tax Document (Figure 5 and Figure 6) potentially to gain credibility.
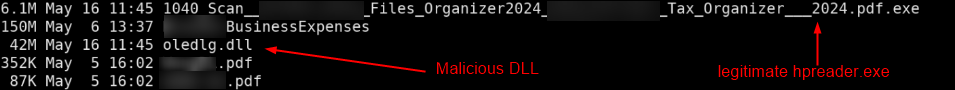
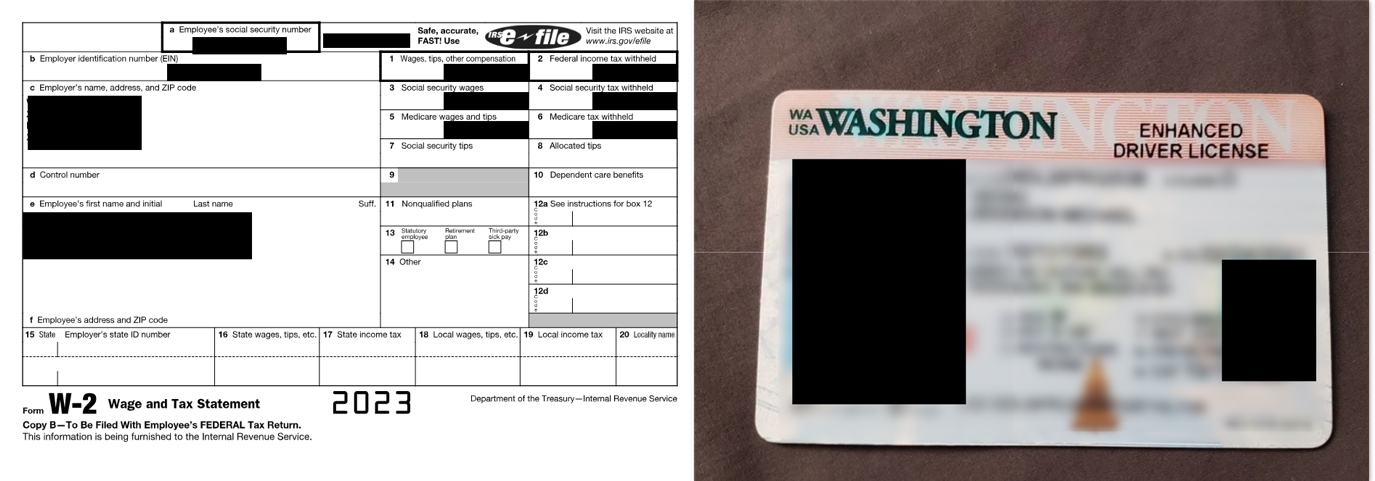
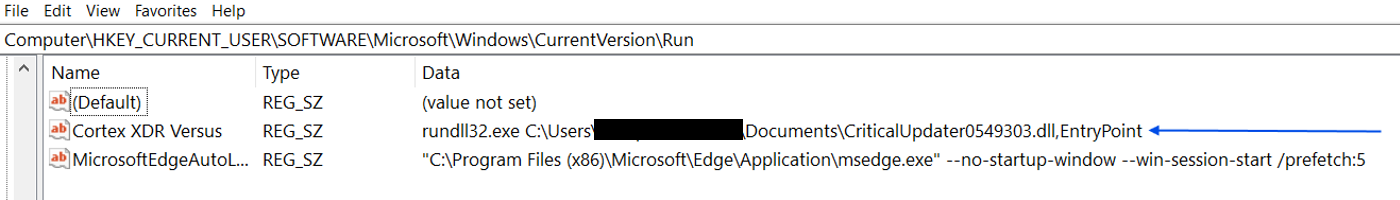
1040_Scan__<Redacted>_Files_Organizer2024_<Redacted>_Tax_Organizer___2024.pdf[.]exe was legitimate file “hpreader.exe” version 1.5.7.0 by “Haihaisoft Limited”. This executable was used to sideload the malicious DLL, which was originally named “oledlg.dll” but had been renamed to “CriticalUpdater0549303.dll”.
To maintain access, the malicious DLL copies itself to “C:\Users\<username>\Documents\” folder and establishes persistence by creating an entry in the Windows Registry Key to ensure DLL is launched each time users log in.
Ghost Crypt Analysis
Ghost Crypt employs a modified ChaCha20 algorithm to decrypt the payload stored in oledlg.dll. This custom implementation differs from standard ChaCha20 in three ways:
- Uses a non-standard magic constant
- Implements a 12-byte null nonce
- Uses a null counter value
- The encryption key is modified by incrementing the fifth double word (DWORD) in each state matrix.

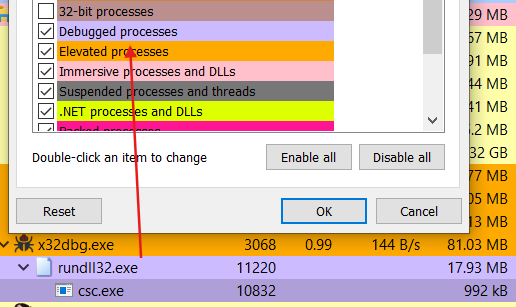
After decrypting the payload, it uses an injection technique known as “Process Hypnosis” beginning by calling the CreateProcessW API with dwCreationFlags set to DEBUG_ONLY_THIS_PROCESS (0x00000002). This flag opens the target process in debug mode, as illustrated in the figure below. This technique effectively prevents debugging the child process as it is already being debugged.
