The toolkit of a Security Operations Center (SOC) Analyst should include a wide variety of tools and resources; sandboxes, virtualized browsers, and the odd Cyber Chef recipe or two. But prime of all should be the tools and resources that don't need to be updated, built, or have a daily quota (Looking at you, VirusTotal).
Yes, I am talking about a cat's worst enemy – "curiosity". But for a SOC analyst, curiosity is their best friend.
A great SOC Analyst needs to be curious. When performing any threat investigation, regardless of its source, the analyst needs to challenge the information they are presented with. They should never take any evidence at face value, and they should be undeterred until they are fully satisfied that an event is truly signaling a threat or is benign, and the investigation can be closed out.
This brings us to "caultonconsulting[.]com". eSentire's 24/7 Cyber SOC Analysts, including myself, were alerted to the domain and that it was potentially masquerading as a phishing domain. However, when we initially scanned the URL with VirusTotal, VT did not flag that the domain had a bad reputation or give any indication that the domain was malicious.
When navigating to the domain, it appeared perfectly legitimate. There were no apparent signs that the domain was malicious. Web visitors weren't immediately presented with a login page meant to phish their credentials, and all the links, within the home page, were all live sub-pages that contained legitimate-looking content.
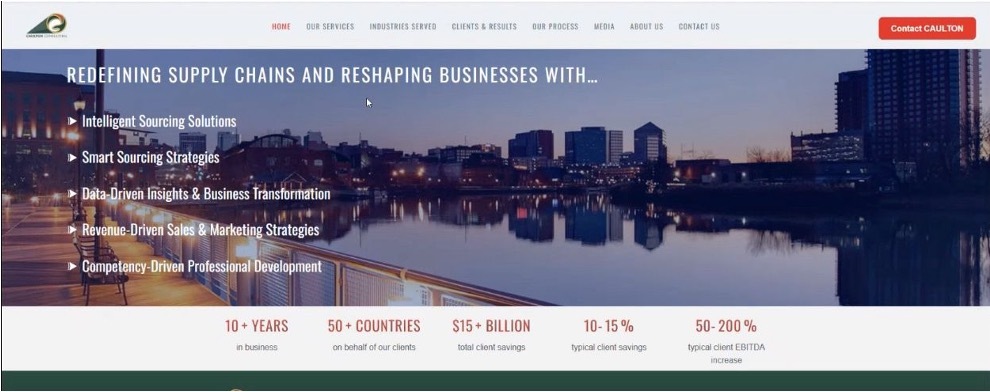
By all accounts, the Caulton Consulting website was a benign, legitimate domain. But this was not enough proof for eSentire's SOC Analysts, and they were not confident that the alert was a false positive. They kept asking themselves, "Why were we alerted to this domain if it was perfectly legitimate?"
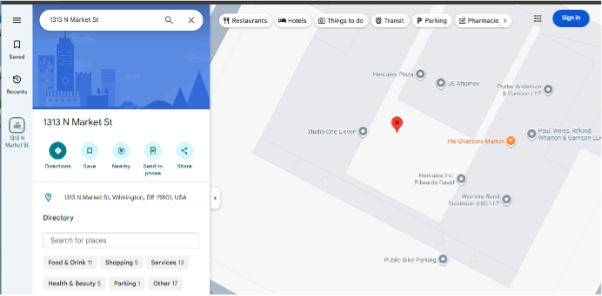
This curiosity led us to dig deeper, and we wanted to verify if this Caulton Consulting company actually existed. We began by searching for the address of the company and found there was no record of it in Google.
This further piqued our interest, so we directed our attention to the executives listed on the organization's website to confirm if they were, in fact, real. We began with the man listed as Caulton Consulting's Founder and Managing Partner, Wyatt Julian Caulton, and focused our investigation on him.
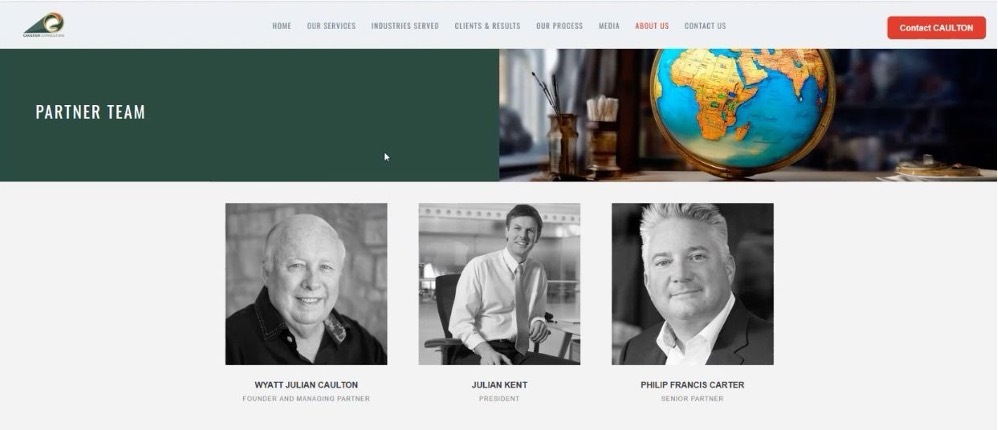
We copied Wyatt Julian Caulton's image, and after a reverse Google image search, the results showed that Caulton Consulting Founder and Managing Partner, Wyatt Julian Caulton, was actually a man named "Pastor Bob Phillips," who formerly resided in Iowa, served as the pastor of Heartland Church and passed away in April of 2017.