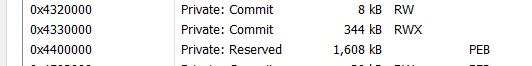
Once the process is running in debug mode, the malware uses VirtualAllocEx to allocate memory within the child process. The memory permissions are then modified using VirtualProtectEx to grant Read, Write, and Execute (RWX) access. As shown in Figure 10, a 344 kB payload is allocated with RWX permissions.
The malware then proceeds to write the PureRAT payload into the victim processes address space using WriteProcessMemory:
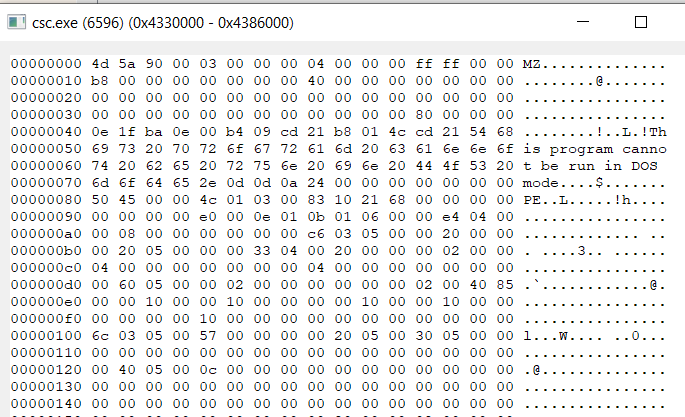
WriteProcessMemory is called once more to patch the ZwManageHotpatch function with 32 bytes of data, a technique highlighted in hasherezade’s blog for bypassing safeguards put in place by Microsoft to prevent process injection on Windows 11 24H2+.
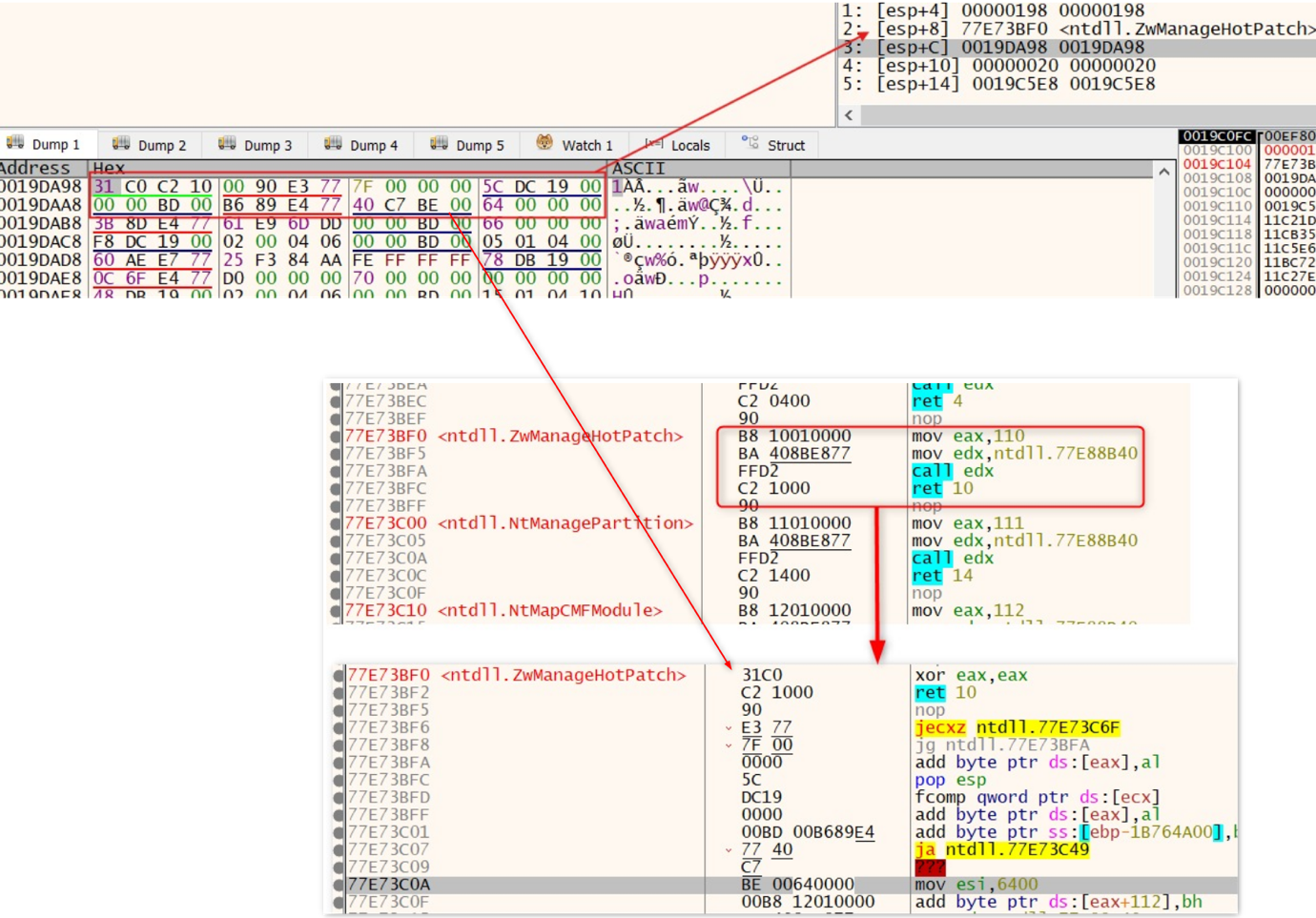
Finally, the malware uses SetThreadContext to update the EAX register, which stores the entrypoint of the main thread, and changes it to point to the PureRAT loader. Lastly, the DebugActiveProcessStop API is called resume execution of PureRAT.
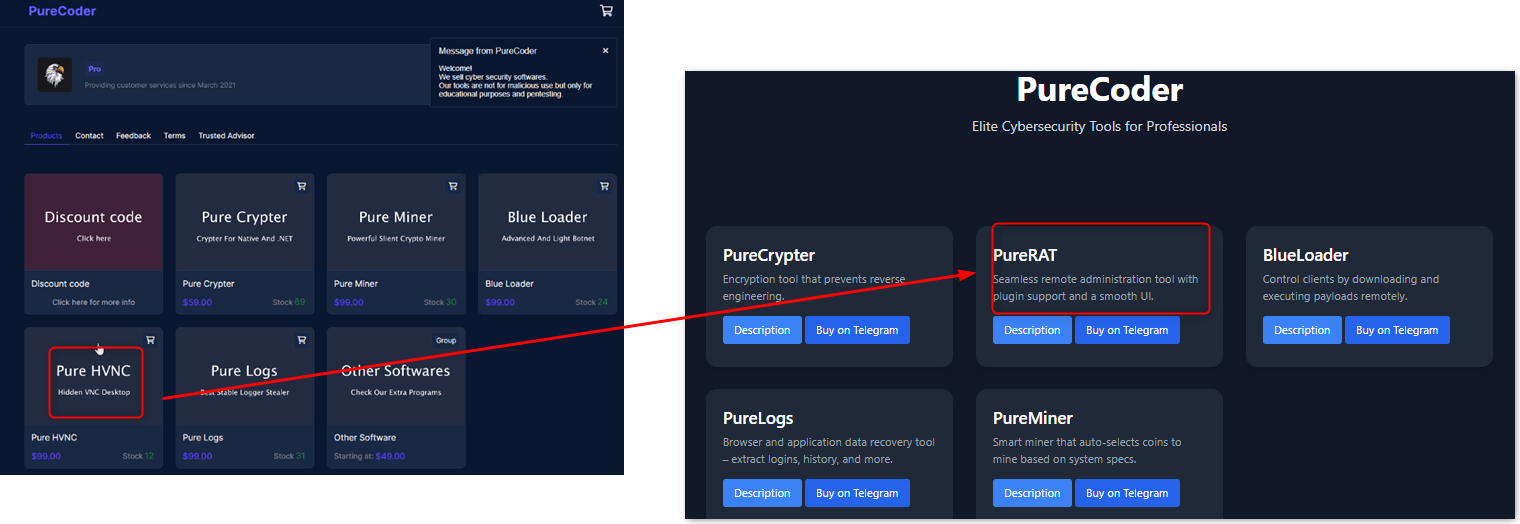
PureCoder, the Seller Behind PureHVNC, Now Focuses on PureRAT
The figure below displays an older screenshot of PureCoder's vendor site compared to the updated site. The older version previously offered PureHVNC, but this product is no longer available for sale. PureCoder has since incorporated PureHVNC's features into PureRAT, which is now their main product offering.
PureRAT Analysis
After dumping the main executable, the next stage involves a binary named “Kolaidqv.exe”. This .NET-based executable is obfuscated using Eazfuscator.NET but can be easily deobfuscated with open-source tooling like EazFixer. A before-and-after comparison can be seen in the figure below, illustrating the effectiveness of using open-source tools for easing the reverse engineering process.