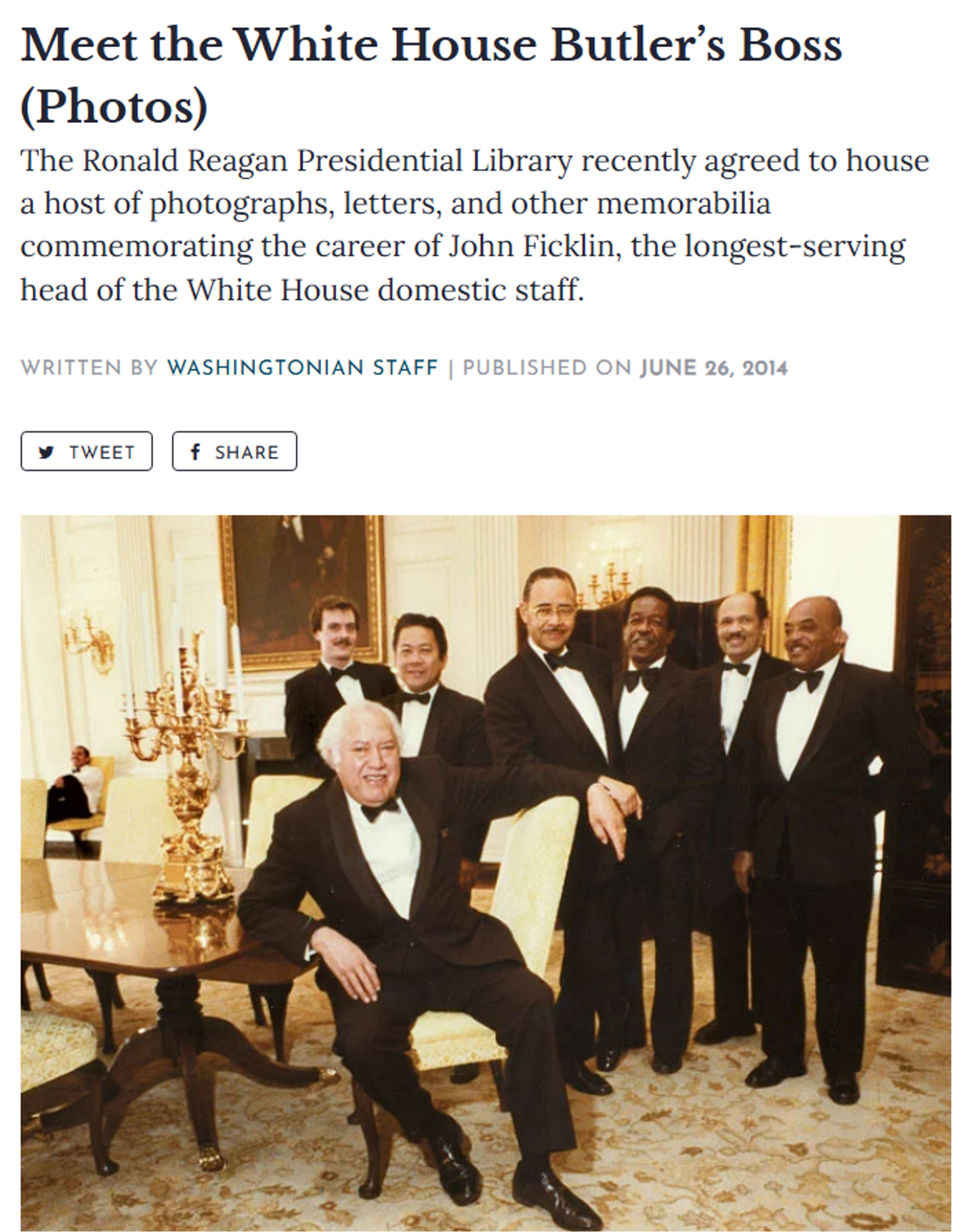
Continuing to review the consulting firm's "About Us" page on their website displays a picture of who Caulton Consulting states are the firm's other founding members.