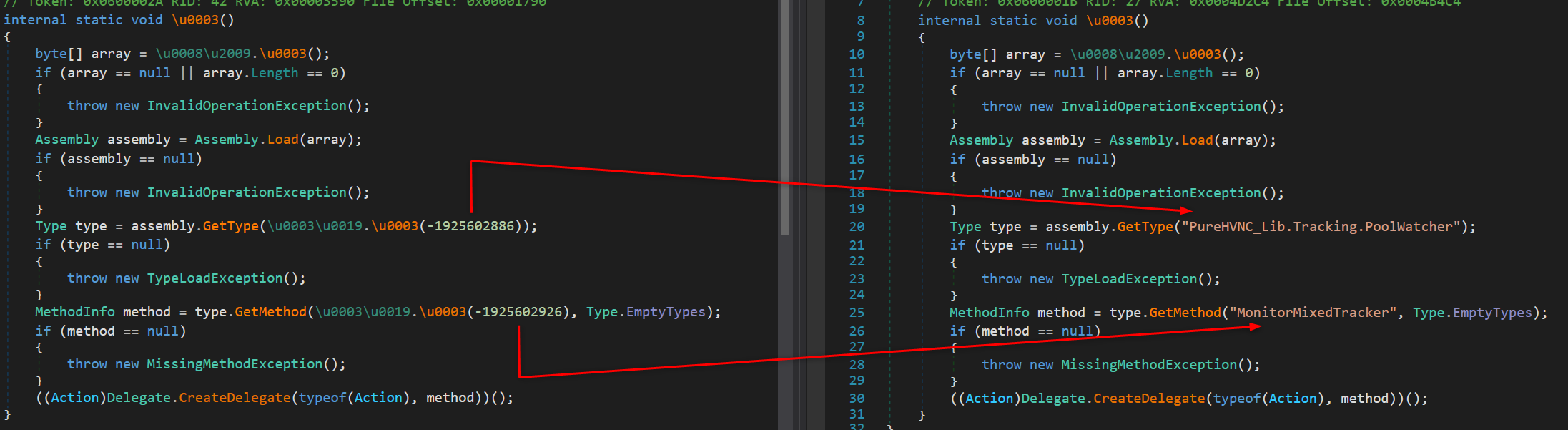
Focusing on the \u0003() method of the \u0008\u2009 class, we observe a series of operations:
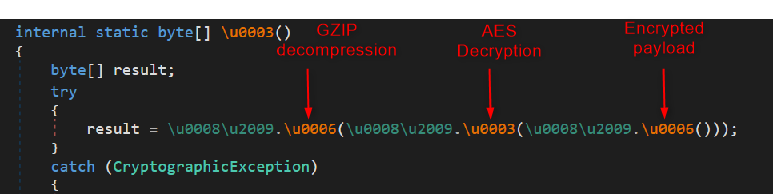
- AES-256 Decryption: It decrypts the payload using AES-256 (see Figure 16 for the decryption code and Figure 17 for the key and IV).
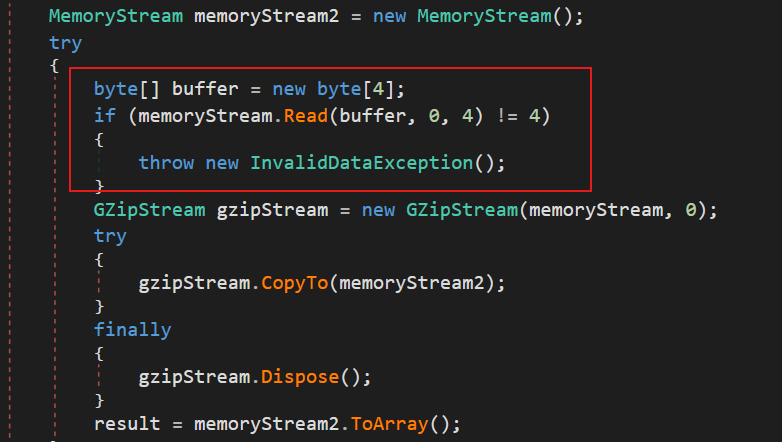
- GZIP Decompression: The code decompresses the payload using the GZIP compression algorithm, as shown in Figure 18.
- Payload Extraction: Before GZIP decompression, the code skips the first 4 bytes (Figure 18).
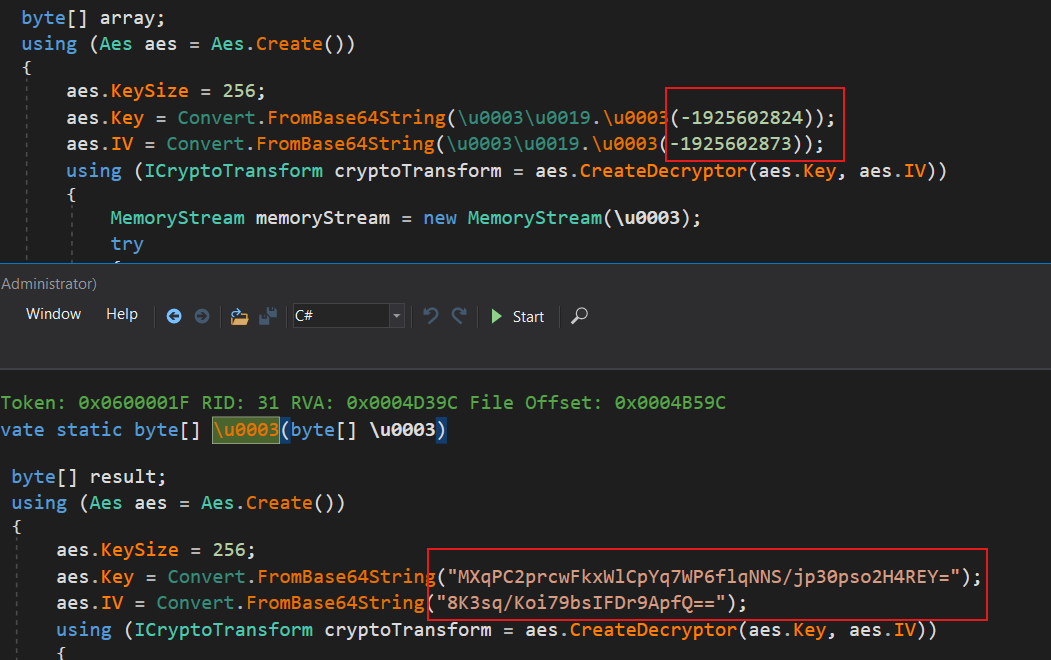
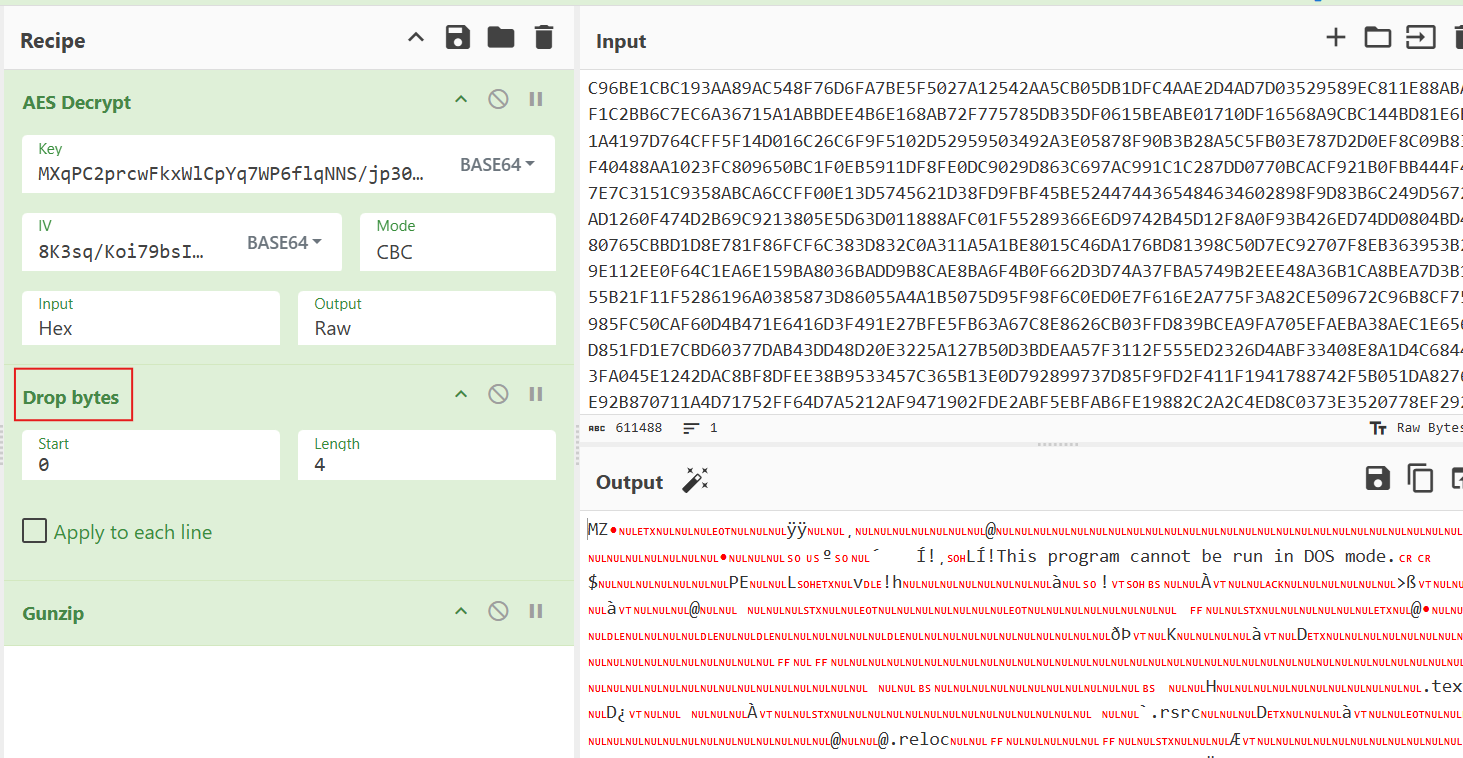
To streamline analysis, we prepared a CyberChef recipe to automate the decryption/decompression process (see CyberChef Figure 19 for the full workflow).