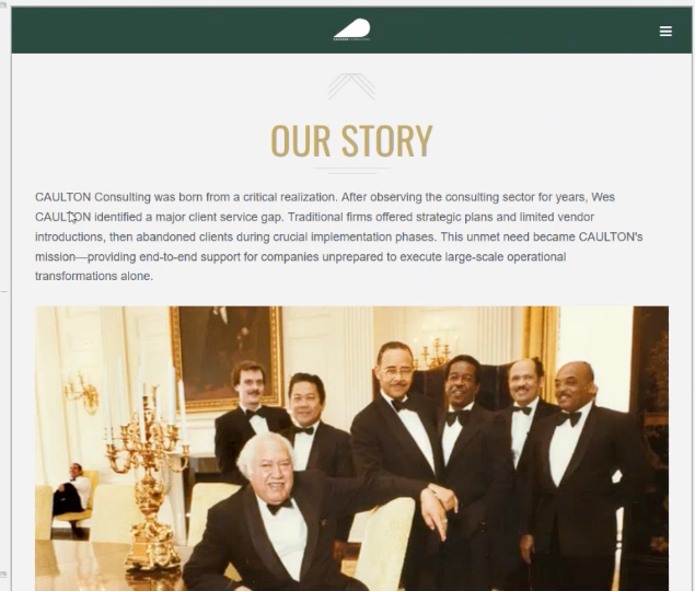
But after another Google image search, we identified that Figure 5 was a picture of John Ficklin and his staff. Ficklin was formerly the White House' top butler (officially referred to as maître d). He worked in the White House for 44 years and was the longest-serving head of the White House household staff. The picture appeared in a 2014 news article about Ficklin in the Washingtonian. Figure 6.
Further investigation into the domain would undoubtedly uncover more fabricated information. Thus, our Analysts tagged the domain as malicious.
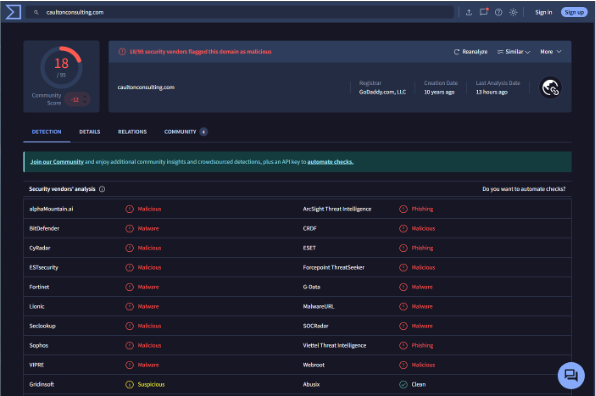
Interestingly, a few days after the SOC Analysts added Caulton Consulting to eSentire's global IP blocklist, 18 cybersecurity vendors flagged the website as being malicious, with some security firms identifying it as a phishing website or identifying it as a site distributing malware.
The Caulton Consulting domain also caught the attention of cybersecurity solutions provider, Check Point Software Technologies, who published a comprehensive report on the threat campaign associated with the domain on August 26, 2025.
Check Point found that the threat actors behind the domain were phishing their victims by visiting the website of each targeted organization and pretending to be a representative of a legitimate company interested in doing business with the potential victim company.
The threat actors filled out the targets' "Contact Us" form on their website. It was a clever lure because what company wouldn't want to respond to a potential business lead? The campaign was sophisticated and had many moving parts. The threat actors used multiple domains and websites in their attacks but once exposed the Caulton Consulting domain, and its counterparts, were taken down.
The important takeaway from this report is that none of the information about Caulton Consulting being a malicious domain was available at the time of eSentire's initial investigation.
This further validates that curiosity is a vital skill for a SOC Analyst to possess. It can be the differentiating factor between a security alert being determined as a false negative or a true positive.
Had our investigating analyst not given the domain a second look, because of the lack of malicious indicators at the time and the domain not being flagged as malicious, we would have missed a very probable phishing attack.
Instead, the Analyst's curiosity overcame any doubt, they challenged the evidence, and in doing so protected not just one eSentire customer but potentially many others.
Stay curious, my friends!
References
- Check Point Analysis: https://research.checkpoint.com/2025/zipline-phishing-campaign/
- VirusTotal: https://www.virustotal.com/gui/domain/caultonconsulting.com
To learn how your organization can build cyber resilience and prevent business disruption with eSentire’s Next Level MDR, connect with an eSentire Security Specialist now.
GET STARTEDABOUT THE AUTHOR

Adem Keranovic SOC Team Lead
Adem Keranovic is a Technical Team Lead, within the Tier 3 team in eSentire’s Security Operations Center (SOC), responsible for serving as a subject matter experts across eSentire’s suite of services, and acting as the primary point of technical escalation within the SOC. Adem began his career in cybersecurity at eSentire in 2015 as a SOC Analyst, later joining the Customer Care team as a Technical Lead. Adem joined Telus, helping to modernize their Threat Intelligence service, later rejoining eSentire in 2021. Since his return, Adem has been involved in launching every new service and product eSentire offers, acting as the SOC representative during each deployment, in addition to helping develop several SOC support initiatives. Adem obtained his Bachelor's Degree in Criminology and his Master's Degree in Infrastructure Protection and International Security from Carleton University, and also studied Network and Systems Security at George Brown College, where he obtained a Post Graduate Diploma in Information Technology.