CyberChef Query:
AES_Decrypt({'option':'Base64','string':'MXqPC2prcwFkxWlCpYq7WP6flqNNS/jp30pso2H4REY='},{'option':'Base64','string':'8K3sq/Koi79bsIFDr9ApfQ=='},'CBC','Hex','Raw',{'option':'Hex','string':''},{'option':'Hex','string':''})
Drop_bytes(0,4,false)
Gunzip()
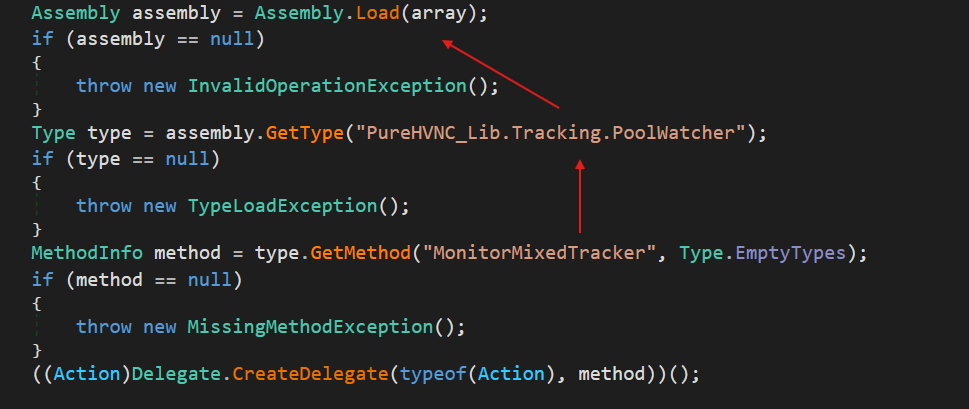
The next stage is another .NET binary, but this time it’s a DLL. Unlike typical malware, this DLL is not executed via rundll32 or regsvr32. Instead, the initial binary contains a hardcoded class and method names, which serve as the entry point for executing the DLL. The DLL is loaded via the Assembly.Load method, the Type/Method for PureRAT are resolved, and the Delegate.CreateDelegate method is called to invoke the method.
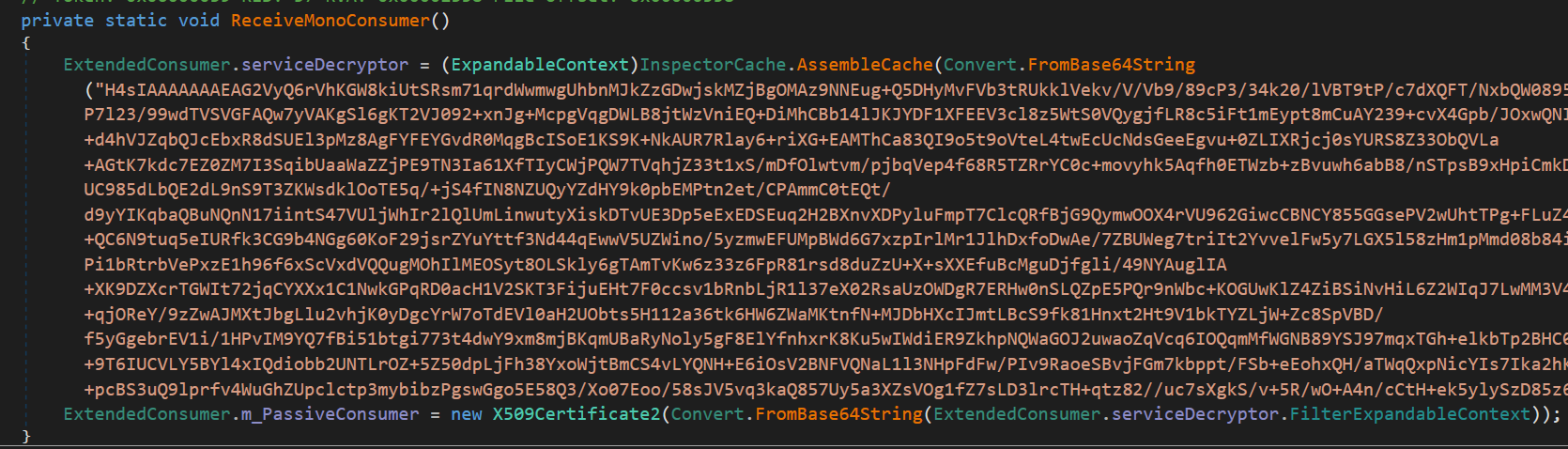
The DLL is packed with .NET Reactor which is common among other malware distributed by PureCoder, and can be unpacked using tools like NetReactorSlayer. Once unpacked, the binary loads and decompresses an embedded GZIP-compressed, base64-encoded payload. This payload is then cast and used to load an X.509 certificate into memory (see Figure 21 and Figure 22 for the embedded certificate, decrypted C2 information, and mutex details).
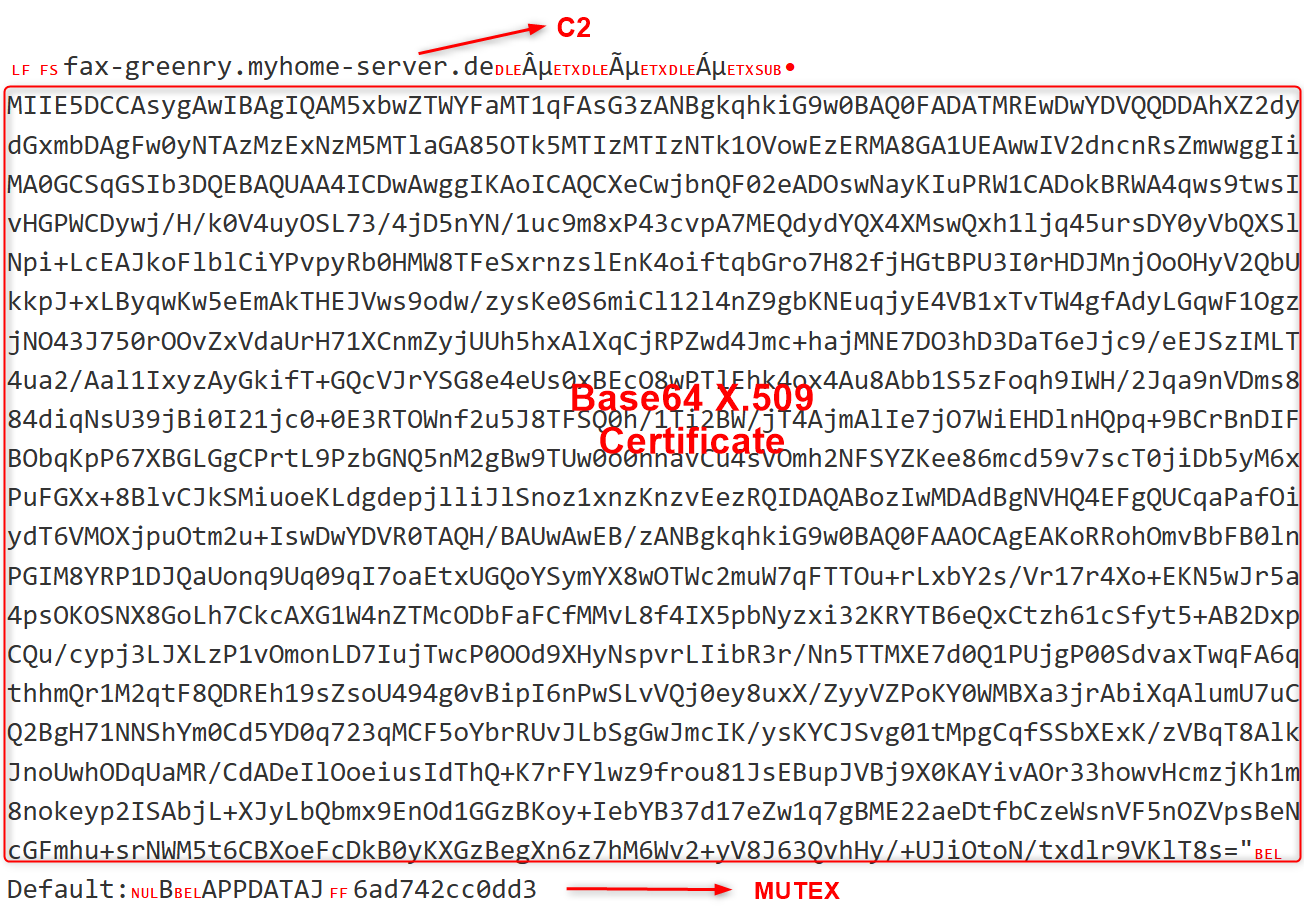
Parsed X.509 Certificate:
Version: 3 (0x02)
Serial number: 1071913861427099792278749970483054303 (0x00ce716f065359815a313d6a140b06df)
Algorithm ID: SHA512withRSA
Validity
Not Before: 31/03/2025 17:39:19 (dd-mm-yyyy hh:mm:ss) (250331173919Z)
Not After: 31/12/9999 23:59:59 (dd-mm-yyyy hh:mm:ss) (99991231235959Z)
Issuer
CN = Wggrtlfl
Subject
CN = Wggrtlfl
Fingerprints
MD5: 3de14ad7e90355527282d3da369815a2
SHA1: 9add49745b6fb5002aa89f79ef549f3bfaa8203d
SHA256: cbbda2edde38162e49f7578512c015640392342a26ea0e5cd90705bb66a7ba81
Public Key
Algorithm: RSA
Length: 4096 bits
Modulus: <Redacted Included in IOCs>
Exponent: 65537 (0x10001)
Certificate Signature
Algorithm: SHA512withRSA
Signature: <Redacted Included in IOCs>
Extensions
subjectKeyIdentifier :
0aa68f69f3a2c9d4fa54c3978e9b8eb66daef88b
basicConstraints CRITICAL:
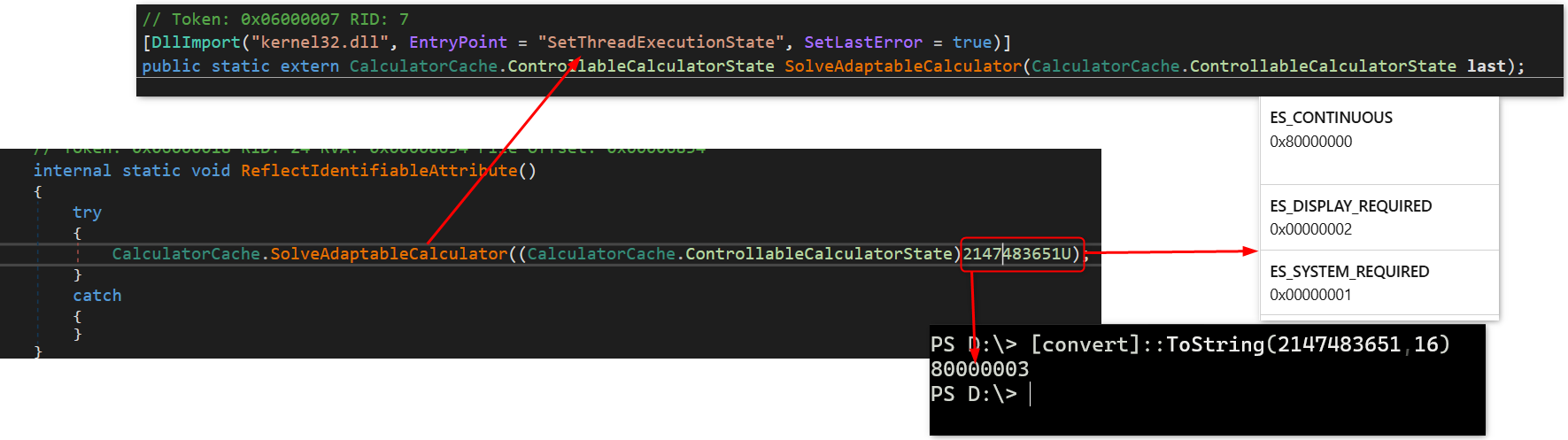
cA=trueThe malware uses the SetThreadExecutionState API with the flags : ES_CONTINUOUS, ES_SYSTEM_REQUIRED, and ES_DISPLAY_REQUIRED (0x80000003 ). This informs the system that the thread is in use, preventing the system from sleeping or turning off the display.
Upon establishing a connection, the malware collects and sends a wealth of information to the Command and Control (C2) server, including:
The malware specifically targets Chrome extensions related to crypto wallets:
These extensions are checked across the following Chromium-based browsers:
Chromium, Chrome, Brave, Edge, QQBrowser, ChromePlus, Iridium, 7Star, CentBrowser, Chedot, Vivaldi, Kometa, Elements, Epic Privacy, Uran, Sleipnir5, Citrio, Coowon, liebao, QIP Surf, Orbitum, Dragon, Amigo, Torch, Comodo, 360Browser, Maxthon3, K-Melon, Sputnik, Nichrome, CocCoc, Chromodo, AtomIn addition to targeting browser extensions, the malware scans the system for desktop cryptocurrency applications. It specifically searches for installation and data folders belonging to messaging apps like Telegram and cryptocurrency wallets such as Ledger Live, Exodus, and Atomic Wallet.
This PureRAT infection closely resembles the tactics described by Fortinet in their article on PureHVNC. After gathering all the specified information including system details, hardware fingerprints, user data, and crypto wallet extensions, the malware sends this data to the command and control (C2) server.
The malware then awaits further instructions, which typically include loading additional plugins for expanded functionality. Unfortunately, we were unable to capture any plugin payloads during our investigation.
What can you learn from this TRU Positive?
- Threat actors often use a sense of urgency and impersonation like calling and posing as a client to trick users into opening or running files. Always verify unexpected requests, especially if they involve downloading or executing files.
- File extensions can be hidden by default in Windows, making double-extension tricks (like pdf.exe) harder to spot.
- Legitimate applications can be abused to run malicious code (side-loading). Keep your security software up to date and consider using Endpoint Detection and Response (EDR) solutions for better protection.
- Be cautious with links from cloud storage services, even if they look legitimate. Always double-check the source before clicking or downloading files.
Recommendations from the Threat Response Unit (TRU)
- Enable the display of file extensions in Windows settings. This helps users spot double extension tricks (like pdf.exe), making it harder for attackers to disguise malicious files.
- Implement a Phishing and Security Awareness Training (PSAT) program that educates and informs your employees on the risks associated with downloading software from unofficial sources.
- Use a Next-Gen AV (NGAV) or Endpoint Detection and Response (EDR) solution to detect and contain threats.
Indicators of Compromise
- Indicators of Compromise can be found here.
References
- https://www.fortinet.com/blog/threat-research/purehvnc-deployed-via-python-multi-stage-loader
- https://github.com/CarlosG13/Process-Hypnosis-Debugger-assisted-control-flow-hijack
- https://hshrzd.wordpress.com/2025/01/27/process-hollowing-on-windows-11-24h2/
- https://github.com/holly-hacker/EazFixer
- https://github.com/SychicBoy/NETReactorSlayer
To learn how your organization can build cyber resilience and prevent business disruption with eSentire’s Next Level MDR, connect with an eSentire Security Specialist now.
GET STARTEDABOUT ESENTIRE’S THREAT RESPONSE UNIT (TRU)
The eSentire Threat Response Unit (TRU) is an industry-leading threat research team committed to helping your organization become more resilient. TRU is an elite team of threat hunters and researchers that supports our 24/7 Security Operations Centers (SOCs), builds threat detection models across the eSentire XDR Cloud Platform, and works as an extension of your security team to continuously improve our Managed Detection and Response service. By providing complete visibility across your attack surface and performing global threat sweeps and proactive hypothesis-driven threat hunts augmented by original threat research, we are laser-focused on defending your organization against known and unknown threats.